The Internet of Things (IoT) has become a buzzword in the tech industry, but what does it really mean? And why is it becoming so ubiquitous in our daily lives? Let’s dive deep into the world of IoT.
What is IoT?
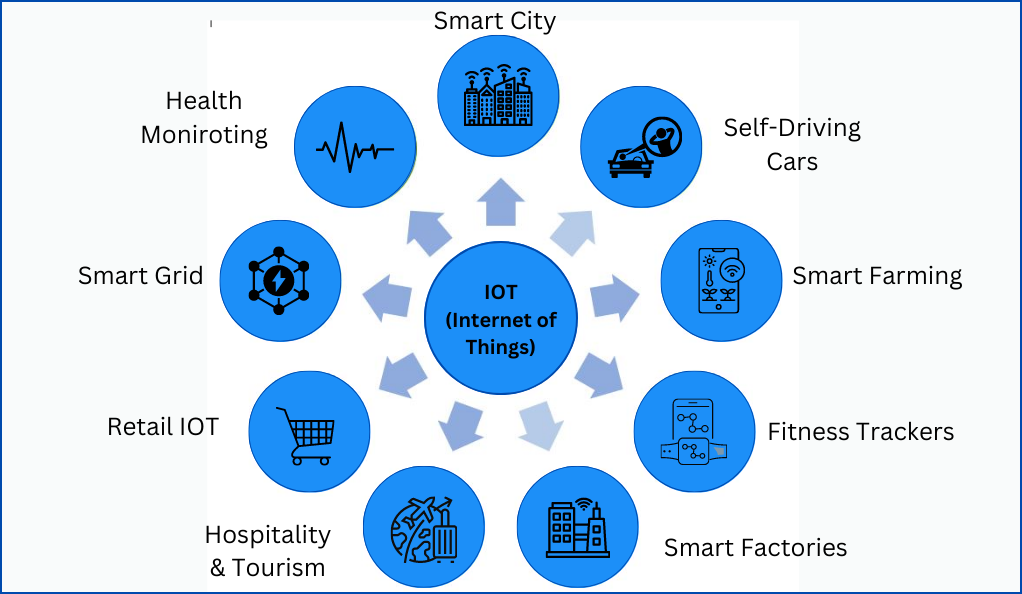
The Internet of Things (IoT) refers to the vast network of interconnected physical devices that can collect and share data without human intervention. These devices, often embedded with sensors, software, and other technologies, connect and exchange data over the internet.
Basic Components of an IoT System
| Component | Description |
|---|---|
| Devices | Physical objects embedded with sensors, software, or other technologies. Examples include smart thermostats, wearable health monitors, and connected vehicles. |
| Connectivity | The method by which devices communicate with each other and with central systems. This can be via Wi-Fi, cellular networks, Bluetooth, or other communication protocols. |
| Data Processing | Once data is collected, it needs to be processed to be useful. This can happen on the device itself (edge computing) or in centralized data centers (cloud computing). |
| User Interface | The interface through which humans interact with the IoT system. This could be a mobile app, a web dashboard, voice commands, etc. |
The Rise of IoT
The concept of interconnected devices has been around for decades, but several factors have contributed to the rapid rise of IoT in recent years:
- Decreasing Costs: The cost of sensors, processors, and other IoT components has dropped significantly, making it economically viable to add connectivity to a wide range of products.
- Increased Internet Penetration: With the internet reaching even the most remote parts of the world, more devices can be connected.
- Advancements in Data Analytics: The ability to process and analyze vast amounts of data in real-time has made IoT more valuable for businesses and consumers alike.
IoT in Everyday Life
IoT, or the Internet of Things, is no longer just a futuristic concept; it has seamlessly woven itself into the fabric of our everyday lives. One of the most prevalent manifestations of this integration is in our homes. Smart homes today are equipped with devices such as thermostats, lights, and security cameras that not only can be controlled remotely but also have the capability to adapt to user behaviors. On a personal level, wearables have become a staple for many. Devices like fitness trackers and smartwatches are now commonplace, monitoring various health metrics and offering real-time feedback to users.
