Email, as one of the earliest forms of digital communication, has undergone significant transformations since its inception in the 1970s. Initially, email systems were confined to closed networks, where security wasn’t a primary concern. However, as the internet expanded and email became a ubiquitous communication tool, the need for robust security measures became evident.
Email, as one of the earliest forms of digital communication, has undergone significant transformations since its inception in the 1970s. Initially, email systems were confined to closed networks, where security wasn’t a primary concern. However, as the internet expanded and email became a ubiquitous communication tool, the need for robust security measures became evident.

Table 1: Timeline of Email Evolution and Security Measures
| Year | Email Milestone | Security Measure Introduced |
|---|---|---|
| 1970s | Inception of Email | None |
| 1980s | Expansion of Email Services | Basic Password Protection |
| 1990s | Advent of Commercial Email Services | SSL/TLS Encryption |
| 2000s | Rise of Phishing Attacks | Anti-Phishing Tools & Spam Filters |
| 2010s | Cloud-based Email Services | Two-Factor Authentication |
| 2020s | AI-driven Email Services | Behavioral Authentication Techniques |
The Traditional Password System: A Double-Edged Sword
The most rudimentary form of email security was the password system. It acted as the first line of defense against unauthorized access. However, as cyber threats evolved, it became evident that passwords alone were insufficient.
Limitations of Traditional Password Systems:
- Predictability: Many users often resort to easily guessable passwords, making them vulnerable to brute-force attacks.
- Reuse: A significant number of users reuse passwords across multiple platforms. If one platform is compromised, all accounts with the same password are at risk.
- Phishing Vulnerability: Even strong passwords can be stolen through phishing attacks, where users are tricked into providing their credentials.
- Management Challenges: As the number of online accounts per user grew, remembering unique and complex passwords for each became a challenge, leading to the rise of password managers.
Comparison Table: Traditional Passwords vs. Modern Security Measures
| Criteria | Traditional Passwords | Modern Security Measures |
|---|---|---|
| Strength | Varies (often weak) | Strong (with multi-factor auth) |
| Ease of Use | Moderate | High (biometrics, single sign-on) |
| Vulnerability to Phishing | High | Reduced (with behavioral auth) |
| Management | Challenging | Simplified (with password managers) |
The Challenges of Password-Based Authentication
Email has become an integral part of our daily lives, both professionally and personally. With its widespread use, ensuring the security of email accounts is paramount. However, password-based authentication, the most common method of securing email accounts, presents several challenges.
Common Password Vulnerabilities
Password-based authentication systems are only as strong as the passwords themselves. Over the years, several vulnerabilities associated with password usage have been identified:
- Brute Force Attacks: This involves systematically trying all possible password combinations until the correct one is found. Short and simple passwords are especially susceptible to this type of attack.
- Dictionary Attacks: Here, attackers use a pre-arranged list of words found in dictionaries. Passwords that are actual words or common phrases can be easily cracked using this method.
- Rainbow Table Attacks: Attackers use precomputed tables for reversing cryptographic hash functions. Using unique “salts” with hashes can mitigate this, but not all systems implement them.
- Credential Stuffing: This is when attackers use previously breached username-password pairs to gain unauthorized access to user accounts on various platforms, banking on the fact that many people reuse passwords.
- Keylogging: Malicious software records a user’s keystrokes, capturing passwords as they’re entered.
Table: Common Password Vulnerabilities and Their Countermeasures
| Vulnerability | Description | Countermeasure |
|---|---|---|
| Brute Force | Trying all password combinations | Account lockouts, CAPTCHAs |
| Dictionary Attack | Using common words/phrases | Encourage complex passwords |
| Rainbow Table | Precomputed tables for hash functions | Use of unique “salts” with hashes |
| Credential Stuffing | Using breached username-password pairs | Two-factor authentication |
| Keylogging | Recording keystrokes | On-screen keyboards, encrypted keystrokes |
The Human Factor: Memorability vs. Security
At the heart of the password conundrum is the human factor. Users are often caught in the dilemma of creating passwords that are both memorable and secure.
