In the digital age, our online activities are increasingly becoming targets for malicious software, commonly known as malware. This threat has escalated particularly in popular web browsers, where users spend a significant portion of their digital lives. Google Chrome, being one of the most widely used browsers, is often a prime target for these attacks. Understanding the nature and impact of malware in Chrome is crucial for maintaining a secure online presence.
Brief Overview of the Rising Threats of Malware in Browsers, Especially Chrome
Malware, a term that combines the words ‘malicious’ and ‘software’, refers to any software intentionally designed to cause damage to a computer, server, client, or computer network. In the context of web browsers like Chrome, malware can take various forms, from annoying adware that bombards users with unwanted ads to more sinister types such as spyware, which secretly monitors user actions. The threats have evolved over time, becoming more sophisticated and harder to detect.
With its extensive user base, Chrome offers a lucrative target for cybercriminals. Malware can infiltrate Chrome through various means, including malicious websites, unsecured extensions, and deceptive pop-up ads. Once infected, the browser may exhibit a range of issues like unexpected ads, redirection to harmful sites, or even theft of personal information.
The impact of such infections is not just limited to the annoyance or performance degradation of the browser. It extends to more serious concerns like privacy breaches, financial loss, and even identity theft. Hence, being aware of these rising threats and understanding how to combat them is not just advisable; it’s essential for anyone using Chrome for daily internet activities.
Understanding Malware in Chrome
Google Chrome, the widely used web browser, is not immune to the threats posed by malware. Malware in Chrome can significantly disrupt your browsing experience and compromise your online security. It’s essential to understand what malware is and how it affects your Chrome experience to effectively protect yourself and your data.
What is Malware?
Malware, short for malicious software, refers to any program or code designed to harm or exploit any programmable device, service, or network. It encompasses a variety of forms, including viruses, worms, trojan horses, ransomware, spyware, adware, and more. Malware intrudes upon a system with the intent of causing damage, stealing data, or creating chaos. It’s often disguised as legitimate software, making it tricky for users to identify before it’s too late. Malware can spread through email attachments, downloaded files, or even through compromised websites.
How Malware Affects Your Chrome Experience
When malware infects Chrome, it can manifest in several ways, each potentially harmful to your browsing experience and personal data:
- Browser Performance: Malware can slow down Chrome’s performance, causing unexpected crashes, unresponsive pages, and overall sluggishness.
- Unwanted Ads and Pop-ups: Adware-type malware floods your browser with continuous, often intrusive advertisements, significantly hampering your browsing experience.
- Redirects and Hijacks: Some malware types redirect your searches to different sites, often filled with more malware or phishing attempts.
- Information Theft: More dangerous forms of malware, like spyware, can steal sensitive information, including login credentials, credit card numbers, and personal data.
Understanding these signs is crucial in identifying and taking swift action against malware infections. Keeping Chrome updated, avoiding suspicious downloads, and using reliable antivirus software are proactive steps to safeguard your browser against these threats.
Common Types of Chrome Malware
Malware in Google Chrome manifests in various forms, each with its unique characteristics and risks. Understanding these common types of Chrome malware is essential for identifying and protecting against them effectively. Let’s look at some of the most prevalent forms: adware and browser hijackers, spyware and tracking cookies, and ransomware.
Adware and Browser Hijackers
Adware, short for advertising-supported software, is designed to display unwanted advertising on your browser. These ads often pop up unexpectedly, redirecting you to advertising sites or even injecting ads into web pages you visit. Browser hijackers take this a step further by altering your browser settings without your permission. They can change your homepage, default search engine, and even redirect your web traffic to malicious sites. While not always harmful, they significantly disrupt your browsing experience and can be challenging to remove.
Spyware and Tracking Cookies
Spyware is a type of malware that quietly collects information about your browsing habits, personal details, and even keystrokes. This data can be used for targeted advertising or more malicious purposes like identity theft. Tracking cookies, while not inherently malicious, can also be used to monitor and record your online activities. These cookies are often employed by advertisers to track your browsing history, leading to privacy concerns. Regularly clearing your cookies and using privacy-focused browser settings can help mitigate these risks.
