In today’s digital age, where cyber threats loom large and data breaches are all too common, the need for enhanced security measures has never been more pressing. Enter Two-Factor Authentication (2FA), a security process that goes beyond the traditional password to provide an extra layer of protection for users.

What is Two-Factor Authentication?
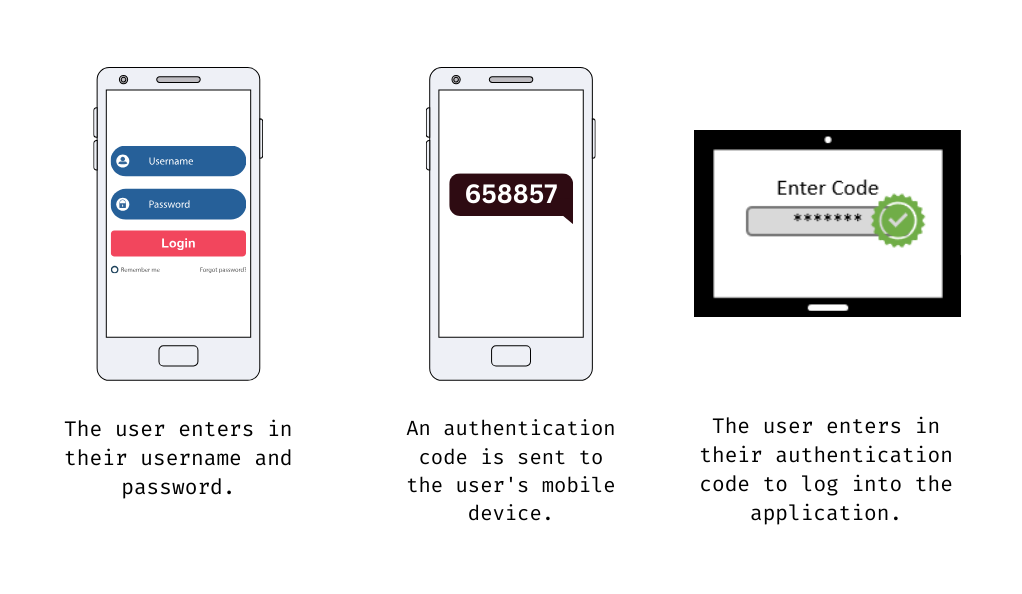
Two-Factor Authentication, often abbreviated as 2FA, is an authentication mechanism designed to ensure that people trying to gain access to an online account are who they claim to be. Instead of merely asking for a username and password, 2FA requires a second piece of evidence, or “factor,” to verify identity. This second factor could be something you know (like a password), something you have (like a physical device), or something you are (like a fingerprint or other biometric trait).
| Factor Type | Examples |
|---|---|
| Something you know | Password, PIN, security question |
| Something you have | Smartphone, smart card, security token |
| Something you are | Fingerprint, facial recognition, voice pattern |
Why is 2FA Important?
The digital landscape is fraught with hackers and cybercriminals who have become adept at stealing personal information. Traditional passwords, no matter how complex, are no longer enough to keep these adversaries at bay. With 2FA, even if a malicious actor obtains your password, they would still need the second factor to access your account, making unauthorized access significantly more challenging.
Furthermore, the increasing number of high-profile data breaches has made consumers more conscious of their digital security. Businesses, recognizing this concern, are implementing 2FA to not only protect their users but also to build trust and enhance their reputation.
The Evolution of Authentication
Historically, the humble password was the sole guardian of our digital identities. However, as cyber threats evolved, so did our defenses. From PINs at ATMs to biometric scans on smartphones, the journey of authentication has been one of continuous innovation. Two-Factor Authentication is the next logical step in this evolution, bridging the gap between convenience and security.
The Mechanics of 2FA
Understanding the intricacies of Two-Factor Authentication requires a deep dive into its core mechanics. At its heart, 2FA is about layering security measures to create a more robust defense against unauthorized access.
The Dual Layers of Security
The primary principle behind 2FA is the combination of two distinct authentication methods. This dual-layer approach ensures that even if one factor is compromised, the second layer remains intact, acting as a barrier against potential breaches.
- First Factor – Knowledge-Based Authentication: This is the traditional method most people are familiar with. It involves something the user knows, such as a password, PIN, or the answer to a security question. While this method has been the standard for years, it’s also the most vulnerable. Hackers often exploit weak or reused passwords, making this layer susceptible to breaches.
- Second Factor – Possession or Inherence-Based Authentication: This layer is where 2FA truly shines. It requires the user to present evidence of something they have (like a smartphone or a hardware token) or something inherent to their identity (like a fingerprint or voice pattern). This factor is much harder for cybercriminals to replicate or steal, adding a significant layer of security.
Common 2FA Methods
Several methods have emerged as popular choices for the second factor in 2FA:
- SMS Verification: After entering a password, the user receives a one-time code via SMS, which they must enter to gain access. While convenient, this method has vulnerabilities, especially if the user’s phone is compromised or if the SMS is intercepted.