Furthermore, the automotive industry has also embraced IoT with open arms. Modern vehicles are no longer just means of transportation; they come loaded with advanced features such as navigation assistance, the ability to start remotely, and alerts for predictive maintenance. The convergence of technology with daily life through IoT is undeniable, and its applications are vast and continually evolving.
The Ubiquity of IoT
The reason IoT is becoming ubiquitous is its potential to bring efficiency, convenience, and automation to almost every sector. From agriculture (with smart irrigation systems) to healthcare (with remote patient monitoring), the applications are endless.
However, with this ubiquity comes challenges, especially in terms of security and privacy. As more devices get connected, the potential for data breaches and other cyber threats increases. It’s crucial for manufacturers, developers, and users to prioritize security as the IoT landscape continues to expand.
Understanding IoT Security
The Internet of Things (IoT) has revolutionized the way we interact with devices, offering unprecedented convenience and automation. However, with the increasing interconnectivity of devices comes the paramount importance of understanding and ensuring their security. Let’s delve deep into the intricacies of IoT security.
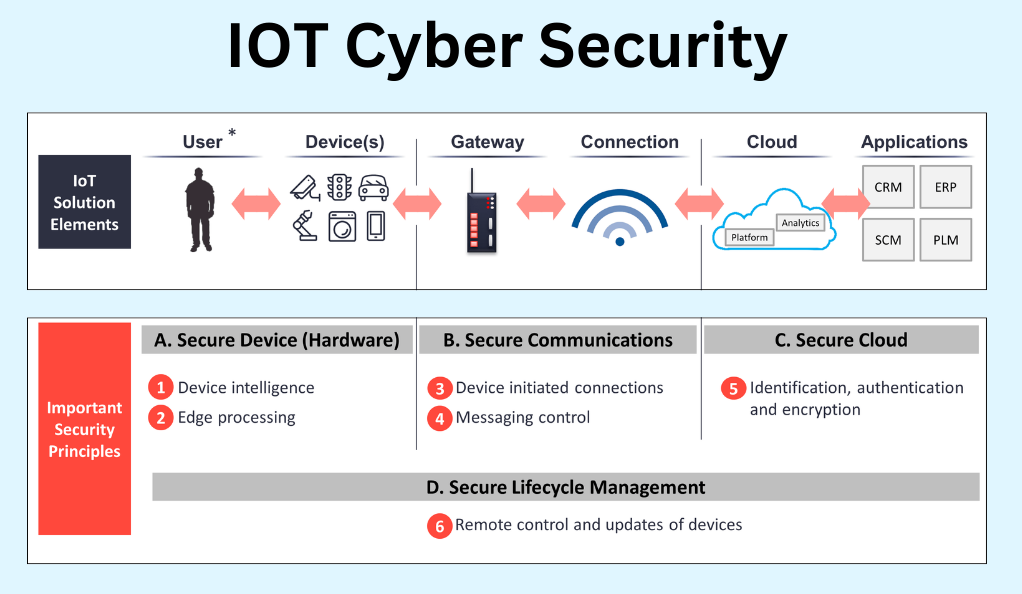
What is IoT Security?
IoT security refers to the protective measures and strategies employed to safeguard IoT devices and networks from potential threats. It encompasses the technologies, processes, and practices designed to protect IoT devices from unauthorized access, manipulation, or data breaches.
Why is IoT Security Important?
As the number of connected devices continues to grow exponentially, so does the potential attack surface for malicious actors. These devices, if compromised, can serve as entry points to larger networks, leading to data breaches, unauthorized surveillance, or even physical harm in the case of critical infrastructure.
Challenges in IoT Security
- Diverse Device Landscape: IoT devices come from various manufacturers, each with its own set of security standards and protocols. This diversity makes it challenging to have a unified security approach.
- Limited Device Capabilities: Many IoT devices have limited processing power and memory, making it difficult to implement robust security measures directly on the device.