- Simplicity vs. Complexity: While a password like “123456” is easy to remember, it’s also easily hackable. On the other hand, a password like “j#4!Qz9&” is strong but challenging to recall.
- Password Fatigue: With the increasing number of online accounts, users often experience fatigue, leading to password reuse or the creation of overly simplistic passwords.
- Security Overload: Constant reminders to update passwords, combined with the requirements for special characters, numbers, and varying cases, can overwhelm users.
- Balancing Act: The challenge is finding a balance where users can easily remember their passwords without compromising on security.
Comparison Table: Memorability vs. Security
| Criteria | Memorable Passwords | Secure Passwords |
|---|---|---|
| Complexity | Low | High |
| Length | Short | Long |
| Variety of Characters | Limited | Diverse (symbols, numbers, letters) |
| Frequency of Change | Rare | Regular |
Biometric Authentication for Email Access
In the quest for more secure authentication methods, biometrics has emerged as a promising alternative to traditional password systems. Biometric authentication relies on the unique physiological or behavioral characteristics of an individual. For email access, this means that instead of remembering a password, users can rely on their inherent traits to gain access.
Fingerprint, Facial Recognition, and Voice Patterns
- Fingerprint Authentication: Every individual has a unique fingerprint pattern. Modern devices, equipped with fingerprint scanners, can store and match these patterns to authenticate users. This method is widely adopted in smartphones and laptops.
- Facial Recognition: Using advanced cameras and software, devices can analyze facial features to identify and authenticate users. This technology considers various aspects, including the distance between eyes, nose width, and jawline shape.
- Voice Patterns: Voice biometrics analyzes the unique features of an individual’s voice, such as pitch, tone, and cadence. While less common than fingerprint and facial recognition, it’s gaining traction, especially with the rise of voice-activated devices.

Table: Biometric Methods and Their Features
| Biometric Method | Unique Feature | Common Use Cases |
|---|---|---|
| Fingerprint | Ridge patterns on fingers | Smartphones, Laptops |
| Facial Recognition | Distinct facial features | Smartphones, Security systems |
| Voice Patterns | Pitch, tone, and cadence of voice | Voice assistants, Banking verification |
Pros and Cons of Biometric Systems
Pros:
- Enhanced Security: Biometrics are unique to each individual, making them difficult to replicate or forge.
- Convenience: Users don’t need to remember passwords or carry additional authentication devices.
- Speed: Biometric authentication is often faster than typing a password or PIN.
- Reduced Risk of Phishing: Since there’s no password to steal, the risk associated with phishing attacks is minimized.
Cons:
- Privacy Concerns: Storing biometric data raises concerns about user privacy and potential misuse.
- False Positives/Negatives: No system is perfect. There’s a risk of false acceptances (unauthorized user granted access) or false rejections (authorized user denied access).
- Irrevocability: Unlike passwords, biometrics can’t be changed. If compromised, it poses a permanent risk.
- Hardware Dependency: Biometric authentication requires specific hardware, such as fingerprint scanners or advanced cameras.
Comparison Table: Pros vs. Cons of Biometric Systems
| Criteria | Pros | Cons |
|---|---|---|
| Security Level | High | Risk of data breach |
| User Convenience | High (no need to remember passwords) | Hardware dependency |
| Authentication Speed | Fast | Risk of false positives/negatives |
| Changeability | Not applicable (biometrics are constant) | Irrevocable if compromised |
Multi-Factor Authentication (MFA) for Enhanced Email Security
As cyber threats become more sophisticated, relying solely on passwords, even strong ones, is no longer sufficient. Multi-Factor Authentication (MFA) has emerged as a robust solution to this challenge, adding an extra layer of security to the authentication process.
