The Fortress of iPhone’s Security Features
Apple’s iPhone stands as a bastion of digital security, integrating advanced technology to safeguard user data. Each device is fortified with encryption, Touch ID, and Face ID, forming a robust shield against unauthorized access. Regular iOS updates further strengthen this defense, patching vulnerabilities and enhancing security protocols.
Staying Vigilant in a Digital World
In an era where cyber threats are ever-evolving, understanding and utilizing iPhone’s security settings is crucial. Users must be aware of the potential risks and the importance of maintaining their device’s security. Regularly checking settings, being cautious with app downloads, and staying informed about the latest security trends are key practices in ensuring the safety of personal information.
Apple’s commitment to security, coupled with user vigilance, creates a formidable barrier against digital threats. By leveraging built-in security features and adopting cautious digital habits, iPhone users can significantly reduce the risk of falling victim to cyber attacks. This proactive approach is essential in navigating the complexities of today’s digital landscape, where security is not just a feature, but a necessity.
Understanding How iPhones Can Be Compromised
Despite the robust security measures of iPhones, they are not immune to hacking. Knowledge of common hacking methods is essential for iPhone users to protect their devices effectively.
Common Hacking Methods Targeting iPhones
Phishing attacks are a prevalent threat, where hackers trick users into revealing sensitive information through deceptive emails or messages. Malicious software, or malware, can also infiltrate iPhones, often disguised as legitimate apps. These programs can steal data or damage the device’s functionality. Additionally, hackers can exploit software vulnerabilities, particularly in older iOS versions that lack the latest security updates.
Recognizing the Risks of Public Networks and Jailbreaking
Using public Wi-Fi networks exposes iPhones to potential hacks. These networks often lack proper security, making it easier for hackers to intercept data. Another significant risk is jailbreaking, which involves removing software restrictions imposed by iOS. While it allows for greater customization, jailbreaking also removes critical security layers, leaving the iPhone vulnerable to various threats, including unauthorized access and malware.
By understanding these common threats and their consequences, iPhone users can take proactive steps to safeguard their devices. Being cautious with network connections, avoiding jailbreaking, and staying informed about the latest security updates are critical measures in maintaining iPhone security.
Signs Your iPhone Might Be Hacked
Detecting a hacked iPhone involves spotting changes in its behavior and usage that are out of the ordinary. Being aware of these signs can help in taking timely action to secure your device.
Unusual Activity and Performance Issues
A hacked iPhone may exhibit abnormal behavior such as apps crashing frequently, battery draining faster than usual, or the phone overheating. These symptoms can indicate that malicious software is running in the background. Slow response times and unexpected restarts are also red flags. Monitoring for these changes is crucial in identifying potential security breaches.
Unauthorized Charges or Messages
Check for inexplicable charges on your accounts linked to the iPhone. These could be in-app purchases or subscriptions you didn’t authorize. Also, be alert for strange messages sent from your device. These could be attempts by hackers to reach your contacts. Regularly reviewing your billing statements and message history can help in early detection of these anomalies.
Staying vigilant for these signs is key in recognizing if your iPhone has been compromised, enabling you to take swift action to protect your data and privacy.
Checking iPhone Settings for Hacks
Regularly reviewing your iPhone’s settings can help you identify signs of hacking. Being familiar with what each indicator means is crucial for maintaining your device’s security.
Specific Settings to Inspect
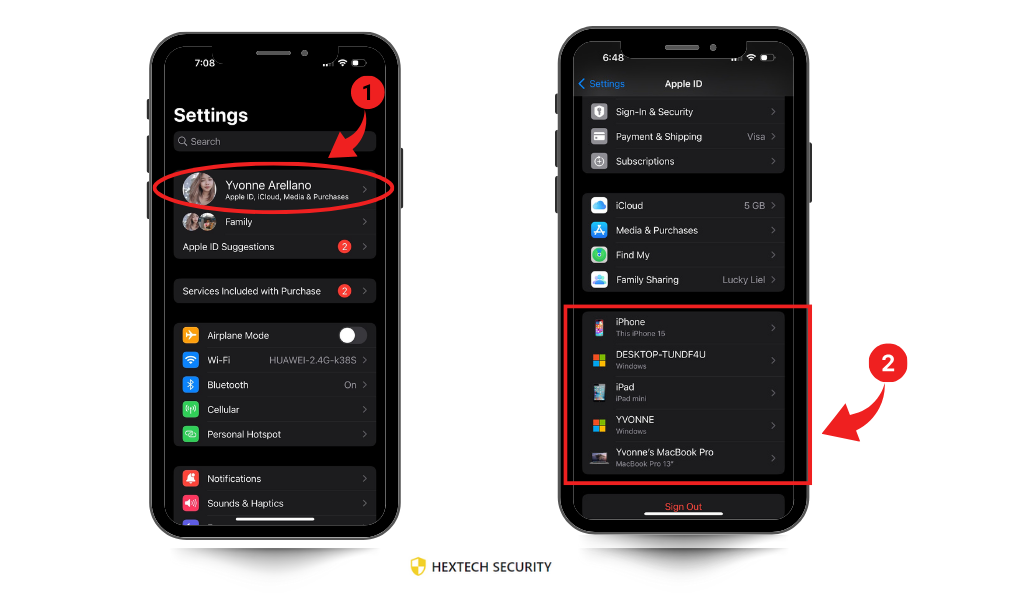
- Apple ID Connections: Navigate to ‘Settings > Apple ID’ to check for unknown devices.