- Authenticator Apps: Applications like Google Authenticator or Authy generate time-sensitive codes that users must input after providing their password. These apps are generally more secure than SMS verification.
- Hardware Tokens: These are physical devices that generate codes or use a button press to authenticate. They are not connected to the internet, making them highly secure against online hacks.
- Biometrics: Fingerprints, facial recognition, and voice patterns are unique to each individual, making them an excellent choice for authentication. Modern smartphones often come equipped with the necessary sensors for biometric verification.
The User Experience
While 2FA adds an extra step to the login process, it’s a small price to pay for enhanced security. Most users find the process straightforward, especially with intuitive methods like biometric verification. Businesses implementing 2FA often prioritize user experience, ensuring that the added security doesn’t come at the cost of convenience.
Real-World Applications of 2FA
As the digital realm expands, the application of Two-Factor Authentication has permeated various sectors, proving its versatility and importance. From banking to social media, 2FA has become a standard security measure, ensuring that users’ data remains protected.

Banking and Financial Transactions
One of the earliest adopters of 2FA was the banking sector. Given the sensitive nature of financial data, banks have always been at the forefront of security innovations:
- ATM Transactions: The simple act of withdrawing money from an ATM involves 2FA. The ATM card (something you have) combined with a PIN (something you know) ensures that even if a card is lost or stolen, unauthorized access is prevented without the PIN.
- Online Banking: Many banks now send a one-time code to the user’s registered mobile number or email when they attempt to log in or make a significant transaction. This code acts as the second factor, ensuring an added layer of security.
Social Media and Online Platforms
With the rise of social media platforms and the vast amount of personal data they hold, implementing 2FA has become crucial:
- Email Services: Providers like Gmail and Outlook offer 2FA options, usually through SMS or authenticator apps. Given that email accounts can be the gateway to resetting passwords for various services, securing them with 2FA is paramount.
- Social Networks: Platforms like Facebook, Twitter, and Instagram have introduced 2FA to protect users’ accounts from unauthorized access, especially given the rise in account hacking incidents.
E-commerce and Online Shopping
The e-commerce sector, which deals with both personal and financial data of users, has also embraced 2FA:
- Payment Gateways: When making online purchases, users often receive a one-time password (OTP) on their registered mobile number, which they must enter to complete the transaction.
- Account Logins: E-commerce platforms like Amazon and eBay offer 2FA options for logging in, ensuring that users’ accounts and purchase histories remain secure.
Healthcare and Sensitive Data
In sectors where data sensitivity is of utmost importance, 2FA plays a pivotal role:
- Medical Records: Access to electronic medical records often requires multiple authentication steps, especially when accessed remotely, to ensure patient confidentiality.
- Research and Development: Companies involved in R&D, especially in fields like pharmaceuticals or technology, use 2FA to protect their proprietary data from industrial espionage.
Advantages of Using 2FA
In an era where cyber-attacks are becoming increasingly sophisticated, the importance of robust security measures cannot be overstated. Two-Factor Authentication, with its dual-layered approach, offers several advantages that make it a preferred choice for many organizations and individuals.
Enhanced Security Against Unauthorized Access
The primary benefit of 2FA is the added layer of security it provides:
- Barrier to Breaches: Even if a hacker manages to obtain a user’s password, they would still need the second factor to gain access. This makes breaching an account significantly more challenging.
- Protection from Common Attacks: Techniques like brute force attacks, where hackers try multiple password combinations, become less effective when 2FA is in place.
Protection Against Identity Theft and Online Fraud
Identity theft can have severe consequences, both financially and reputationally:
- Financial Safety: With 2FA, even if someone has stolen your credit card details, they would need the second authentication factor (like an OTP sent to your phone) to complete a transaction.
- Personal Data: For platforms that store personal data, 2FA ensures that even if a password is compromised, the data remains secure.
Increased Trust and Credibility
For businesses, implementing 2FA can enhance their reputation:
- Consumer Confidence: Customers are more likely to trust and engage with platforms they believe are secure. Knowing that a service uses 2FA can boost this confidence.
- Regulatory Compliance: Many industries have regulations that mandate certain security measures. Implementing 2FA can help businesses meet these requirements.
Flexibility and Customization
2FA solutions are versatile:
- Multiple Methods: Organizations can choose from various 2FA methods, such as SMS, authenticator apps, or biometrics, depending on their needs and the level of security they desire.
- Adaptive Authentication: Some advanced 2FA systems can adapt based on user behavior. For instance, if a user logs in from a new location or device, the system might prompt for 2FA, even if it doesn’t always do so.
Cost-Effective Security Solution
Compared to other security measures, 2FA offers a cost-effective solution:
- Reduced Breach Costs: The expenses associated with a data breach can be astronomical. By preventing breaches, 2FA can save organizations significant amounts.
- Low Implementation Costs: Many 2FA solutions, especially those based on software or SMS, are relatively inexpensive to implement and maintain.
