The Internet of Things (IoT) represents a groundbreaking shift in our relationship with technology and our environment. It involves interlinking commonplace items, from kitchen appliances to vehicles, through the internet, enabling them to gather, process, and respond to data. Imagine a world where your fridge can order groceries when you’re running low or a car that schedules its own maintenance. While this interconnectedness offers unparalleled convenience and efficiency, it also introduces significant security concerns. As the number of connected devices multiplies, so does the potential for cyberattacks and data breaches. Ensuring the safety of these devices becomes paramount in harnessing their full potential without risking user privacy or system integrity.
What is IoT?
The Internet of Things (IoT) refers to the network of physical devices, vehicles, home appliances, and other items embedded with sensors, software, and other technologies that enable them to connect and exchange data over the Internet. These devices collect and share data, making our lives more efficient, informed, and connected.
The Growth of IoT
The proliferation of IoT devices has been staggering. According to a report by Statista, the number of connected devices worldwide is expected to jump from 8.74 billion in 2020 to over 30 billion by 2025.
Growth of IoT Devices (in billions)
| Year | Number of Devices |
|---|---|
| 2020 | 8.74 |
| 2021 | 11.31 |
| 2022 | 15.41 |
| 2023 | 20.45 |
| 2024 | 25.12 |
| 2025 | 30.73 |
The Promise of IoT
IoT offers numerous benefits:
- Efficiency and Productivity: Devices can communicate to optimize operations without human intervention.
- Data Collection: Provides insights into user behavior, helping businesses tailor their services.
- Improved Quality of Life: Smart homes can enhance comfort and convenience for residents.
Security Challenges in IoT
However, the rapid expansion of IoT has brought forth a myriad of security challenges:
- Vulnerability to Hacks: Many IoT devices lack robust security features, making them easy targets.
- Data Privacy Concerns: Devices collect vast amounts of personal data, raising privacy issues.
- Lack of Standardization: With numerous manufacturers entering the IoT space, there’s a lack of standard security protocols.
Comparison Table: Traditional Internet Devices vs. IoT Devices
| Feature | Traditional Internet Devices | IoT Devices |
|---|---|---|
| Primary Function | Computing | Specific tasks (e.g., monitoring temperature) |
| User Interaction | High (e.g., laptops) | Low (e.g., smart bulbs) |
| Security Features | Robust (firewalls, antivirus) | Often minimal |
| Software Updates | Regular | Infrequent or non-existent |
Addressing the Security Challenges
To harness the full potential of IoT without compromising security:
- Standardization: The rapid proliferation of IoT devices underscores the urgent need to implement universal security standards. Such standards would ensure consistent protection across all devices, regardless of the manufacturer. By adopting a unified approach to security, we can safeguard user data and maintain the integrity of interconnected systems, promoting trust and reliability in the IoT ecosystem.
- Education: Educating consumers about potential risks associated with IoT devices is crucial. By raising awareness, users can make informed decisions and adopt best practices. This not only involves understanding the vulnerabilities but also learning how to use devices securely. Proper guidance can prevent data breaches and ensure that technology serves its purpose without compromising user safety.
- Innovative Solutions: Utilizing cutting-edge technologies such as artificial intelligence (AI) and blockchain can significantly bolster IoT security. AI can detect and counteract threats in real-time, while blockchain offers transparent and tamper-proof data storage. By integrating these technologies, we can create a more robust defense mechanism, ensuring that IoT devices operate securely and efficiently in interconnected ecosystems.
Blockchain: A Primer
In the digital age, where data is the new gold, ensuring its authenticity and security is paramount. Enter blockchain, a technology that promises to revolutionize the way we perceive data integrity and security.
Understanding the Basics of Blockchain Technology
At its core, a blockchain is a distributed ledger or database, shared across a network of computers, often referred to as nodes. What makes it unique is its structure. Data in a blockchain is stored in blocks, and each block contains a record of transactions. Once a block is filled with this data, a new block is created, forming a chain of blocks – hence the name, blockchain.
One of the defining features of blockchain is its decentralization. Unlike traditional databases, such as a SQL database, where there’s a central entity controlling the data, in a blockchain, every participant (node) has access to the entire database and its complete history. No single participant can alter past transactions, making it inherently secure.
How Blockchain Ensures Data Integrity and Security
- Immutable Records: Once data is added to the blockchain, it becomes permanent and cannot be altered or deleted. This immutability is ensured by cryptographic hashes. Each block has a unique code (hash) and the hash of the previous block. Any change in the block’s information would change its hash, alerting the system to potential foul play.
- Decentralization: Since there’s no central authority, it’s nearly impossible for a single entity to take control of or alter the blockchain. Every transaction is verified by multiple nodes, ensuring that only valid transactions get recorded.