Ransomware Attacks via Chrome
Ransomware is one of the most severe types of malware. It can encrypt your files, making them inaccessible, and then demand a ransom payment for their release. While traditionally targeting systems through email phishing, ransomware attacks have also been initiated through Chrome, often via malicious downloads or compromised websites. These attacks can be particularly damaging, potentially leading to loss of important data and financial losses. Ensuring regular backups and avoiding suspicious downloads are key to protecting against ransomware attacks.
Chrome Malware Trends 2024
In 2024, the landscape of Chrome malware has been shaped by several prominent trends and challenges:
- Zero-Day Vulnerabilities: Google Chrome has experienced significant security challenges, including zero-day vulnerabilities. For instance, CVE-2024-0519 involved an out-of-bounds memory access in Chrome’s V8 JavaScript engine, potentially allowing remote attackers to exploit heap corruption via a crafted HTML page. Google has responded to such threats by releasing critical updates. Users are advised to regularly update their Chrome browsers to the latest versions to protect against these vulnerabilities.
- Malware Types and Families: Key malware types in 2023, which are likely to persist in 2024, include loaders, stealers, and Remote Access Trojans (RATs). Loaders are significant due to their role in downloading and installing other malicious payloads, while stealers focus on stealing financial and personal data. RATs grant attackers remote control over infected devices and have varied malicious capabilities. Popular malware families include Remcos, AgentTesla, NjRAT, AsyncRAT, and the Redline stealer, with the latter being particularly notable for its extensive functionalities and malware-as-a-service model.
- Techniques, Tactics, and Procedures (TTPs): Attackers often employ tactics like mimicking legitimate file names and exploiting legitimate Windows components (e.g., Rundll32) to execute malicious code. Techniques like using the Windows Command Shell to execute commands on compromised systems are also prevalent. These methods are expected to remain popular in 2024.
- Ransomware Trends: The ransomware landscape continues to evolve, with a notable increase in Ransomware-as-a-Service (RaaS) platforms that allow easy execution of ransomware attacks. Double extortion techniques, where attackers threaten to publish stolen data, have become more common. The expansion of remote work infrastructure has also opened new vulnerabilities that attackers are exploiting. Additionally, there’s a growing preference for cryptocurrency payments in ransomware transactions due to the anonymity and difficulty in tracing such payments.
- Mobile Threats and Overall Malware Statistics: Interestingly, mobile threats have been in decline, with fewer malicious installation packages detected in recent times. However, malware attacks continue to have a significant impact on businesses, especially those in the early stages of implementing cloud security solutions. The cost of breaches can vary greatly depending on the maturity of an organization’s cybersecurity infrastructure.
Recognizing Malware Symptoms in Chrome
Detecting malware in Chrome can be challenging, as its symptoms are often subtle and easily overlooked. However, being aware of certain signs can help you identify a malware infection early, preventing further damage and safeguarding your data. Common indicators include unexpected ads and pop-ups, browser redirections, and slow performance or crashes.
Unexpected Ads and Pop-ups
One of the most noticeable signs of malware in Chrome is the sudden appearance of ads and pop-ups that weren’t there before. These can be particularly intrusive, showing up even on websites that typically don’t display many ads. They might promote suspicious products or lead you to unsafe websites. If you notice an increase in these ads or pop-ups, especially if they appear on sites known for minimal advertising, it could be a sign that your browser has been compromised.
Browser Redirections
Malware can also cause your browser to redirect you to different websites, often without your consent. This symptom is particularly common with browser hijacker malware, which changes your browser settings. You might find your homepage or search engine altered, or you might be taken to unfamiliar web pages when clicking on familiar links. These redirections not only disrupt your browsing experience but can also lead you to phishing or malicious sites.
Slow Performance and Crashes
Another symptom of malware in Chrome is a noticeable slowdown in browser performance. If Chrome starts to lag, takes longer than usual to load pages, or frequently crashes, it could be due to malware overloading the browser’s resources. While performance issues can also stem from other causes, a sudden and unexplained decrease in speed or stability can indicate a malware problem, especially when combined with other symptoms like unexpected ads or redirections.