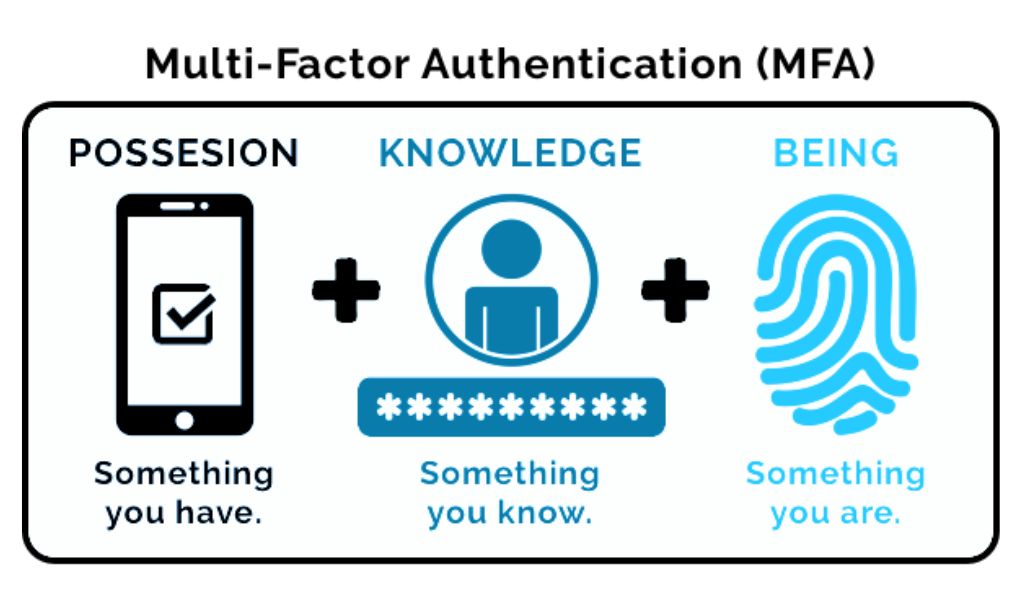
How MFA Enhances Email Security?
MFA works on a simple principle: to verify the identity of a user by requiring multiple forms of verification. The idea is that even if one factor is compromised, the chances of another being breached are minimal, thus ensuring a higher level of security.
- Reduction in Phishing Risks: Even if a malicious actor obtains a user’s password, they would still need access to the second factor, making phishing attacks less effective.
- Protection Against Brute Force: With MFA, even if an attacker guesses a password, they’re halted in their tracks without the second authentication factor.
- Mitigation of Stolen Credentials: Lost or stolen passwords alone are insufficient for account access when MFA is enabled.
- Enhanced User Confidence: Users are assured that their accounts have an added layer of protection, fostering trust in the platform.
Different Types of MFA
- SMS Verification: After entering a password, users receive a one-time code via SMS, which they must enter to gain access. While convenient, this method has vulnerabilities, such as SIM swapping attacks.
- Authenticator Apps: Applications like Google Authenticator or Authy generate time-sensitive codes. Users open the app and enter the displayed code for authentication. This method is considered more secure than SMS as it doesn’t rely on external networks.
- Hardware Tokens: Physical devices, like YubiKey or RSA SecurID, generate codes or can be plugged into a system for authentication. They are not connected to the internet, making them resistant to many types of cyberattacks.
Table: Types of MFA and Their Features
| MFA Type | Description | Security Level |
|---|---|---|
| SMS Verification | One-time code sent via SMS | Moderate (vulnerable to SIM swapping) |
| Authenticator Apps | Time-sensitive codes from an app | High (no external network reliance) |
| Hardware Tokens | Physical device generating codes or for direct connection | Very High (offline, tamper-resistant) |
Behavioral Authentication Techniques: A New Frontier in Email Security
In the ever-evolving landscape of cybersecurity, traditional methods of authentication, even those as advanced as biometrics and MFA, can sometimes fall short. Enter behavioral authentication, a cutting-edge approach that leverages the unique ways in which users interact with their devices and applications.