- Long Device Lifespans: Unlike smartphones or computers that are frequently updated or replaced, some IoT devices, like smart thermostats or industrial sensors, can remain operational for years, making them vulnerable to evolving threats.
Key Components of IoT Security
- Device Authentication: Ensuring that only legitimate devices can connect to the network.
- Data Encryption: Encrypting data transmitted between devices to prevent interception.
- Regular Updates: Periodically updating device firmware to patch vulnerabilities.
- Network Security: Implementing firewalls and intrusion detection systems to monitor and protect network traffic.
Comparison Table: Traditional Security vs. IoT Security
| Aspect | Traditional Security | IoT Security |
|---|---|---|
| Focus | Mainly on data protection | Device, data, and network protection |
| Threat Landscape | Primarily malware and phishing | Diverse, including device tampering and network breaches |
| Update Frequency | Regular, with user prompts | Less frequent, often requiring manual intervention |
Best Practices in IoT Security
When it comes to ensuring the security of the Internet of Things (IoT), there are several best practices that experts recommend. One of the foremost steps is to change the default credentials that manufacturers provide with their devices. These default usernames and passwords are often common knowledge and can be easily exploited by malicious actors. To further enhance security, it’s advisable to segment networks, ensuring that IoT devices operate on dedicated networks that are separate from critical business systems. This isolation minimizes the risk of a compromised IoT device becoming a gateway to more sensitive parts of the network.
Additionally, continuous monitoring of device behavior is essential. By employing network monitoring tools, unusual or suspicious device activities, which could be indicative of a security breach, can be promptly detected and addressed.
Lastly, the human element cannot be overlooked. It’s imperative to educate and train everyone involved in the IoT ecosystem, from developers to end-users. By ensuring that they understand the significance of IoT security and adhere to established best practices, the overall security posture of the IoT environment can be significantly strengthened.
The Current State of IoT Security
The Internet of Things (IoT) has rapidly evolved, weaving itself into the fabric of our daily lives and the infrastructure of modern industries. However, as the number of connected devices surges, so do the security challenges associated with them. Let’s delve into the current state of IoT security, examining its complexities, challenges, and the measures being taken to fortify it.
The Landscape of IoT Security
IoT security is a multifaceted domain that encompasses various devices, from household appliances to industrial sensors. Each device, depending on its function and manufacturer, presents unique security considerations.
Challenges in the Current IoT Security Framework
- Diverse Ecosystem: The IoT landscape is vast and varied. Devices from different manufacturers, each with its own set of protocols and standards, make it challenging to implement a one-size-fits-all security solution.
- Resource Constraints: Many IoT devices are designed to be cost-effective and energy-efficient, which often means they lack the computational power necessary for advanced security measures.
- Lack of Standardization: The IoT industry lacks a universal set of security standards, leading to inconsistent security implementations across devices.
Predominant Challenges in IoT Security
| Challenge | Implication |
|---|---|
| Diverse Ecosystem | Difficulty in creating unified security solutions. |
| Resource Constraints | Limited capability for advanced security features. |
| Lack of Standardization | Inconsistent security measures across devices. |
Notable Security Incidents
In the realm of IoT, there have been several significant security breaches that have drawn attention to the vulnerabilities of interconnected devices. One of the most impactful incidents was the Mirai Botnet Attack in 2016. This attack involved a massive Distributed Denial of Service (DDoS) assault, which was orchestrated using a botnet composed of infected IoT devices. This sophisticated attack managed to disrupt major internet platforms and services, causing widespread outages.