Challenges and Vulnerabilities
While Two-Factor Authentication offers a robust layer of security, it is not without its challenges and vulnerabilities. Understanding these potential pitfalls is crucial for both users and organizations to maximize the benefits of 2FA while minimizing risks.
Phishing Attacks and Man-in-the-Middle Threats
Cybercriminals have evolved their tactics to bypass 2FA:
- Phishing Schemes: Attackers can create fake login pages to trick users into providing both their password and the second authentication factor, such as an OTP.
- Man-in-the-Middle (MitM) Attacks: In this scenario, a hacker intercepts communication between the user and the service. They can capture both the password and the second factor, granting them unauthorized access.
Issues with SMS-Based Verification
While convenient, SMS-based 2FA has vulnerabilities:
- SIM Swapping: Attackers can trick mobile carriers into transferring a victim’s phone number to a new SIM card. Once done, they can receive all SMS messages, including OTPs, meant for the victim.
- Network Interception: In some cases, SMS messages can be intercepted during transmission, especially if they’re not encrypted.
User Inconvenience and Resistance
Balancing security with user experience is a challenge:
- Extra Step: Some users find the additional authentication step cumbersome, especially if they need to access a service frequently.
- Locked Out: If a user loses their second factor, like a phone or hardware token, they might be locked out of their account until they can recover or reset the authentication method.
Technical Glitches and Failures
No system is infallible, and 2FA is no exception:
- System Downtime: If the system responsible for generating or sending the second factor experiences downtime, users might be unable to access their accounts.
- Sync Issues: Authenticator apps rely on time-based codes. If there’s a time sync issue between the server and the user’s device, the generated codes might not work.
Over-reliance on 2FA
A potential pitfall for organizations:
- Complacency: Believing that having 2FA in place makes a system impervious to attacks can lead to neglecting other essential security measures.
- Single Point of Failure: If the 2FA system itself has vulnerabilities and is compromised, it can become a single point of failure, jeopardizing the security of all accounts.
Modern Implementations and Innovations
The realm of Two-Factor Authentication is not static. As technology evolves and cyber threats become more sophisticated, so do the methods and tools associated with 2FA. Let’s delve into some of the modern implementations and innovations that are shaping the future of this security measure.
Third-Party Authenticator Apps
Beyond the traditional SMS-based 2FA, third-party apps have gained popularity:
- Google Authenticator and Authy: These apps generate time-sensitive codes for users to input during the authentication process. They operate offline, reducing the risk of interception.
- Push-Based Authentication: Some apps, like Duo Security, offer push notifications as an authentication method. Instead of entering a code, users simply approve or deny a login request sent to their device.
Biometric Innovations
Biometric-based 2FA methods are becoming more advanced:
- Facial Recognition: Beyond smartphones, facial recognition is being integrated into various systems, from laptops to secure building access.
- Voice Biometrics: Unique voice patterns can be used as an authentication factor, especially useful for phone-based services.
- Behavioral Biometrics: This involves analyzing patterns in user behavior, such as keystroke dynamics or mouse movements, to authenticate a user.
Universal 2nd Factor (U2F) and Security Keys
U2F is an open authentication standard that strengthens and simplifies 2FA:
- Physical Security Keys: Devices like the YubiKey can be plugged into a computer or tapped on a device to authenticate. They’re resistant to phishing and man-in-the-middle attacks.
- Wireless Options: Some U2F keys use NFC or Bluetooth, allowing for wireless authentication.
Decentralized Authentication
Blockchain technology is being explored for 2FA:
- Decentralized IDs: Instead of relying on a centralized server, authentication data is stored on a decentralized ledger, enhancing security.
- Smart Contracts: These can be used to set up and verify authentication protocols, ensuring transparency and security.
Adaptive and Risk-Based Authentication
Moving beyond static methods, adaptive 2FA adjusts based on the situation:
- Risk Analysis: The system assesses the risk associated with a login attempt. For instance, logging in from a new country might trigger 2FA, while routine logins might not.
- Machine Learning: Algorithms analyze login patterns and behaviors, adjusting authentication requirements in real-time.
Conclusion
In an era where our digital footprints expand with each passing day, the importance of safeguarding our online identities and assets cannot be overstated. Two-Factor Authentication, with its multi-layered approach to security, stands as a beacon of hope against the ever-growing tide of cyber threats. From its foundational principles to the latest innovations, 2FA represents a dynamic and evolving response to the challenges of digital security.
While no system is entirely infallible, the adoption and continuous refinement of 2FA underscore a collective commitment to a safer digital future. For businesses, it’s not just about protecting data; it’s about fostering trust and ensuring continuity. For individuals, it’s about peace of mind in an interconnected world.
As we navigate the complexities of the digital realm, tools like 2FA will be our compass, guiding us towards safer shores. Embracing these tools, staying informed about potential vulnerabilities, and always being proactive in our approach to digital security are the keys to thriving in this digital age. In the end, Two-Factor Authentication is not just a technical measure; it’s a testament to our enduring adaptability and resilience in the face of evolving challenges.








