In the vast expanse of the digital universe, email stands as one of the pioneering tools that revolutionized the way we communicate. Often hailed as the internet’s “killer app”, email has woven itself into the very fabric of our daily lives, becoming an indispensable tool for both personal and professional communication.
A Brief History of Email as the Internet’s “Killer App”
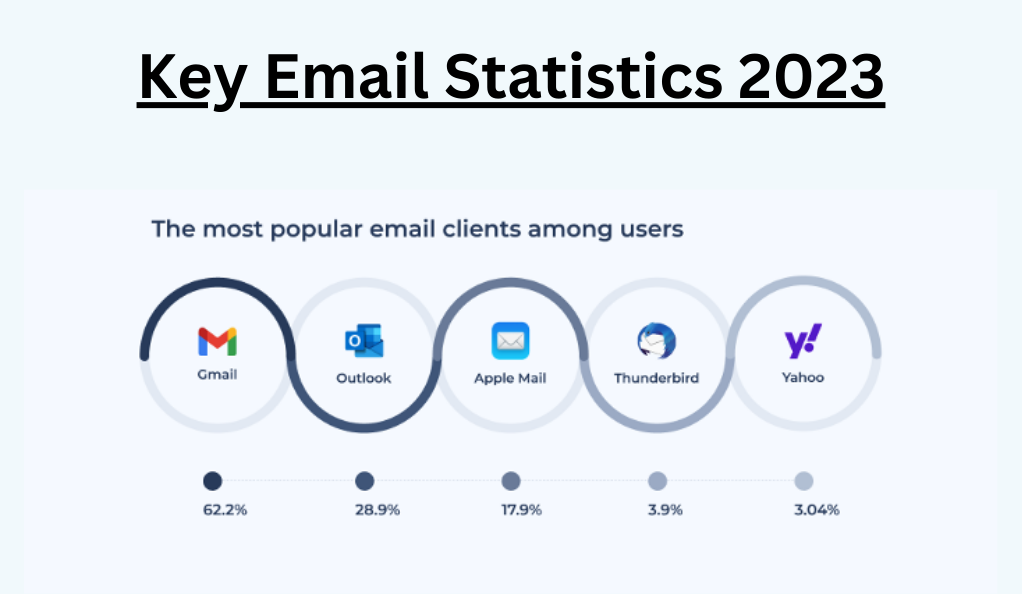
The term “killer app” refers to a software application that is so useful or desirable that it proves the core value of some larger technology. In the early days of the internet, that killer application was email. Before the rise of social media, video streaming, and online gaming, email was the primary reason many people went online. It offered a way to send and receive messages instantaneously, breaking the barriers of time and distance.
In its infancy, email was a simple tool. It was designed for basic text-based communication between users on the same computer. As the internet grew, so did email’s capabilities, allowing users to send messages across vast networks to anyone with an email address. Attachments, hyperlinks, and rich text formatting soon followed, enhancing the user experience.
The Pervasive Role of Email in Today’s Digital Age
Today, email is more than just a communication tool. It’s an identifier, a storage vault, and a gateway to the digital world. From signing up for social media accounts to receiving bank statements, from collaborating on work projects to staying in touch with loved ones across the globe, email plays a pivotal role.
Consider these facts:
- Ubiquity: Over 4 billion people worldwide use email, making it one of the most widely used digital communication tools.
- Versatility: Email is platform-agnostic. Whether you’re on a smartphone, tablet, laptop, or desktop, you can access your email.
- Functionality: Beyond communication, email serves as a digital locker. Receipts, tickets, contracts, and memories, all stored in our inboxes.
| Key Email Statistics | |
|---|---|
| Number of email users worldwide | 4.1 billion |
| Average number of email accounts per user | 1.75 |
| Total number of business and consumer emails sent daily | 319.6 billion |
| Percentage of emails that are spam | 28.5% |
However, with great power comes great responsibility. The very features that make email indispensable also make it a prime target for cyberattacks, fraud, and espionage. As we delve deeper into the dangers of unsecured email, it’s crucial to understand the inherent vulnerabilities of this medium and the real-world consequences of neglecting email security.