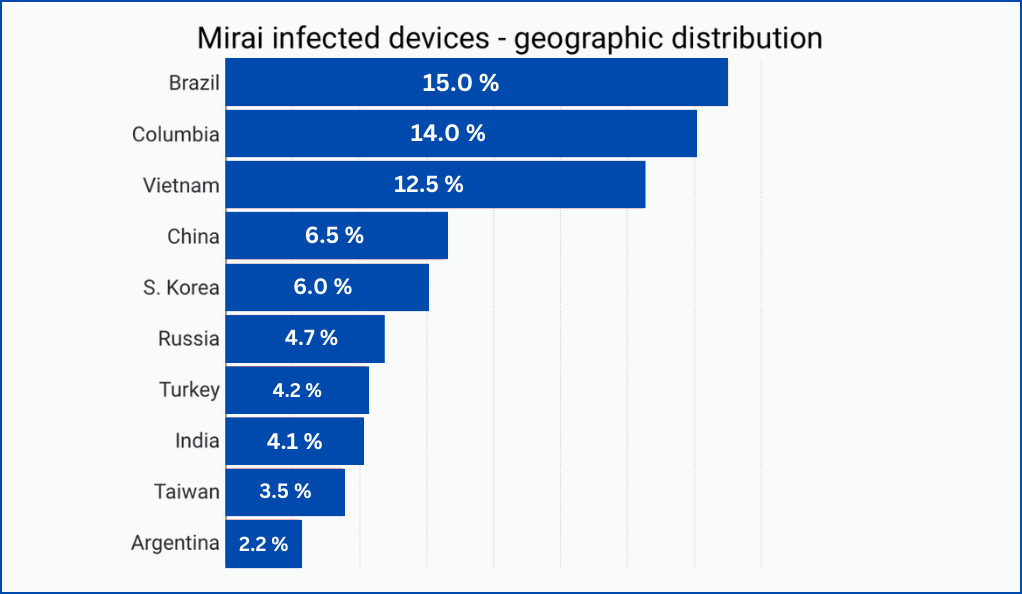
Additionally, the security of smart home devices has also been compromised in various instances. For example, there have been reported cases where hackers successfully infiltrated smart home devices, such as cameras and thermostats. These breaches not only disrupted the functionality of the devices but also posed significant privacy risks to users. These incidents serve as stark reminders of the potential security threats in the IoT ecosystem and emphasize the need for robust protective measures.
Initiatives and Progress in IoT Security
Recognizing the challenges and risks, various stakeholders in the IoT ecosystem are taking steps to bolster security:
- Industry Collaborations: Organizations are coming together to formulate standardized security guidelines for IoT devices.
- Advanced Encryption: Manufacturers are increasingly integrating advanced encryption techniques to secure data transmission between IoT devices.
- Regular Firmware Updates: To address vulnerabilities, manufacturers are rolling out regular firmware updates, ensuring devices are equipped to counter emerging threats.
Why IoT Security is Paramount
The Internet of Things (IoT) has ushered in an era of unprecedented connectivity, transforming industries and reshaping the way we live and work. However, with this vast network of interconnected devices comes a multitude of security concerns. Let’s explore why ensuring the security of IoT devices and networks is of paramount importance.
The Proliferation of IoT Devices
IoT devices are everywhere. From smart thermostats in our homes to sensors in industrial manufacturing plants, the number of connected devices is growing at an exponential rate. This widespread adoption amplifies the potential risks associated with security breaches.
Potential Risks and Threats
- Data Breaches: IoT devices often collect and transmit vast amounts of data. If not properly secured, this data can be intercepted, leading to breaches that can compromise personal and corporate information.
- Physical Threats: Devices controlling physical systems, like smart locks or industrial machinery, can be manipulated if hacked, leading to theft or even physical harm.
- Network Vulnerability: A compromised IoT device can serve as an entry point for attackers to infiltrate larger networks, potentially leading to more extensive breaches.
Key Threats in IoT Security
| Threat | Implication |
|---|---|
| Data Breaches | Compromise of personal and corporate data |
| Physical Threats | Potential for theft, damage, or harm |
| Network Vulnerability | Entry point for broader network breaches |
Economic and Reputational Implications
Security breaches can have severe economic consequences for businesses. Beyond the immediate financial losses, companies may face regulatory fines, legal actions, and a loss of customer trust. The reputational damage can have long-term implications, affecting customer loyalty and brand value.