Preventive Measures to Avoid Malware
Protecting your Chrome browser from malware is not just about responding to threats, but also about proactively preventing them. Adopting preventive measures can significantly reduce the risk of malware infections, ensuring a safer browsing experience. Let’s explore some essential steps you can take to safeguard Chrome against malware.
Regular Browser Updates
Keeping your Chrome browser updated is one of the most effective ways to protect against malware. Each update often includes security enhancements and patches for vulnerabilities that malware could exploit. To ensure your browser is up-to-date, enable automatic updates in Chrome’s settings. This will allow Chrome to automatically download and install updates, ensuring you always have the latest security features and bug fixes.
Safe Browsing Practices
Safe browsing practices form the cornerstone of malware prevention. Be cautious about the websites you visit and the links you click on. Avoid downloading files or opening attachments from unknown or suspicious sources, as these are common ways malware gets distributed. Additionally, be wary of phishing attempts—emails or websites that try to trick you into providing personal information or downloading malware. Always verify the authenticity of requests for your information.
Utilizing Chrome’s Safety Features
Google Chrome comes equipped with various safety features designed to protect against malware. Utilize these features for enhanced protection:
- Safe Browsing: Chrome’s Safe Browsing warns you if you attempt to navigate to dangerous sites or download malicious files.
- Incognito Mode: While browsing in Incognito mode, Chrome doesn’t save your browsing history, cookies, site data, or information entered in forms.
- Extensions: Be selective about the extensions you install. Only use extensions from the Chrome Web Store and check the permissions they require.
- Security Check: Chrome’s built-in Security Check feature in settings can help you identify unsafe settings, passwords, and extensions.
Implementing these measures can significantly bolster your defenses against malware. Regular updates, cautious browsing, and making the most of Chrome’s inbuilt safety features are key strategies to maintain a secure online environment.
Step-by-Step Guide to Cleaning Chrome Malware
When your Chrome browser is infected with malware, it’s crucial to take immediate action to clean and secure it. This step-by-step guide will walk you through the process of identifying and removing malware from Chrome, ensuring your browsing experience is safe and secure.
Identifying Malware in Chrome
The first step in cleaning malware from Chrome is to identify if your browser is indeed infected. Look for common symptoms such as frequent pop-ups, unexpected ads, browser crashes, or your homepage and search engine being changed without your consent. Use reliable antivirus software to run a scan on your system, as it can detect and identify malware present in your browser.
Safe Mode and Backups
Before proceeding with the removal process, it’s wise to start your computer in Safe Mode, which runs your system with minimal programs and can prevent malware from hindering the cleaning process. Additionally, back up your important data. This ensures that your valuable files and information are safe in case something goes wrong during the malware removal process.
Updated Approach for Chrome Cleanup
While Chrome’s specific built-in cleanup tool may no longer be available, you can still take steps to clean your browser:
- Check for Malware Using Antivirus Software:
- Run a thorough scan using your antivirus program to detect and remove any malware from your system.
- Reset Browser Settings:

- Open Chrome, go to Settings > Advanced > Reset and clean up.