- Transparency: All transactions are visible to every user, ensuring transparency in the system. However, the identity of the person behind each transaction can remain anonymous.
- Consensus Algorithms: These are protocols used to achieve agreement on a single data value among distributed processes or systems. Popular methods include Proof of Work (PoW) and Proof of Stake (PoS). They ensure that all transactions are genuine and prevent double-spending.
Blockchain’s Role in IoT Security
The Internet of Things (IoT) has ushered in an era of interconnected devices, streamlining operations and enhancing user experiences. However, this interconnectivity also introduces vulnerabilities. Blockchain, with its inherent security features, offers promising solutions to these challenges.
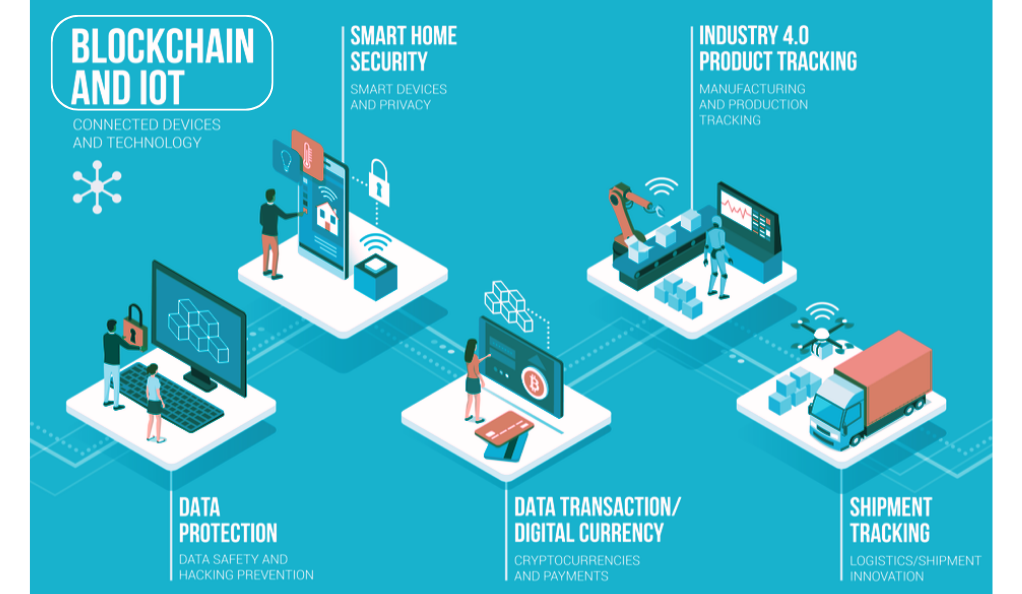
How Blockchain Can Prevent Data Tampering in IoT Devices
IoT devices constantly transmit and receive data. This data flow, if not secured, can be intercepted, altered, or misused. Blockchain’s decentralized nature and cryptographic mechanisms come into play here:
- Immutable Transactions: Once a device’s data is recorded on the blockchain, it’s permanent. This means that any data sent from an IoT device, once verified and added to the blockchain, cannot be tampered with. If an external actor tries to alter this data, the discrepancy becomes evident when cross-referenced with the blockchain’s records.
- Distributed Ledgers: Unlike centralized systems where a single point of failure can compromise the entire network, blockchain’s data is spread across numerous nodes. Each node verifies the data, ensuring that only genuine information is recorded. This distributed nature makes it challenging for hackers to alter data across all nodes simultaneously.
Locking Access to IoT Devices Using Blockchain
Blockchain can also control who accesses an IoT device and when:
- Smart Contracts: These are self-executing contracts with the terms of the agreement directly written into code. In the context of IoT, smart contracts can be used to set conditions for device access. For instance, a smart lock could be programmed to open only when verified by a blockchain-based identity.
- Decentralized Identity Verification: Traditional security measures often rely on centralized servers to verify identities, making them vulnerable to attacks. Blockchain offers a decentralized approach. Each device can have its unique blockchain-based identity. When access is required, the system can verify this identity on the blockchain, ensuring only authorized users gain entry.
- Device-to-Device Communication: In a blockchain-enabled IoT network, devices can communicate directly without needing a central server. This peer-to-peer communication, backed by blockchain’s verification mechanisms, ensures that devices only act on authenticated requests.
In essence, blockchain’s integration into the IoT landscape offers a robust shield against potential security threats. By ensuring data integrity and controlling device access, blockchain paves the way for a more secure and trustworthy IoT ecosystem.