The Complexity of the IoT Ecosystem
The IoT ecosystem is inherently complex. Devices from various manufacturers, each with its own set of protocols and standards, are interconnected. This diversity makes it challenging to implement uniform security measures, further emphasizing the need for robust security solutions.
The Future of IoT and Security
As the IoT landscape continues to evolve, the importance of security will only grow. The integration of AI and machine learning in IoT devices, the rise of edge computing, and the development of 5G networks will introduce new security challenges. Proactively addressing these challenges will be crucial to harness the full potential of IoT safely.
Challenges in IoT Security
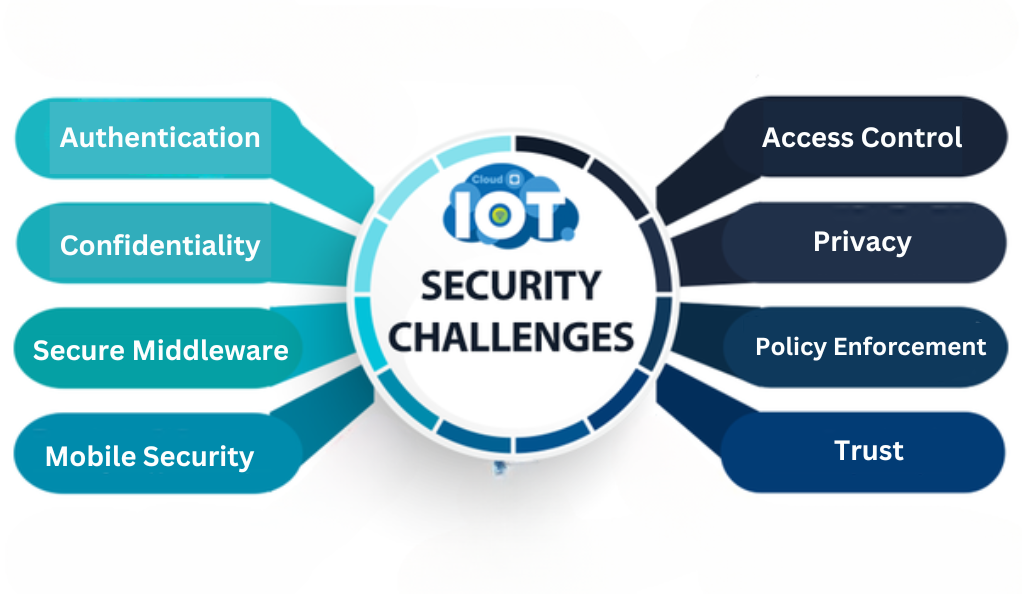
The Internet of Things (IoT) promises a future of seamless connectivity, with devices communicating and collaborating to make our lives more efficient and integrated. However, this vast interconnected landscape is not without its pitfalls. The security of IoT devices and networks is a pressing concern, and several challenges make it a complex issue to address. Let’s delve into the intricacies of these challenges.
Diversity of Devices and Standards
The IoT ecosystem is vast, encompassing everything from smart refrigerators and wearable fitness trackers to industrial sensors and medical devices. Each device type can come from various manufacturers, each with its own set of protocols, standards, and security measures. This diversity makes it challenging to implement a standardized security approach across the board.
Resource Constraints on Devices
Many IoT devices are designed to be lightweight and energy-efficient. This often means they have limited processing power and memory. Such constraints can make it difficult to run sophisticated security protocols or software, leaving them vulnerable to threats.
Inconsistent Updates and Patches
Unlike traditional IT systems, which often receive regular security updates, IoT devices can have varied and infrequent update schedules. Some devices might never receive an update post-deployment, leaving them exposed to known vulnerabilities for their entire operational lifespan.
Lack of User Awareness and Education
Many users are unaware of the potential security risks associated with IoT devices. This lack of awareness can lead to lax security practices, such as using default passwords, not updating device firmware, or indiscriminately connecting devices to insecure networks.
