The Internet of Things (IoT) has revolutionized the way we interact with the world around us. From smart homes that adjust the temperature based on our preferences to wearable devices that monitor our health, the IoT ecosystem has seamlessly integrated into our daily lives. As of 2023, there are billions of IoT devices connected worldwide, and this number is expected to grow exponentially in the coming years. However, with this rapid expansion comes a pressing concern: security.
Understanding the IoT Landscape
IoT refers to a network of interconnected devices that can collect, exchange, and process data without requiring human-to-human or human-to-computer interaction. These devices range from everyday household items like refrigerators and thermostats to industrial machinery and healthcare equipment. The primary allure of IoT is its ability to automate processes, provide real-time data, and enhance user experience.
| IoT Device | Primary Function | Example of Use |
|---|---|---|
| Smart Thermostat | Regulate home temperature | Adjust temperature based on user’s daily routine |
| Wearable Fitness Tracker | Monitor health metrics | Track steps, heart rate, and sleep patterns |
| Industrial Sensor | Monitor machinery | Detect anomalies in machine performance |
| Smart Security Camera | Enhance home security | Provide real-time video feed and motion detection alerts |
The Security Imperative
While the benefits of IoT are undeniable, the interconnected nature of these devices presents a unique set of security challenges. Each device serves as a potential entry point for cyberattacks, and a breach in one device can compromise the entire network. Given the personal and often sensitive nature of the data these devices handle, the stakes are incredibly high. A security lapse can lead to significant financial, reputational, and even physical harm.
Moreover, the diverse range of IoT devices, each with its own set of software, hardware, and communication protocols, makes standardizing security measures a complex task. Manufacturers, often in a rush to market their products, might overlook rigorous security testing, leaving devices vulnerable to attacks.
The Current State of IoT Security
The rapid proliferation of IoT devices has ushered in a new era of connectivity. From smart cities to intelligent healthcare systems, the applications of IoT are vast and varied. However, this widespread adoption has also exposed a myriad of security vulnerabilities, making it a prime target for cyber adversaries.

IoT’s Double-Edged Sword
The strength of IoT lies in its interconnectedness. Devices communicate with each other, sharing data and making automated decisions based on this data. For instance, a smart refrigerator can detect when you’re running low on milk and automatically order a fresh carton from your preferred online grocery store. While this level of automation offers unparalleled convenience, it also means that if one device is compromised, the entire network can be at risk.
Security Oversights and Their Implications
A significant concern in the IoT landscape is the lack of standardized security protocols across devices. Many IoT devices are manufactured with a primary focus on functionality and cost-effectiveness, often sidelining security considerations. This oversight can lead to several vulnerabilities:
- Default Credentials: Many devices come with default usernames and passwords, which users often neglect to change. This makes it easy for attackers to gain unauthorized access.
- Unencrypted Data: Without proper encryption, sensitive data transmitted between devices can be intercepted and misused.
- Outdated Software: Devices that aren’t regularly updated can have known security flaws that hackers can exploit.
The implications of these vulnerabilities are vast. For instance, in a smart home setup, a compromised security camera can provide real-time footage to malicious actors, violating the privacy of residents. In an industrial setting, a breach in IoT sensors can lead to machinery malfunctions, posing safety risks and leading to significant financial losses.
A Glimpse into Recent Breaches
In recent years, there have been several high-profile breaches highlighting the vulnerabilities in IoT systems:
- The Mirai Botnet Attack (2016): This attack involved malware that turned networked devices running Linux into remotely controlled bots. These bots then became part of a botnet that launched powerful Distributed Denial of Service (DDoS) attacks. The primary targets were IoT devices like cameras and routers with default credentials.
- Smart Home Intrusions (2019): There were multiple reports of hackers gaining access to smart home devices, including security cameras and speakers. In some cases, hackers spoke to residents through the devices, causing panic and distress.
Characteristics of IoT Devices
IoT devices are diverse in their functionalities and applications, but they share certain inherent characteristics that define their operation and interaction within the larger digital ecosystem. Understanding these characteristics is crucial for grasping the complexities of IoT security.
Sensing and Actuating
At the heart of any IoT device is its ability to sense and actuate. Sensors collect data from the environment, be it temperature readings from a smart thermostat or heart rate measurements from a wearable device. Actuators, on the other hand, perform actions based on the data received. For instance, a smart irrigation system might activate sprinklers when soil moisture levels drop below a certain threshold.
Connectivity and Communication
IoT devices are constantly communicating, either with other devices, central servers, or cloud platforms. This continuous exchange of data is facilitated by various communication protocols, ranging from Wi-Fi and Bluetooth to more specialized protocols like Zigbee or LoRaWAN. The choice of protocol often depends on the device’s specific requirements, such as range, power consumption, and data transmission rate.
