In today’s digital age, the way we communicate and collaborate has undergone a significant transformation. With the rise of remote work and global teams, virtual meetings have become an indispensable tool for businesses and individuals alike. From daily check-ins to high-stakes board meetings, the virtual space is where decisions are made, ideas are brainstormed, and relationships are forged.
| Year | Number of Virtual Meetings (in millions) |
|---|---|
| 2018 | 50 |
| 2019 | 70 |
| 2020 | 120 |
| 2021 | 150 |
However, with this convenience comes a set of challenges, the most pressing of which is security. As the table indicates, the frequency of virtual meetings has surged, making them a prime target for cybercriminals. Eavesdropping, unauthorized access, and data breaches can have severe consequences, both in terms of financial losses and reputational damage. Imagine discussing a confidential product launch, only to find out that a competitor was silently listening in. Or consider the ramifications of personal data being leaked from a healthcare consultation conducted over a video call.
Common Oversights in Virtual Meeting Security
As virtual meetings become more commonplace, it’s easy to fall into a routine and overlook potential security vulnerabilities. Here are some of the most frequent missteps that can inadvertently compromise the safety of your virtual interactions:
Reusing Access Codes: One of the most common mistakes is the continuous reuse of the same access codes or meeting IDs. While it might seem convenient, it increases the risk of unauthorized access. If an access code has been shared multiple times, it’s likely that it’s known by more people than you might realize.
Overlooking Waiting Rooms: Many virtual meeting platforms offer a ‘waiting room’ feature, where participants wait to be admitted by the host. Neglecting this feature means anyone with the meeting link can join, even if they weren’t invited.
Not Monitoring Attendees: Once a meeting starts, it’s crucial to keep an eye on the participant list. If you don’t recognize someone, it’s worth pausing the meeting to ascertain their identity.
Recording Without Consent: Automatically recording meetings can be a breach of privacy, especially if participants are unaware. Always inform attendees if a session is being recorded and ensure recordings are stored securely.
Sharing Sensitive Information on Screen: When sharing your screen, ensure that sensitive information, like passwords or confidential documents, isn’t inadvertently displayed.
Using Unsecured Networks: Joining a virtual meeting from a public Wi-Fi network can expose your data to eavesdroppers. Always ensure you’re on a secure, private network when attending or hosting virtual meetings.
Ignoring Software Updates: Meeting platforms regularly release updates to enhance security and fix vulnerabilities. Ignoring these updates can leave your meetings exposed to known threats.
Essential Security Features in Virtual Meeting Platforms
The good news for users is that most virtual meeting platforms are acutely aware of the security concerns surrounding online meetings. As a result, they’ve integrated a range of security features to help ensure the safety of their users. Let’s explore some of these essential features:
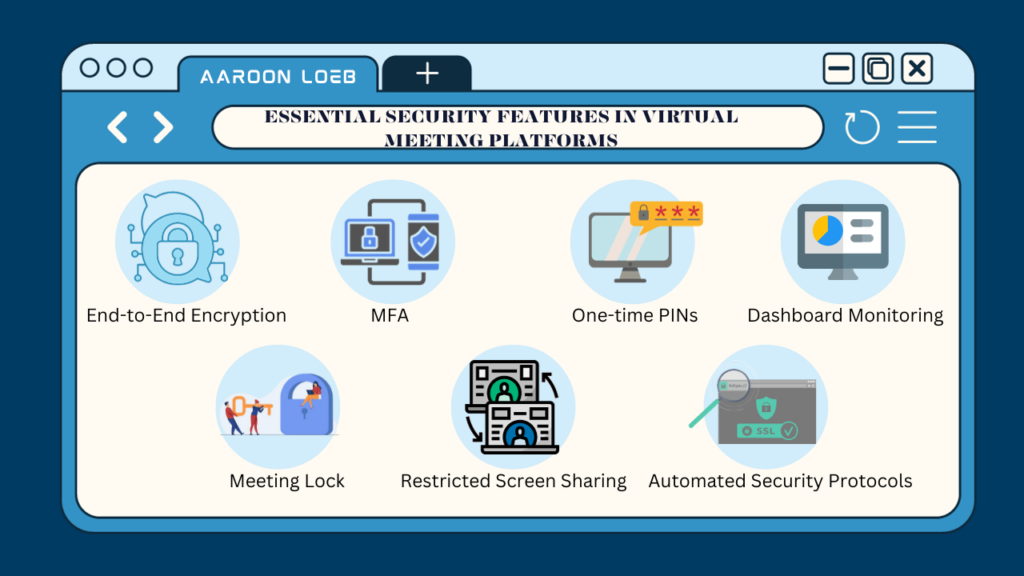
End-to-End Encryption: At the forefront of these security measures is end-to-end encryption. This feature ensures that all data—whether audio, video, or text—transmitted between participants is encrypted from the moment it leaves the sender until it reaches the recipient. This encryption method acts as a formidable shield, making it exceedingly challenging for malicious actors to intercept and decipher the meeting’s content.