The Inherent Insecurity of Email
Email, despite its widespread use and significance, was not originally designed with robust security in mind. Its primary purpose was to facilitate communication, and as such, many of its foundational protocols lack the security measures that are standard in today’s digital tools.
How Email Was Not Designed with Security in Mind
When email was first conceptualized in the 1970s, the internet was a vastly different place. It was a smaller, more insular network primarily used by academic institutions and government agencies. The threats we associate with the internet today—hackers, phishing schemes, malware—were virtually non-existent. As a result, email was developed as an open system, prioritizing ease of communication over security.
In its original design:
- Transmission: Emails were sent in plain text over the network, making them easily readable by anyone who could access the data traffic.
- Storage: On servers, emails were (and often still are) stored without encryption, making them vulnerable to breaches.
- Authentication: There was no robust mechanism to verify the identity of senders, leading to the possibility of impersonation and spoofing.
The Evolution of Email and Its Vulnerabilities
As the internet expanded and began to play a more integral role in business and personal communication, the vulnerabilities in email’s design became more apparent. Cybercriminals recognized the potential of exploiting these weaknesses for financial gain, espionage, or simply to cause disruption.
Some of the most common email-based threats include:
- Phishing: Cybercriminals impersonate legitimate entities to trick users into providing sensitive information.
- Malware Distribution: Emails containing malicious attachments or links can introduce malware into the recipient’s system.
- Man-in-the-Middle Attacks: Unauthorized entities can intercept email communications, gaining access to the information being shared.
- Spam: Unsolicited emails, often sent in bulk, can flood inboxes, reducing productivity and sometimes serving as a cover for more malicious activities.
The Real-World Implications
The vulnerabilities in email have real-world consequences. Businesses can suffer financial losses, reputational damage, and operational disruptions due to email-based attacks. Individuals can face identity theft, financial fraud, and personal data breaches. Moreover, the psychological impact of being a cyberattack victim—feeling violated, vulnerable, and distrustful—cannot be understated.
Real-world Consequences of Unsecured Emails
The digital realm’s threats often manifest in tangible, real-world consequences. Unsecured emails, being a primary vector for many cyberattacks, have led to significant incidents with far-reaching implications.
High-Profile Breaches
Over the years, several high-profile email breaches have made headlines, underscoring the dangers of unsecured email communication. From political organizations to multinational corporations, no entity is immune. These breaches have led to the exposure of sensitive data, strategic communications, and personal information, often resulting in public scandals, financial repercussions, and strategic setbacks.
Collateral Damage: Beyond the Immediate Victim
While the direct victims of email breaches face immediate consequences, the ripple effects often extend much further. For instance:
- Trust Erosion: When a trusted institution suffers a breach, it erodes public trust not only in that entity but often in digital communication as a whole.
- Financial Markets: Breaches, especially in significant corporations, can influence stock prices and investor confidence.
- Regulatory Repercussions: Significant breaches often lead to tighter regulations, impacting industries and shaping digital communication norms.
The Personal Toll
For individuals, an unsecured email can lead to personal and financial turmoil. Identity theft, fraudulent transactions, and personal data exposure can take months, if not years, to fully resolve. The emotional and psychological strain, coupled with potential financial hardships, can be overwhelming.
Why Email Isn’t Secure by Default
To truly grasp the gravity of email security concerns, it’s essential to understand the technical underpinnings of email and the inherent vulnerabilities in its design.
The Original Design and Intent of Email
Email’s foundational protocols, such as SMTP (Simple Mail Transfer Protocol), were developed during a time when the internet was more of a collaborative, trust-based network. The primary goal was seamless communication, not security.
- Open Transmission: Originally, emails were transmitted in plain text. This means that anyone with the right tools and access could easily read the content of emails as they traveled across networks.
- Lack of Authentication: Early email systems didn’t have mechanisms to verify if an email genuinely came from the claimed sender. This lack of authentication is what makes spoofing and phishing attacks possible today.