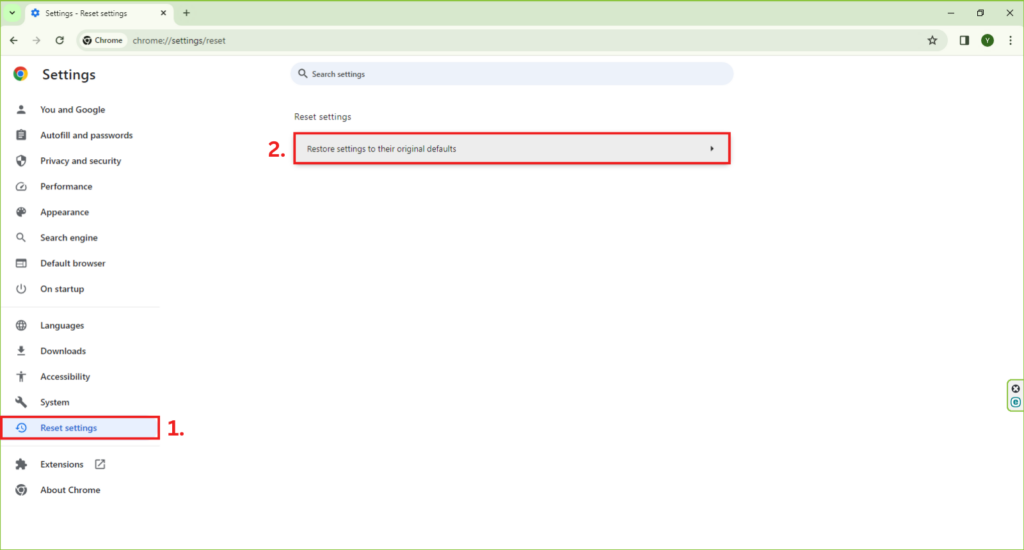
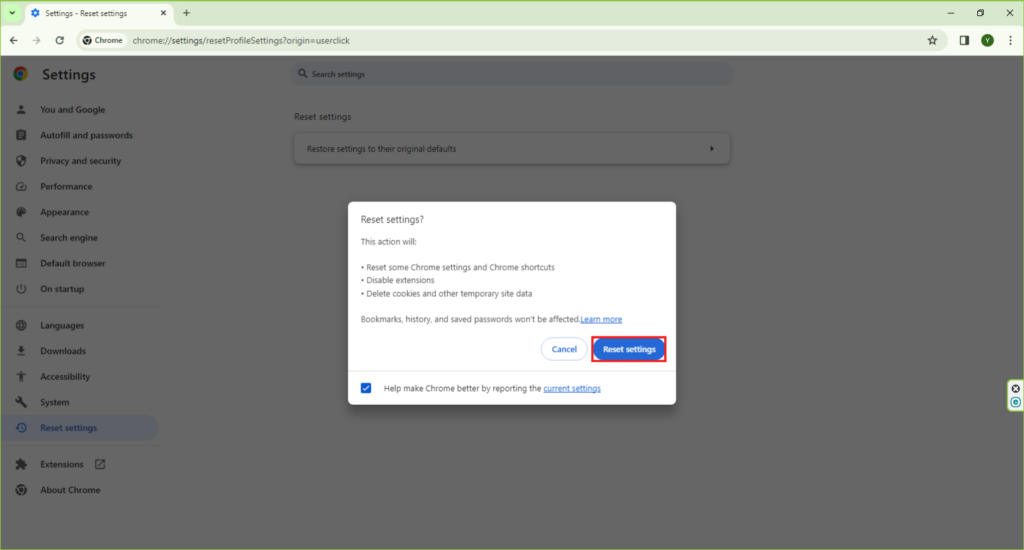
- Choose ‘Restore settings to their original defaults’ and click ‘Reset settings.’ This can help remove changes made by malware.
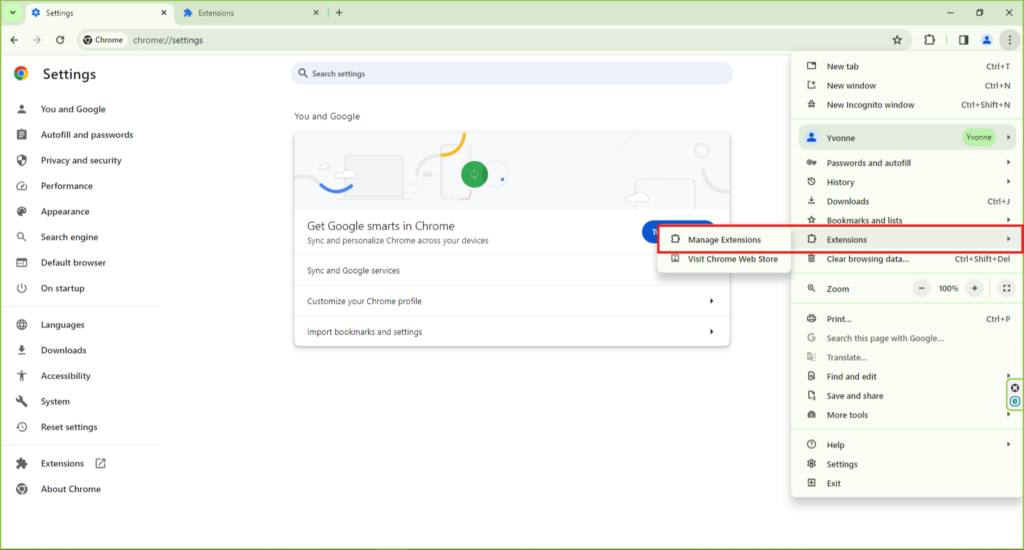
- Review Extensions and Settings:
- Go to Chrome Menu > More Tools > Extensions.