Decentralized Decision Making
Unlike traditional systems where decisions are made centrally, many IoT setups allow for decentralized decision-making. Devices can make real-time decisions based on the data they collect without always relying on a central server. This autonomy enhances efficiency but also introduces unique security challenges, as each device becomes a potential point of vulnerability.
Limited Resources
Many IoT devices are designed to be compact and energy-efficient. As a result, they often operate with limited computational power, memory, and battery life. These constraints can make it challenging to implement robust security measures, such as advanced encryption algorithms, which might be resource-intensive.
Diverse Lifespan and Update Cycles
IoT devices can have vastly different lifespans and update cycles. While a smartphone might receive regular software updates and be replaced every few years, an industrial IoT sensor could remain operational for a decade or more without any significant updates. This disparity can lead to older devices becoming security liabilities if they’re not adequately maintained.
The Human Element
Lastly, it’s essential to consider the human element in the IoT equation. Users interact with these devices daily, and their behaviors, such as setting weak passwords or ignoring software updates, can introduce vulnerabilities. Educating users about best practices is as crucial as implementing technical security measures.
Opportunities Offered by IoT
The Internet of Things (IoT) stands at the intersection of technology and daily life, offering transformative solutions that redefine traditional boundaries. Its applications are vast, touching almost every sector and presenting opportunities that are both innovative and impactful.
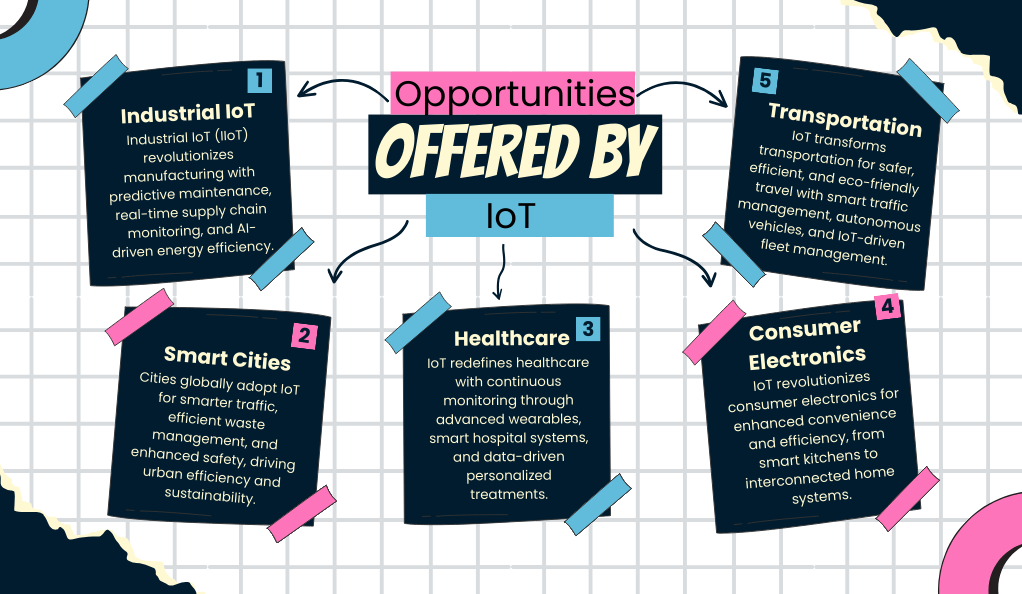
Industrial IoT (IIoT): The Backbone of Modern Industries
The industrial realm has witnessed a paradigm shift with the advent of IIoT. This integration of connected devices within the manufacturing and industrial sectors has led to:
- Predictive Maintenance: Beyond just monitoring, advanced algorithms analyze machinery data to predict potential failures. This proactive approach minimizes unplanned downtimes, ensuring consistent productivity.
- Supply Chain Transparency: With IoT sensors, every step of the supply chain, from raw material sourcing to product delivery, can be monitored in real-time. This transparency ensures timely interventions, reduces inefficiencies, and fosters trust among stakeholders.
- Energy Management: Advanced energy monitoring systems, combined with AI-driven analytics, can dynamically adjust energy consumption based on need, significantly reducing costs and environmental impact.
Smart Cities: The Future of Urban Living
As urban populations swell, cities worldwide are turning to IoT to address challenges and enhance the quality of urban life.
- Adaptive Traffic Systems: Beyond just monitoring, these systems analyze traffic patterns, predict congestion points, and dynamically adjust signals and routes to ensure smooth traffic flow.
- Intelligent Waste Management: IoT-enabled bins can not only signal when they’re full but also predict waste generation patterns, leading to more efficient waste collection and recycling processes.