Complexity of IoT Networks
IoT networks can be intricate, with devices interconnected in various configurations. This complexity can make it challenging to monitor and secure every communication point, providing multiple potential entry points for malicious actors.
Comparison Table: Traditional vs. IoT Network Complexity
| Aspect | Traditional Network | IoT Network |
|---|---|---|
| Connectivity | Predominantly centralized | Highly decentralized |
| Monitoring | Easier due to fewer device types | Challenging due to device diversity |
| Entry Points | Limited and well-defined | Multiple, often undefined |
Physical Accessibility of Devices
Many IoT devices are deployed in easily accessible locations, making them vulnerable to physical tampering. An attacker with physical access to a device can potentially alter its functions, extract data, or introduce malicious software.
Interoperability Issues
IoT devices often need to communicate with devices from other manufacturers or run on different platforms. Ensuring secure interoperability without compromising functionality is a significant challenge.
Strategies for Addressing IoT Security Challenges
The Internet of Things (IoT) has brought forth a new era of connectivity, but with it comes a host of security challenges. As the number of IoT devices continues to grow, so does the urgency to implement robust security measures. Let’s explore the strategies being employed to address these challenges and ensure a safer IoT ecosystem.
Holistic Security Approach
A comprehensive security approach is essential, considering the multifaceted nature of IoT. This means looking beyond just device security and considering the entire ecosystem, including data transmission, storage, and user interfaces.
Device-Level Security
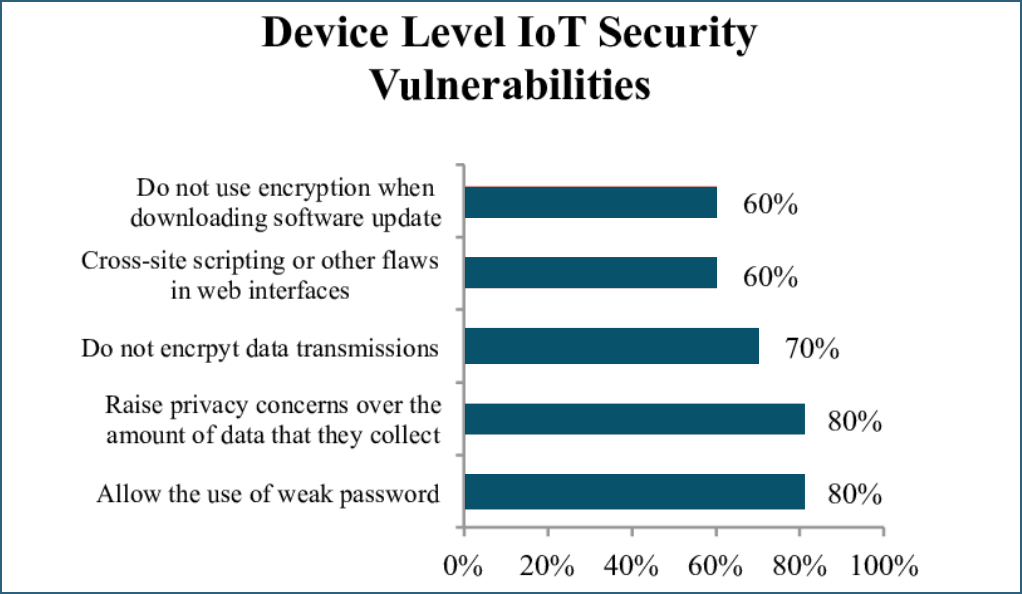
Device-level security is vital for the broader IoT ecosystem. Key strategies include hardware-based security features embedded directly into devices and mechanisms like secure boot processes. Regular firmware updates, especially over-the-air (OTA) ones, address vulnerabilities without extensive manual effort. Devices should come with default security features, and users should be prompted to change initial credentials. These measures enhance device security, mitigating many potential threats and establishing a foundation for a safer IoT landscape.