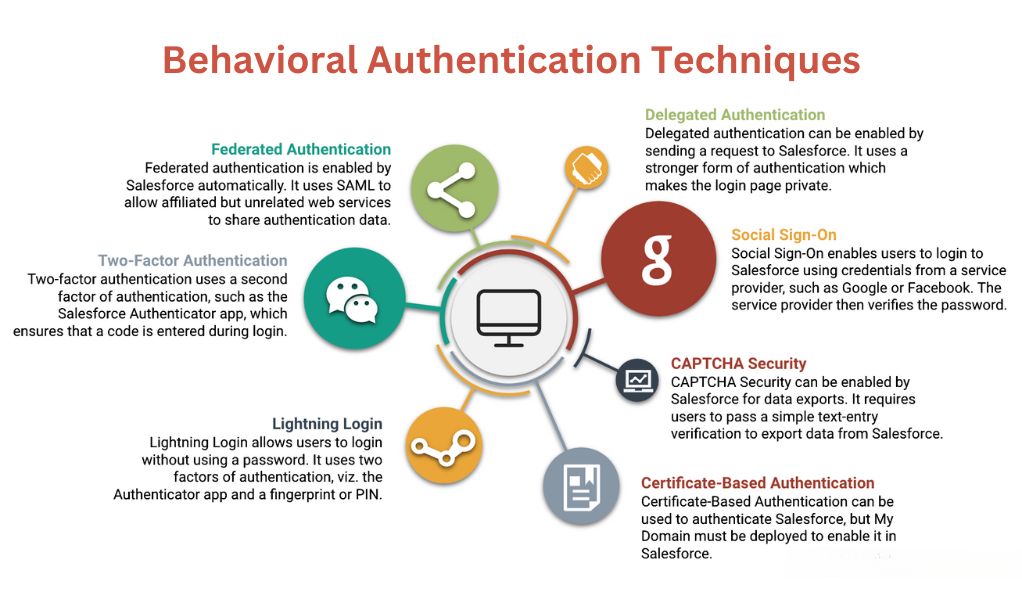
Analyzing User Behavior Patterns for Authentication
Behavioral authentication is rooted in the principle that each individual has a unique way of interacting with digital platforms. These interactions, when analyzed, can serve as a reliable method of verifying a user’s identity. Some key behavioral patterns include:
- Keystroke Dynamics: The rhythm and speed at which a user types can be distinctive. Factors like dwell time (how long a key is pressed) and flight time (interval between pressing two keys) are considered.
- Mouse Movement Patterns: The way a user moves the mouse, the speed of movement, and the pattern of clicks can be unique to individuals.
- Device Interaction: How a user swipes on a touchscreen, the pressure applied, or even the tilt and angle at which they hold their device can be used for authentication.
- Application Usage Patterns: The sequence in which a user accesses apps, the frequency, and the duration can also be indicative of their identity.
The Role of Machine Learning in Behavioral Authentication
Machine learning (ML) plays a pivotal role in the effectiveness of behavioral authentication. Here’s how:
- Continuous Learning: ML algorithms can continuously learn and update a user’s behavior profile, accommodating slight changes in behavior over time.
- Anomaly Detection: By understanding what constitutes ‘normal’ behavior for a user, ML can quickly identify deviations or anomalies, potentially signaling a security threat.
- Reduced False Positives: Traditional systems might flag a user if they enter a correct password too slowly or quickly. ML can adapt to such variances, reducing unnecessary security flags.
- Predictive Analysis: ML can predict potential security breaches by analyzing patterns and comparing them to known breach behaviors.
Table: Machine Learning in Behavioral Authentication
| Feature | Description | Benefit |
|---|---|---|
| Continuous Learning | Adapts to evolving user behavior | Keeps authentication methods up-to-date |
| Anomaly Detection | Identifies deviations from the norm | Quick threat detection |
| Reduced False Positives | Understands minor behavioral variances | Smoother user experience |
| Predictive Analysis | Foresees potential threats | Proactive security measures |
The Role of Encryption in Secure Email Access
In the digital age, where data breaches and cyber-espionage are prevalent threats, the security of email communication has never been more crucial. Encryption stands as a formidable barrier against these threats, ensuring that the content of emails remains confidential and accessible only to the intended recipients.
End-to-End Encryption and Its Importance
End-to-end encryption (E2EE) is a method where the data is encrypted on the sender’s side and only decrypted on the recipient’s side. This ensures that even if the communication is intercepted during transit, the content remains unreadable to unauthorized parties.
Key Benefits of E2EE:
- Confidentiality: Only the sender and the intended recipient can read the email, ensuring the privacy of the communication.