- Server Storage Vulnerabilities: Emails are stored on servers, which, if not properly secured, can be accessed by malicious actors. Originally, there was no encryption for these stored emails, making them easy targets.
The Four Main Points of Email Vulnerability
- On Your Device(s): If your personal devices like computers or smartphones are compromised, attackers can easily access your emails. This vulnerability emphasizes the importance of device security.
- On the Networks: As emails travel across the internet, they pass through multiple networks. If the email data isn’t encrypted, it can be intercepted and read at any of these points.
- On the Server(s): Email service providers store your emails on their servers. If these servers are breached, all your stored emails can be accessed.
- On Your Recipient’s Device(s): Even if you take all precautions, the security of your emails also depends on the recipient’s device security. If their device is compromised, your sent emails can be accessed.
The Illusion of Encrypted Connections
While encryption has been heralded as the solution to email’s security woes, it’s crucial to differentiate between the types of encryption and understand their limitations.
Encrypting Messages vs. Encrypting Network Connections:
When it comes to email security, there’s a significant distinction between encrypting the actual content of messages and encrypting the network connections through which these messages travel. Encrypting the content ensures that the email’s message is scrambled, decipherable only by the intended recipient with the correct decryption key. While this method offers a high level of security, it can be cumbersome. Both the sender and the recipient need the necessary encryption tools and keys, which can sometimes be a barrier to seamless communication.
On the other hand, encrypting network connections, akin to the encryption seen on secure websites like online banking platforms, ensures data traveling between the sender’s device and the email server remains private. However, this type of encryption doesn’t necessarily secure the email once it’s stored on the server, where it’s often kept in plain text.
The Limitations of Encrypted Connections:
While encrypted connections offer a layer of security, they come with their own set of limitations. For an email connection to be fully encrypted, both the sender’s and recipient’s email services must support and implement encryption. If one end doesn’t utilize encryption, the entire communication’s security can be compromised. Another challenge is the storage of emails on servers. Even if the connection is encrypted, if the email is stored in plain text on the server, it remains vulnerable to breaches.
Additionally, there’s the often-overlooked issue of metadata. Even with encrypted email content, the metadata, which includes details like the sender, recipient, and time of the email, often remains unencrypted. This data can provide a wealth of information about communication patterns and is a valuable asset for surveillance entities.
Solutions to Secure Your Emails
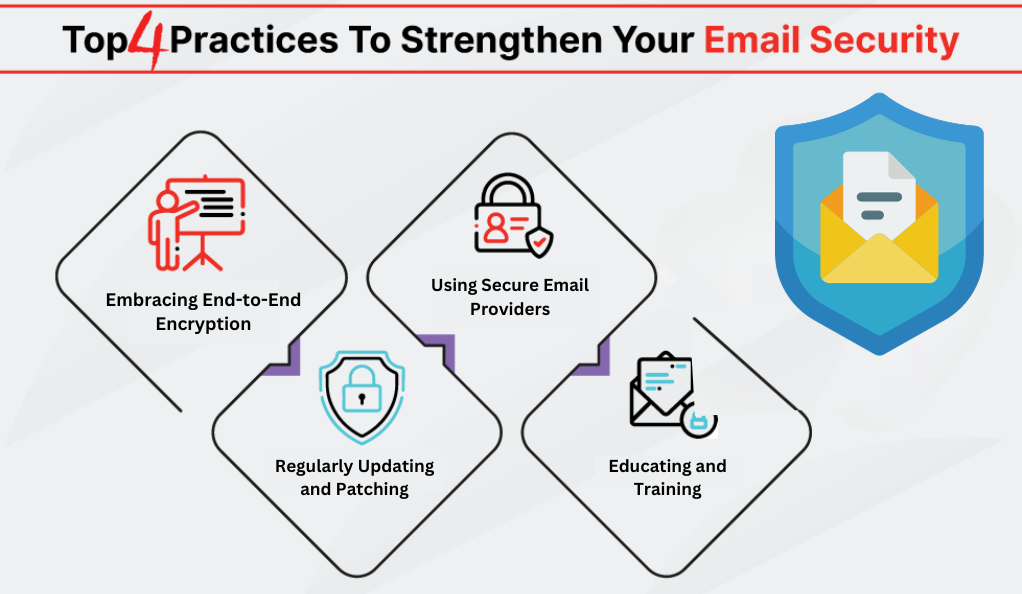
Given the vulnerabilities, it’s easy to feel that email is a lost cause. However, several solutions and best practices can significantly enhance email security.