- Public Safety and Surveillance: Advanced surveillance systems, integrated with facial recognition and anomaly detection algorithms, ensure public spaces remain safe. Additionally, IoT-enabled emergency response systems ensure quicker reaction times during crises.
Healthcare: Personalized and Proactive Care
IoT’s impact on healthcare goes beyond remote monitoring, heralding an era of personalized and proactive care.
- Continuous Health Monitoring: Advanced wearables now monitor a range of health metrics, from blood oxygen levels to electrocardiogram (ECG) readings, providing a comprehensive health overview.
- Smart Hospital Infrastructure: From tracking equipment to monitoring patient vitals in real-time, IoT ensures hospitals operate at peak efficiency while delivering optimal patient care.
- Data-Driven Treatment Plans: With continuous data collection, treatments can be tailored not just based on symptoms but also on individual health patterns and responses.
Consumer Electronics: Beyond Convenience
The realm of consumer electronics has been revolutionized by IoT, offering not just convenience but also enhanced efficiency.
- Smart Kitchens: Imagine refrigerators that not only notify you when you’re out of milk but also suggest recipes based on the ingredients available. Or ovens that adjust cooking times and temperatures based on the dish being prepared.
- Integrated Home Systems: Voice assistants, when integrated with IoT, can control everything from lighting and temperature to security systems, creating a truly interconnected home environment.
Transportation: Navigating the Future
The transportation sector stands to gain immensely from IoT integrations, making travel safer, more efficient, and environmentally friendly.
- Intelligent Traffic Management: By analyzing traffic patterns, weather conditions, and even special events, traffic management systems can predict and mitigate congestion points.
- Autonomous Vehicles: Cars, buses, and even trucks equipped with IoT sensors can communicate with each other, making autonomous driving a reality. This not only ensures safety but also optimizes fuel consumption and reduces traffic jams.
- Fleet Management: For businesses, IoT-enabled real-time monitoring of vehicles ensures timely deliveries, reduces operational costs, and enhances vehicle maintenance.
Foundational Elements of IoT Systems
The Internet of Things (IoT) is a complex interplay of various components, each serving a distinct yet interconnected role.
Hardware Architecture: At the heart of any IoT device are its tangible components. Sensors, often described as the eyes and ears, capture a myriad of data, from environmental conditions to visual inputs. Actuators, in response, execute actions, whether that’s motors propelling devices, speakers emitting sounds, or lights signaling information. Central to this orchestration are microcontrollers, which can be likened to the device’s brain, processing the data and guiding the system’s responses.
Software Dynamics: Beyond the physical, the software realm of IoT devices is multifaceted. Many of these devices operate on specialized operating systems, akin to the ones in PCs, which manage the intricate dance between hardware and software. The application layer, tailored for each device, provides specific functionalities, be it data interpretation, user interaction, or device controls. Embedded deep within is the firmware, a foundational layer of software that dictates the basic operations and interactions of the device.
Communication Mechanisms: In the world of IoT, communication is the linchpin. Devices rely on established communication protocols, such as MQTT, CoAP, and HTTP, to define and streamline their interactions. This continuous flow of data is channeled through a robust networking infrastructure, which includes routers, gateways, and other pivotal equipment.
Data Management: Data, once harvested, demands meticulous handling. A significant portion of IoT devices lean on expansive cloud ecosystems, like AWS IoT, Google Cloud IoT, or Microsoft Azure IoT, for both storage and in-depth analysis. However, a rising trend is edge processing, where data is processed at the source, optimizing both speed and efficiency.
Security Framework: Given the vast interconnectedness of IoT, security is not just essential; it’s paramount. Data encryption ensures that transmitted information remains both confidential and unaltered. Authentication protocols stand as gatekeepers, validating the identities of devices and users. And to shield against potential external threats, defensive systems, encompassing firewalls and intrusion detection mechanisms, are in constant vigil.