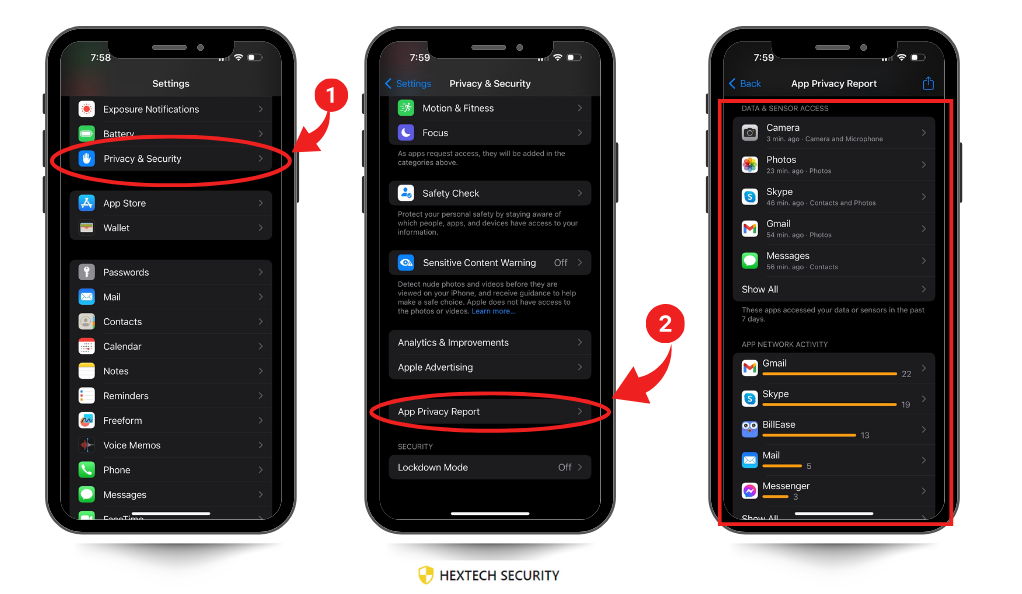
- App Privacy Settings: Go to ‘Settings > Privacy and Security > App Privacy Report’ for app data access review.
- Battery Health: Inspect ‘Battery Health’ for unusual battery drain.
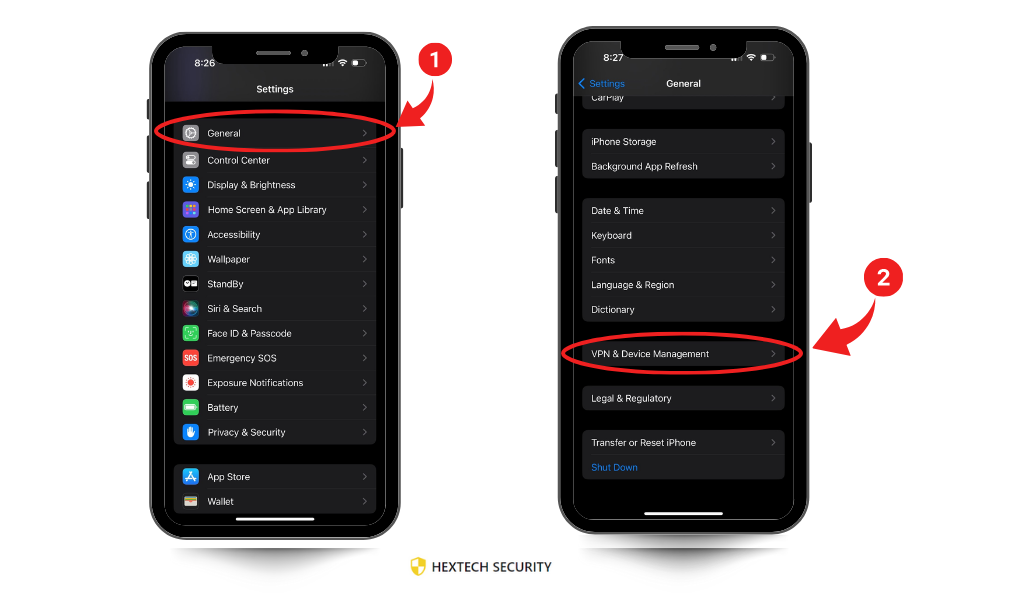
- Installed Profiles: Check ‘Settings > General > Profiles & Device Management’ for unrecognized profiles.
How to Interpret Various Settings Indicators
- Unknown Devices on Apple ID: If you find devices connected to your Apple ID that you don’t recognize, it could mean someone else has access to your account. This requires immediate action like changing your Apple ID password and reviewing account security.