- Protection Against Interception: Even if emails are intercepted, they remain encrypted and, therefore, unreadable.
- Integrity of Data: E2EE ensures that the content of the email hasn’t been altered during transit.
- Trustworthiness: Users can trust the platform more, knowing their communications are secure.
Public and Private Key Systems
The effectiveness of encryption largely hinges on the key management system in place. The public and private key system, also known as asymmetric encryption, is foundational to this.
- Public Key: This is a cryptographic key that can be shared with anyone. It’s used to encrypt data. For emails, this means that anyone can encrypt a message using the recipient’s public key.
- Private Key: This is a secret key that only the owner knows. It’s used to decrypt data. In the context of emails, only the recipient, who possesses the private key, can decrypt and read the email.
How Does It Work?
- A sender encrypts the email using the recipient’s public key.
- The email travels encrypted through the internet.
- Upon reaching the recipient, it’s decrypted using the recipient’s private key.
Table: Public vs. Private Key in Email Encryption
| Key Type | Purpose | Accessibility |
|---|---|---|
| Public Key | Encrypting data | Available to anyone |
| Private Key | Decrypting data | Only available to the key owner |
Future of Email Authentication: Beyond Passwords and Into the Unknown
The realm of email authentication has witnessed a rapid evolution over the past few decades. From rudimentary passwords to sophisticated biometric and behavioral techniques, the journey has been marked by constant innovation. As we look ahead, the trajectory suggests a move towards even more advanced and user-friendly methods of ensuring secure email access.
Moving Towards a Passwordless Future
The limitations of password-based systems, combined with the advancements in technology, are pushing the digital world towards a passwordless future. This shift is not just about enhancing security but also about improving user experience.
Key Features of a Passwordless Future:
- User-Centric: Eliminating the need to remember and manage multiple passwords, making the authentication process more user-friendly.
- Reduced Attack Vectors: Without passwords, common threats like brute force attacks, dictionary attacks, and phishing become irrelevant.
- Adaptive Authentication: Systems will assess various factors, like user behavior, device, location, and more, to determine the authenticity of a login attempt.
- Biometrics and Beyond: Fingerprints, facial recognition, and voice patterns might become the primary methods of authentication, backed by advanced algorithms ensuring accuracy and security.
Potential Innovations on the Horizon
As technology continues to advance, several potential innovations could redefine email authentication:
- Quantum-Resistant Algorithms: With the advent of quantum computing, there’s a need for new cryptographic methods that can withstand quantum attacks. Quantum-resistant algorithms are being developed to address this.
- Continuous Authentication: Instead of a one-time login, systems might continuously monitor and authenticate users based on their behavior during an email session.
- Blockchain-Based Authentication: Leveraging the decentralized and tamper-proof nature of blockchain technology to create a secure and transparent authentication system.
- AI-Powered Risk Assessment: Using artificial intelligence to assess the risk level of each login attempt in real-time, adjusting authentication requirements accordingly.
- Wearable Authentication: Devices like smartwatches or even smart clothing could play a role in authenticating users, leveraging unique biometric or behavioral data.
Table: Traditional vs. Future Email Authentication
| Criteria | Traditional Authentication | Future Authentication |
|---|---|---|
| Primary Method | Passwords | Biometrics, Behavior |
| Security Level | Moderate to High | Very High |
| User Experience | Often Cumbersome | Seamless and Intuitive |
| Adaptability | Static (One-time login) | Dynamic (Continuous authentication) |
Conclusion
The digital landscape of email security and authentication is in a state of dynamic evolution. From the rudimentary days of simple passwords to the promising horizon of passwordless futures, the journey has been marked by innovation, challenges, and adaptability. As cyber threats grow in complexity, so does the need for more robust and user-centric authentication methods. This article has traversed the various facets of email security, highlighting the strengths and limitations of each approach. The future beckons a world where email access is not just secure but also intuitive and seamless. As users and stakeholders in this digital ecosystem, it’s imperative to stay informed, adaptable, and proactive, ensuring that our communication channels remain both efficient and secure in the face of ever-evolving cyber challenges.