Challenges in IoT Security
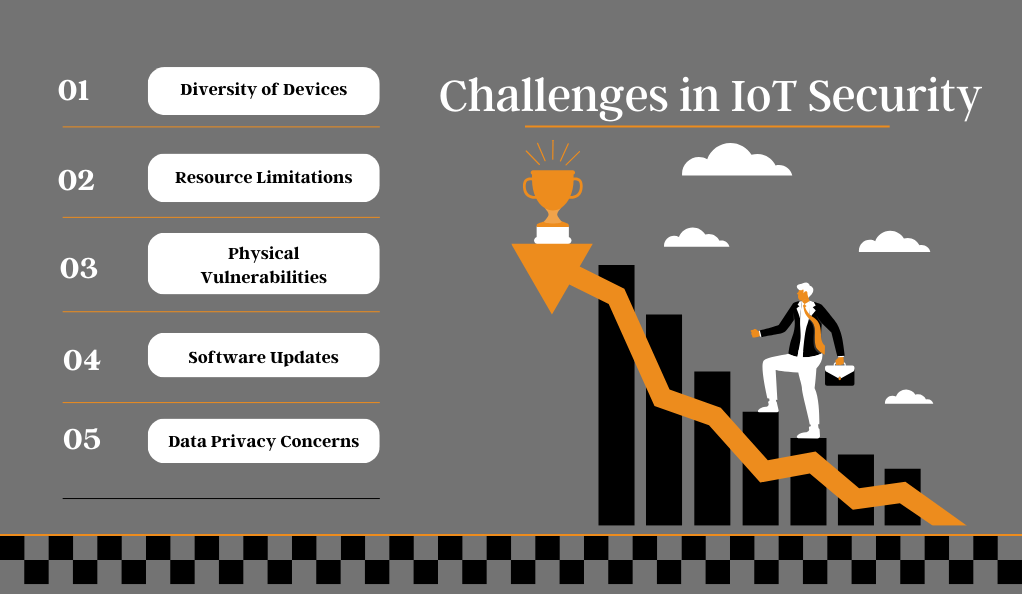
The vast scope of IoT security goes beyond just the device. Here are some of the primary challenges:
- Diversity of Devices: With a myriad of manufacturers, models, and operating systems, standardizing security protocols is a daunting task.
- Resource Limitations: As mentioned earlier, many IoT devices operate with limited computational power and memory, making it challenging to implement robust security measures.
- Physical Vulnerabilities: Unlike traditional computing systems, IoT devices are often out in the open, making them susceptible to physical tampering.
- Software Updates: Many devices don’t receive regular updates, leaving them vulnerable to known security flaws.
- Data Privacy Concerns: With devices collecting vast amounts of data, often personal, ensuring this data remains private is paramount.
Strategies and Protocols for IoT Security
The world of the Internet of Things (IoT) is vast and ever-evolving, bringing forth a myriad of security challenges. To navigate this intricate landscape, a comprehensive and multi-layered strategy is indispensable. Every participant, from the architects who design these devices to the end-users who deploy them, holds the key to the fortress of IoT security.
Proactive Security Integration: The cornerstone of robust IoT security lies in the principle of ‘security by design.’ Instead of retrofitting security measures, devices should be conceived and crafted with intrinsic security features. This encompasses integrating advanced mechanisms like secure boot directly into the device’s hardware, ensuring a foundation of trust. Moreover, by streamlining device functionalities and eliminating redundant features, the potential attack surface for adversaries is significantly reduced.
Commitment to Software Vigilance: Software is the lifeblood of IoT devices, and its integrity is paramount. Adopting adaptive Over-the-Air (OTA) mechanisms allows devices to be remotely updated with the latest security patches and enhancements. But beyond the technicalities, it’s crucial to engage with the user community. By proactively notifying them of updates and underscoring the security implications, a culture of vigilance and prompt software updates can be fostered.
Robust Data Protection Protocols: In our data-driven age, safeguarding information is more critical than ever. Adopting a holistic encryption approach ensures that data, whether at rest or in transit, remains shielded from prying eyes. This end-to-end encryption, coupled with advanced key management systems, offers a formidable defense against data breaches.
Rigorous Access Protocols: Controlling access is a pivotal aspect of IoT security. Implementing enhanced authentication mechanisms, such as Multi-Factor Authentication (MFA), adds layers of verification, ensuring only authorized individuals gain access. Furthermore, the granularity of Role-Based Access Control (RBAC) tailors permissions, ensuring users access only what’s pertinent to their role, fostering both security and efficiency.
Network Resilience: The interconnected web of IoT demands unwavering network security. Dynamic firewalls, which do more than just block traffic, intelligently regulate data flow, ensuring only legitimate interactions. Complementing this are the vigilant eyes of Intrusion Detection and Prevention Systems (IDPS), continuously scanning for anomalies and initiating countermeasures at the slightest hint of a threat.
Empowering Users: At the end of the day, the human element is both a potential vulnerability and a formidable asset. By offering continuous security training, users can be updated on the evolving threat landscape. Coupled with accessible and user-friendly security documentation, users are equipped with the knowledge and tools to be the first line of defense.
Conclusion
The Internet of Things offers a world of possibilities, from smart homes that cater to our every need to industries that operate with unprecedented efficiency. However, with these opportunities come challenges, especially in the realm of security. By understanding these challenges and implementing the countermeasures discussed, we can pave the way for a secure and prosperous IoT future.