Multi-factor Authentication (MFA): Another robust security feature is multi-factor authentication. MFA goes beyond the traditional username and password model, requiring users to provide additional verification, such as a fingerprint, a mobile verification code, or even facial recognition. This multi-tiered approach significantly reduces the chances of unauthorized access, even if a malicious actor obtains a user’s primary login credentials.
One-time PINs or Meeting Identifier Codes: To further combat unauthorized access, many platforms have moved away from static meeting IDs. Instead, they generate unique codes or PINs for each meeting. This dynamic approach ensures that even if a meeting’s access details are inadvertently shared or discovered, they cannot be reused maliciously in the future.
Dashboard Monitoring: Empowering meeting hosts is another focus of virtual meeting platforms. Dashboards provide hosts with real-time insights into attendees, granting them the ability to monitor who joins the meeting and when. If an unfamiliar or unexpected participant joins, the host can swiftly identify and, if necessary, remove them, ensuring the meeting’s integrity.
Meeting Lock: A simple yet effective feature is the ability to ‘lock’ a meeting once it has started and all expected participants have joined. This lock acts as a barrier, preventing any new, potentially unauthorized users from joining mid-way and disrupting the proceedings.
Restricted Screen Sharing: Screen sharing is a vital tool in virtual meetings, but it can also be a vulnerability if misused. To counter this, platforms have introduced restricted screen sharing, ensuring that only those with permission—usually the host or designated participants—can share their screens. This measure prevents malicious or accidental sharing of inappropriate or sensitive content.
Automated Security Protocols: The integration of artificial intelligence (AI) into virtual meeting platforms is a testament to the evolving nature of digital security. Some platforms now boast AI-driven features that proactively detect and block suspicious activities or users. These automated protocols work in the background, offering an added layer of security without requiring manual intervention.
Best Practices for Hosting Secure Virtual Meetings
While having access to a plethora of security features is beneficial, knowing how to effectively implement them is crucial. Here are some best practices to ensure that your virtual meetings remain secure and productive:
Educate and Train Participants: Before hosting a meeting, ensure that all participants are aware of the platform’s security features. A brief training session or a simple guide can go a long way in ensuring everyone is on the same page.
Schedule with Care: Avoid posting meeting links or access codes on public forums or websites. Instead, send them directly to participants via secure email or messaging platforms.
Verify Attendee Identities: At the start of the meeting, take a moment to verify the identity of all participants. If someone is unfamiliar, don’t hesitate to ask them to introduce themselves.
Use Waiting Rooms Effectively: Enable the waiting room feature and admit participants manually. This gives you control over who joins the meeting and when.
Limit Screen Sharing: By default, set screen sharing to ‘host only.’ If a participant needs to share their screen, grant them permission individually.
Mute Participants on Entry: To prevent disruptions, especially in large meetings, mute participants as they join. Allow them to unmute themselves when they need to speak.
Regularly Update Meeting Software: Ensure that your virtual meeting software is always updated to the latest version. This ensures you have the latest security patches and features.
Avoid Recording Unless Necessary: If you must record a meeting, inform participants in advance. Store recordings securely and consider encrypting them for added security.
End Meetings Properly: Once the meeting concludes, ensure you end it for all participants. This prevents the platform from being used without your knowledge once you leave.
Post-Meeting Review: After the meeting, review any recordings or notes to ensure no sensitive information is inadvertently shared. If recordings are no longer needed, delete them to reduce potential security risks.
Advanced Security Measures for Sensitive Meetings
For meetings where highly confidential information is discussed, standard security measures might not suffice. In such scenarios, it’s imperative to adopt advanced security protocols to ensure the utmost protection. Here’s a guide to fortifying your virtual meetings when dealing with sensitive content:

Consult with IT Professionals: Before hosting a sensitive meeting, consult with your organization’s IT or cybersecurity team. They can provide tailored recommendations and might even monitor the meeting for added security.
Use Unique PINs or Passwords: Generate a unique PIN or password for each attendee. Instruct them not to share these credentials and to enter the meeting individually.
Implement Advanced Encryption: While most platforms offer end-to-end encryption, consider using additional encryption tools or VPNs to add another layer of security.
Lock the Meeting: Once all verified participants are present, lock the meeting. This ensures no one else can join, even if they have the access code.
Conduct Meetings on Organization-Issued Devices: Encourage participants to use devices provided by the organization. These devices often have added security measures and are regularly monitored for threats.
Limit Screen Sharing and File Transfers: Only allow hosts to share their screens and disable file transfer options to prevent the sharing of malicious files.