Real-world Implementations and Case Studies
The theoretical advantages of integrating blockchain with IoT are evident, but real-world implementations provide tangible proof of its potential. Several enterprises have embarked on this journey, with some notable examples being Hyundai’s HDAC and the ChainAnchor framework.
Hyundai’s Blockchain Initiative: HDAC (Hyundai Digital Access Currency)
Hyundai, a global automotive giant, recognized the transformative potential of blockchain in enhancing IoT security and took a pioneering step with its blockchain initiative, HDAC.
- Purpose and Vision: HDAC was developed as a blockchain solution tailored for IoT scenarios. It aims to provide a secure and seamless platform for various IoT services, ensuring data integrity, privacy, and device interoperability.
- Technical Features: HDAC operates on a permissioned private network, ensuring faster transaction speeds and enhanced security. It employs a unique Proof-of-Work (PoW) mining algorithm, ePoW, which curtails mining monopolization, ensuring a more democratic and decentralized system.
- Real-world Application: Beyond just vehicles, Hyundai envisions HDAC’s application in smart homes and cities. For instance, a smart home system powered by HDAC could autonomously manage energy consumption, security protocols, and even facilitate machine-to-machine transactions, like a refrigerator ordering groceries.
ChainAnchor: A Blockchain-based IoT Framework
ChainAnchor represents a leap in IoT security frameworks, leveraging the power of blockchain.
- Objective: Developed with insights from MIT Connection Science, ChainAnchor is designed to address IoT device security at multiple levels, from device activation to data access.
- Framework Features: ChainAnchor introduces a multi-layered security approach. It incorporates activation and security layers supported by device manufacturers, data providers, and independent third parties. This ensures that unauthorized devices are kept out, and any compromised device can be swiftly isolated and removed from the network.
- Innovative Solutions: One of ChainAnchor’s standout features is its provision for safely selling and transferring devices. When an IoT device changes hands, its identity and access can be securely updated on the blockchain, ensuring the new user inherits a clean slate without any lingering security threats.
Challenges in Integrating Blockchain with IoT
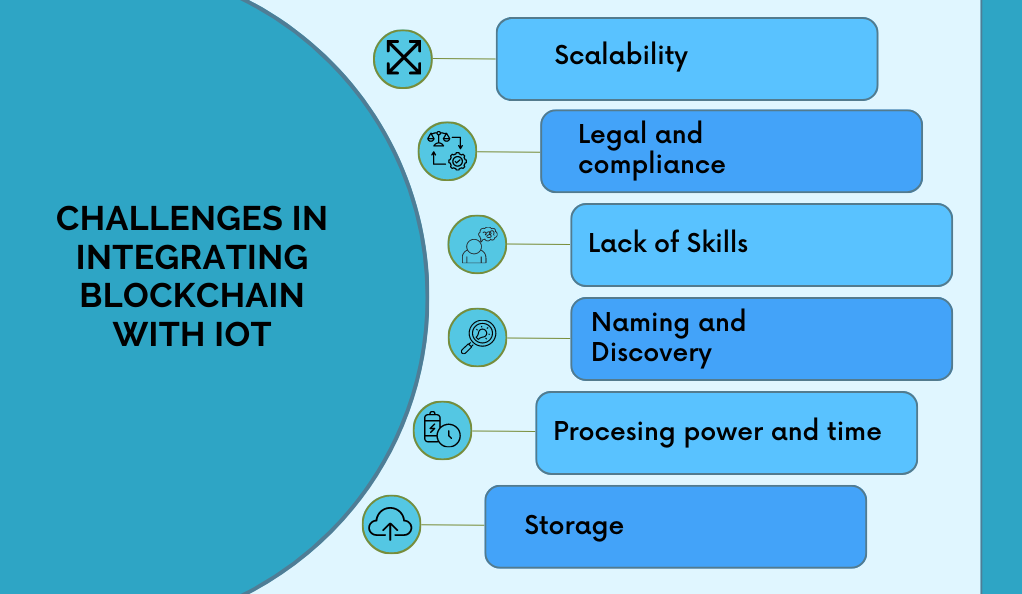
While the integration of blockchain with IoT promises a myriad of benefits, it’s not without its challenges. The fusion of these two groundbreaking technologies brings forth certain complexities and hurdles that need to be addressed for their seamless coexistence.
The Processing Power Required for Blockchain Mining
- Energy-Intensive Operations: Blockchain, especially networks using Proof-of-Work (PoW) consensus algorithms like Bitcoin, requires significant computational power to validate and add transactions to the ledger. This process, known as mining, is energy-intensive and can be counterproductive in an IoT setting where devices are often designed to be energy-efficient.