- Excessive App Permissions: Apps with access to sensitive data (like location, contacts, or camera) which don’t require it for functionality could be a red flag. Review and revoke unnecessary permissions to safeguard your personal information.
- Unusual Battery Drain: A significant and unexplained drop in battery health could indicate hidden processes running in the background, possibly due to malicious software. Keep an eye on battery usage by apps, especially those you don’t use frequently.
- Unrecognized Profiles: The presence of configuration profiles that you didn’t install can be a sign of a compromised device. These profiles can control and monitor your device without your consent. Remove any suspicious profiles immediately and consider resetting your device to factory settings if needed.
Understanding and interpreting these indicators effectively can help in the early detection of security issues, allowing you to take appropriate measures to protect your iPhone from potential hacks. Regular vigilance is key to ensuring the safety and privacy of your personal data.
Advanced Security Features in iOS
Apple’s continuous advancements in iOS security play a pivotal role in safeguarding iPhones against evolving cyber threats. Staying informed about these features is essential for users to maximize their device protection.
Overview of Latest iOS Security Updates
The latest iOS updates have introduced enhanced security measures. These include improved data encryption, stronger Wi-Fi privacy settings, and advanced tracking prevention in Safari. Apple has also focused on securing Face ID and Touch ID with sophisticated biometric data protection, ensuring that personal identity information remains secure. Additionally, the App Store now provides more transparency about app data usage, helping users make informed decisions about their privacy.
How These Features Protect Your iPhone
These updated features serve multiple protective functions. Enhanced encryption safeguards your data from unauthorized access, even if your device is lost or stolen. Improved privacy settings in Wi-Fi and Safari prevent hackers from tracking your online activities. The fortified security in biometric features like Face ID and Touch ID ensures that only you can access your device, making it difficult for intruders to gain entry. The transparency in app data usage allows you to control how much personal information apps can access and use.
By leveraging these advanced security features in iOS, users can significantly fortify their iPhones against potential cyber attacks, ensuring a safer and more secure digital experience.
Steps to Take if Your iPhone is Compromised
Addressing a security breach on your iPhone promptly can significantly reduce the risks and help in restoring your device’s security.
Immediate Actions to Secure Your Device
- Change Apple ID Password: Immediately update your Apple ID password to block unauthorized access.
- Update Other Sensitive Passwords: Change passwords for other essential accounts accessed through your phone.
- Disconnect from Unfamiliar Networks: Disconnect from suspicious Wi-Fi networks and disable Bluetooth.
- Run Antivirus Scan: Conduct a scan using a trusted antivirus app to detect and eliminate malware.
- Remove Suspicious Apps and Content: Uninstall any recently downloaded apps or content that seem suspicious.
- Backup and Restore: Backup important data, then reset your iPhone to factory settings to remove potential threats.
When to Seek Professional Help
If you’re unable to manage the issue, notice unauthorized financial transactions, or suspect identity theft, contact professional cybersecurity services. Additionally, for issues specific to your iPhone, reach out to Apple Support:
- Visit the Apple Support Website: Go to support.apple.com for various support options.
- Using the Apple Support App: Download the Apple Support app from the App Store, log in with your Apple ID, and follow the prompts to find a solution or contact support.

- Call Apple’s Helpline: Dial Apple’s customer service number (find the number specific to your region on the Apple website).
- In-Person Assistance: Visit an Apple Store or an authorized Apple service provider.
Seeking expert assistance in these scenarios is crucial for comprehensive resolution and to protect your digital identity from further compromise.
Preventing Future Hacks: Best Practices
To safeguard your iPhone against future hacks, adopting best practices in digital security is essential. These practices not only protect your device but also your personal information.
Regular Updates and Security Measures
Keeping your iPhone updated is crucial. Regularly install the latest iOS updates, as they often include security patches and enhancements. Utilize strong, unique passwords for your Apple ID and other accounts. Enable two-factor authentication for an additional layer of security. Regularly review app permissions and uninstall apps you no longer use. Also, consider using a reputable VPN, especially when connecting to public Wi-Fi networks, to secure your online activities.
Educating Yourself About Digital Threats
Stay informed about common cyber threats and how they operate. This knowledge can help you recognize potential risks and avoid falling victim to scams. Follow reputable tech news sources or subscribe to cybersecurity newsletters. Participating in online security awareness programs can also significantly enhance your understanding of digital threats and how to protect against them.
By implementing these proactive measures, you significantly reduce the risk of future hacks, ensuring your iPhone and personal data remain secure.
Conclusion
Understanding the nuances of iPhone security is vital in today’s digital age. By recognizing signs of hacking, such as unusual activity and unauthorized charges, and knowing how to inspect settings for anomalies, users can take prompt action against potential breaches. The importance of utilizing the advanced security features in iOS and staying updated with the latest versions cannot be overstated. In instances where a device is compromised, immediate steps, coupled with professional support when necessary, are key. Lastly, adopting best practices for regular updates and educating oneself about digital threats forms a comprehensive approach to safeguarding iPhones against future hacks, ensuring both device integrity and personal data protection.