Encrypt Recordings: If you need to record the meeting, ensure the recording is encrypted. Provide decryption keys only to authorized personnel.
Conduct Regular Security Audits: Periodically review the security protocols of your virtual meeting platform. Conduct audits to identify potential vulnerabilities and address them promptly.
Use Biometric Authentication: Some advanced platforms offer biometric authentication, such as fingerprint or facial recognition. Use these features to ensure only authorized individuals can access the meeting.
Have a Contingency Plan: Always be prepared for potential security breaches. Have a plan in place to address any issues, such as immediately ending the meeting, notifying participants, and conducting a post-breach analysis.
The Role of Meeting Participants in Ensuring Security
While hosts shoulder a significant portion of the responsibility for securing virtual meetings, participants play an equally crucial role. A chain is only as strong as its weakest link, and in the context of virtual meetings, a single participant’s oversight can compromise the security of the entire session. Here’s how participants can contribute to a safer virtual meeting environment:
Stay Updated: Ensure that you’re using the latest version of the meeting software. Updates often contain essential security patches that protect against known vulnerabilities.
Be Cautious with Links: Only click on meeting links from trusted sources. Phishing scams often mimic meeting invites to lure victims.
Protect Your Environment: Attend meetings from a quiet, private location. Ensure no sensitive information (like passwords on sticky notes) is visible if using video.Use Headphones: This simple measure can prevent others around you from eavesdropping on the meeting’s content, especially if discussing confidential information.
Mute When Not Speaking: Keeping yourself muted reduces background noise and ensures private or sensitive side conversations aren’t accidentally broadcasted.
Avoid Sharing Personal Data: Unless necessary, refrain from sharing personal or sensitive data during the meeting. If you must, verify the attendees and use direct messaging instead of public chat.
Log Out Completely: Once the meeting concludes, ensure you log out completely rather than just closing the application. This ensures your connection to the meeting is entirely terminated.
Report Suspicious Activity: If you notice something amiss, such as an unfamiliar participant or strange files being shared, alert the host immediately.
Educate Yourself: Familiarize yourself with the platform’s security features. Knowing how to use features like the waiting room or how to report issues can be invaluable.
Respect Others’ Privacy: If a meeting is being recorded, be mindful of what you share, both verbally and visually. Respect the privacy of other participants and avoid discussing personal details without consent.
Additional Resources and Tools for Secure Virtual Meetings
To further bolster the security of your virtual meetings, there are several external resources and tools available. These can provide added layers of protection, as well as insights and best practices from cybersecurity experts.

NIST’s Recommendations: The National Institute of Standards and Technology (NIST) offers guidelines for securing virtual meetings. Their comprehensive documentation provides insights into potential vulnerabilities and how to address them.
VPN Services: Using a Virtual Private Network (VPN) can encrypt your internet connection, making it harder for eavesdroppers to intercept any data. This is especially useful if you’re joining a meeting from an unsecured network.
Secure Cloud Storage: If you’re storing recordings of your meetings, consider using encrypted cloud storage solutions. These platforms offer enhanced security features to protect your data.
Password Managers: These tools can generate and store strong, unique passwords for each meeting, reducing the risk of unauthorized access.
Cybersecurity Training Platforms: Websites like Cybrary or Coursera offer courses on cybersecurity, helping both hosts and participants understand the nuances of online security.
Third-party Encryption Tools: For ultra-sensitive meetings, consider using third-party tools that offer advanced encryption for both voice and video.
Incident Response Tools: In the event of a security breach, having a tool that can quickly identify, address, and report the issue can be invaluable.
Secure Communication Platforms: For sharing sensitive pre-meeting or post-meeting information, platforms like Signal or Telegram offer encrypted messaging services.
Regular Security Audits: Engage with cybersecurity firms to conduct periodic audits of your virtual meeting practices. This can identify potential vulnerabilities and offer solutions.
Stay Updated with Cybersecurity News: Platforms like The Hacker News or Cybersecurity Ventures provide regular updates on the latest threats and vulnerabilities in the digital world.
Conclusion
In the digital age, as virtual meetings become an integral part of our professional and personal lives, ensuring their security is paramount. From the pitfalls of reusing access codes to the advanced features offered by modern platforms, it’s evident that both meeting hosts and participants play pivotal roles in safeguarding these digital interactions. The myriad of security features, from end-to-end encryption to AI-driven protocols, showcases the tech industry’s commitment to creating a safer virtual space. However, technology alone isn’t the panacea. It’s the synergy of informed users, robust features, and proactive measures that will truly fortify our virtual meeting spaces. As we continue to navigate this interconnected world, let’s prioritize security, stay updated, and ensure that our virtual interactions remain both productive and protected.