- IoT Device Limitations: Many IoT devices, such as sensors or smart bulbs, are designed for specific, low-power tasks. Asking these devices to participate in blockchain mining could quickly deplete their resources, reducing their operational lifespan and efficiency.
- Scalability Concerns: As the number of IoT devices continues to grow exponentially, the amount of data they produce will also surge. Processing this vast amount of data using blockchain can strain the network, leading to potential bottlenecks and reduced transaction speeds.
Vulnerabilities in Blockchain When a Group Controls a Significant Portion of the Network’s Mining Hashrate
- 51% Attack: One of the most discussed vulnerabilities in blockchain is the potential for a “51% attack.” If a single entity or a colluding group gains control of more than half of the network’s mining hashrate, they can potentially double-spend coins, halt transactions, and even alter the historical record of the blockchain.
- Centralization Risks: The very essence of blockchain is its decentralized nature. However, if a significant portion of the network’s mining power is controlled by a few, it contradicts this principle, leading to centralization risks. This can undermine trust in the system and make it more susceptible to external pressures or regulatory interventions.
- IoT Implications: In an IoT context, if a group gains dominance over the blockchain network, they could potentially manipulate device data, disrupt device operations, or even gain unauthorized access to devices, posing severe security and privacy threats.
The Future of Blockchain and IoT: What Lies Ahead
The convergence of Blockchain and the Internet of Things (IoT) is poised to redefine the digital landscape. As we stand on the cusp of this technological revolution, it’s essential to explore the potential outcomes and the trajectory of their combined evolution.

The Potential of a Blockchain IoT Security System
- Decentralized Trust: At the heart of blockchain is the principle of decentralized trust. By integrating this with IoT, devices can operate based on consensus, ensuring that data is not only accurate but also tamper-proof. This eliminates the need for central intermediaries, reducing potential points of failure.
- Enhanced Data Integrity: Every piece of data on the blockchain is time-stamped and linked to the previous one. For IoT, this means a continuous, unalterable record of device data, from sensor readings to user interactions, ensuring full traceability.
- Smart Contracts in Action: Imagine an IoT ecosystem where devices can make decisions autonomously. With blockchain’s smart contracts, devices can execute actions when specific conditions are met, from ordering supplies when they run low to self-diagnosing and scheduling maintenance.
- Interoperability and Standardization: As more manufacturers embrace IoT, the risk of fragmented ecosystems increases. Blockchain can offer a standardized platform where devices, regardless of the manufacturer, can communicate and operate seamlessly.
Table 1: Benefits of Blockchain IoT Security System
| Feature | Traditional IoT Systems | Blockchain-Integrated IoT Systems |
|---|---|---|
| Data Tampering | Vulnerable | Highly Resistant |
| Interoperability | Limited | Enhanced |
| Autonomous Operations | Minimal | Advanced (via Smart Contracts) |
| Trust Mechanism | Centralized | Decentralized |
The Ongoing Evolution of IoT Security Regulations
- The Need for Regulation: As IoT devices permeate every facet of our lives, from healthcare to transportation, the need for robust security regulations becomes paramount. These regulations aim to protect user data, ensure device safety, and maintain public trust.
- Global Standardization Efforts: Recognizing the universal nature of IoT challenges, global bodies like the International Organization for Standardization (ISO) are working on creating standardized security guidelines for IoT devices, which blockchain can help enforce.
- Adaptive Regulatory Frameworks: The dynamic nature of technology means that regulations need to be adaptive. As blockchain and IoT technologies evolve, so will the regulatory frameworks, ensuring they remain relevant and effective.
- Stakeholder Collaboration: The future of IoT security regulations will hinge on the collaboration between various stakeholders – device manufacturers, software developers, blockchain experts, and regulatory bodies. Together, they can shape a secure and user-centric IoT landscape.
Conclusion: The Convergence of Blockchain and IoT
The intertwining of Blockchain and the Internet of Things (IoT) signifies a transformative shift in the digital realm, promising a future where devices are not only interconnected but also operate with unparalleled security and autonomy. The decentralized nature of blockchain, combined with its inherent data integrity features, complements the vast, data-driven landscape of IoT. Together, they have the potential to overcome many of the current vulnerabilities associated with device interconnectivity, data breaches, and system integrity.
As we stand on the precipice of this technological revolution, it’s evident that the fusion of blockchain and IoT will play a pivotal role in shaping the next era of digital innovation. While challenges persist, the collaborative efforts of industry leaders, regulatory bodies, and tech innovators will undoubtedly pave the way for a more secure, efficient, and transparent digital ecosystem. The convergence of these two groundbreaking technologies offers a glimpse into a future where trust, transparency, and innovation coalesce to redefine our digital experiences.