Network-Level Security
Network security is pivotal in the IoT domain. One key strategy is network segmentation, which isolates IoT devices onto dedicated networks, limiting potential breach impacts. Specialized firewalls, designed for IoT traffic, monitor and control data flow, while intrusion detection systems provide real-time threat alerts. Additionally, encrypting data, both at rest and in transit, ensures its protection even if intercepted. Together, these measures fortify the network, ensuring secure communication and operation of connected devices.
User Education and Training
- Awareness Campaigns: Manufacturers and industry bodies can run campaigns to educate users about the importance of IoT security.
- Training Modules: Offering training modules on device setup, maintenance, and best practices can empower users to take charge of their device security.
- Clear Documentation: Providing clear and concise user manuals that emphasize security can guide users in setting up and managing their devices securely.
Standardization and Collaboration
Collaborative efforts are shaping IoT security, with industry-wide standards ensuring consistency across devices. The open-source community accelerates vulnerability detection and patch development. Additionally, third-party audits validate and maintain the effectiveness of security measures, ensuring a comprehensive approach to safeguarding the IoT ecosystem.
Comparison Table: Individual vs. Collaborative Strategies
| Aspect | Individual Strategy | Collaborative Strategy |
|---|---|---|
| Scope | Limited to single manufacturer or device | Covers broader industry standards and practices |
| Speed | May be slower due to limited resources | Faster due to pooled resources and expertise |
| Consistency | Can vary widely between devices | More uniform across devices and manufacturers |
Adaptive Security Architecture
As IoT threats evolve, security measures should also adapt. An adaptive security architecture involves continuous monitoring, assessment, and evolution of security protocols based on emerging threats and vulnerabilities.
IoT Security Best Practices
The Internet of Things (IoT) has transformed the way we interact with the world around us, offering unparalleled convenience and efficiency. However, with the proliferation of IoT devices, ensuring their security becomes paramount. Let’s delve into the best practices that can be adopted to fortify the security of IoT devices and networks.
- Change Default Credentials
One of the most basic yet often overlooked steps is changing the default usernames and passwords that come with devices. Manufacturers often use generic credentials for ease of setup, but these are widely known and can be easily exploited. - Regular Firmware Updates
Ensuring that the device firmware is regularly updated is crucial. Manufacturers often release updates to patch known vulnerabilities. Users should either set their devices to update automatically or regularly check for updates. - Network Segmentation
Isolating IoT devices on separate networks can prevent a compromised device from affecting the entire system. For instance, smart home devices can be on a different network than personal computers or smartphones. - Implement End-to-End Encryption
All data transmitted between IoT devices should be encrypted. This ensures that even if data is intercepted, it remains unreadable to unauthorized entities. - Limit Device Permissions
IoT devices should operate on the principle of least privilege, meaning they should only have permissions essential to their function. This limits the potential damage in case of a breach. - Physical Security
Physical access to a device can lead to tampering. Devices, especially those deployed in public or easily accessible locations, should have measures to deter physical interference. - Monitor Device Behavior
Using monitoring tools to track device behavior can help in detecting anomalies. Any unexpected behavior can be a sign of a security breach and should trigger alerts. - Educate and Train Users
Awareness is a powerful tool. Users should be educated about the potential risks associated with IoT devices and trained on best practices to mitigate these risks. - Collaborate and Share Information
Manufacturers and users should collaborate and share information about potential threats and vulnerabilities. An informed community can respond faster to emerging threats. - Plan for Device End-of-Life
Every device has a lifecycle. Planning for a device’s end-of-life ensures that it doesn’t become a security liability when it’s no longer supported or updated.
Conclusion
The Internet of Things (IoT) has revolutionized our interaction with the digital and physical worlds, bringing both opportunities and security challenges. A holistic approach, involving manufacturers, developers, and users, is essential for addressing these challenges. By adhering to best practices, such as updating credentials and using encryption, we can enhance IoT security. As the IoT landscape evolves, proactive measures and collaboration are crucial to harness its benefits while mitigating risks, ensuring a secure and promising future for this transformative technology.