- Embracing End-to-End Encryption
End-to-end encryption ensures that only the sender and the recipient can read the email content. Even if someone intercepts the email during transmission, they won’t be able to decrypt and read it. - Using Secure Email Providers
Some email providers prioritize security, offering features like encrypted storage, automatic end-to-end encryption, and stringent privacy policies. Opting for such providers can enhance security. - Regularly Updating and Patching
Software vulnerabilities can be exploited to breach email security. Regularly updating email clients, operating systems, and other related software can mitigate this risk. - Educating and Training
Human error often leads to security breaches. Regular training and awareness programs can equip users to recognize threats like phishing emails and take appropriate precautions.
The Future of Email Security
As cyber threats continue to evolve, so too must our defenses. The future of email security lies in a combination of technological advancements, policy changes, and user behavior adaptations.
Innovations in Email Security Protocols
The future of email security is poised to be shaped by several innovative protocols. As cyber threats grow in sophistication, there’s a pressing need to overhaul the foundational protocols of email. One area of focus is advanced encryption, which goes beyond just end-to-end encryption to potentially include the encryption of even metadata, ensuring comprehensive security.
Another promising avenue is the integration of blockchain technology. The decentralized and immutable nature of blockchain can be harnessed to verify the authenticity of emails, drastically reducing the chances of spoofing and phishing attacks. Furthermore, the potential of artificial intelligence and machine learning in the realm of email security is vast. These technologies can be adept at detecting unusual patterns, identifying phishing attempts in real-time, and even automating the process of securing sensitive information sent via email.
Policy Changes and Global Standards
For a holistic approach to email security, technological advancements need to be complemented by robust policy changes and the establishment of global standards. As cyber threats know no borders, there’s a growing realization that email security requires international collaboration. Stricter regulations, akin to how GDPR transformed data privacy norms in Europe, could play a pivotal role in holding companies accountable for breaches and ensuring user data’s sanctity.
A unified global standard for email security can ensure consistency in security measures across borders, making it harder for cybercriminals to exploit regional vulnerabilities. Another promising strategy is collaborative threat intelligence. By fostering a culture of collaboration, organizations worldwide can share real-time threat data, ensuring a more agile and coordinated response to emerging cyber threats.
User Behavior and Awareness
At the heart of any security strategy lies the human element. While technology and policies are crucial, the behavior and awareness of users play an equally significant role in determining the efficacy of email security measures. Continuous training programs can arm users with the knowledge to recognize and thwart threats like phishing emails. Another layer of defense is two-factor authentication (2FA). By adding this additional security layer, even if login details are compromised, unauthorized access to email accounts can be prevented. Lastly, fostering a culture of secure practices, such as avoiding suspicious links, regularly updating passwords, and refraining from accessing emails on public Wi-Fi, can go a long way in bolstering email security.
Conclusion
In the digital age, where communication is instantaneous and borders are blurred, email remains a cornerstone. Its vulnerabilities, while significant, are not insurmountable. Through a combination of technological advancements, global collaboration, and user awareness, we can envision a future where email, the internet’s original “killer app,” can be both a powerful communication tool and a bastion of security.
As we navigate this digital landscape, it’s imperative to remember that security is a shared responsibility. From developers and policymakers to everyday users, each of us plays a role in safeguarding our digital communications. By staying informed, adopting best practices, and pushing for innovation, we can ensure that email remains a trusted and secure medium for generations to come.