- Remove any extensions that you don’t recognize or remember installing.
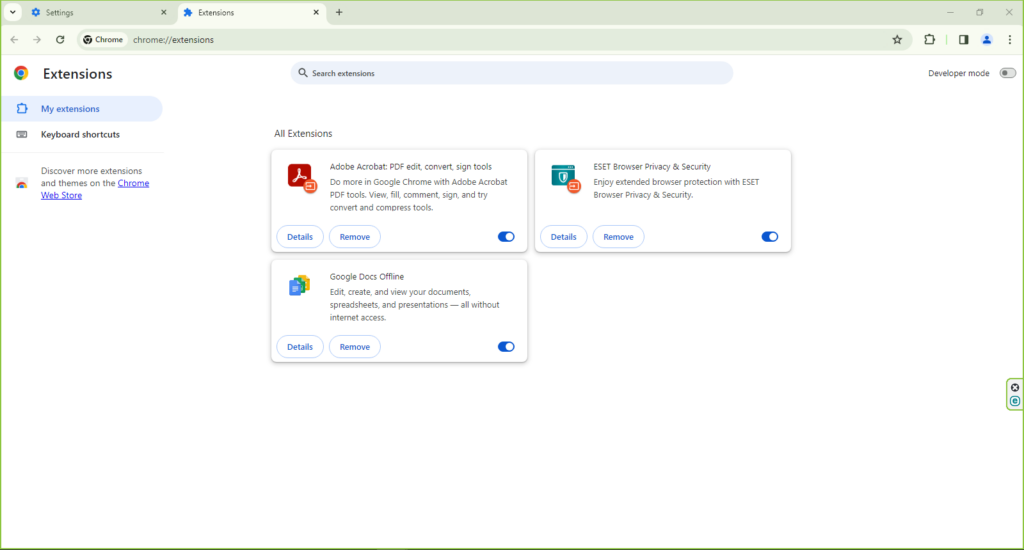
- Additionally, review Chrome’s privacy and security settings to ensure they haven’t been altered by malware.
Manual Removal Techniques
If you suspect that malware still persists:
- Reinstall Chrome: Uninstall and then reinstall Chrome to ensure all traces of malware are removed.
- Consult Professional Help: If the issue is not resolved, consider seeking help from a professional to ensure your system is free from malware.
By following these updated steps, you can effectively clean and secure your Chrome browser.
Post-Cleanup: Securing Your Chrome Browser
After successfully removing malware from Chrome, the next crucial step is to secure your browser to prevent future infections. This involves not only reinstating secure settings but also adopting practices and features that enhance your browser’s defense against malicious threats.
Advice on How to Secure Your Chrome Browser After Cleaning Malware
Once you’ve cleaned malware from Chrome, consider these tips to fortify your browser’s security:
- Update Your Browser: Ensure Chrome is updated to the latest version. Regular updates include security patches that protect against new threats.
- Review Extensions: Go through your Chrome extensions and remove any that are unnecessary or look suspicious. Stick to downloading extensions from the Chrome Web Store only.
- Change Passwords: If the malware could have compromised your passwords, change them, especially for sensitive accounts like email and banking.
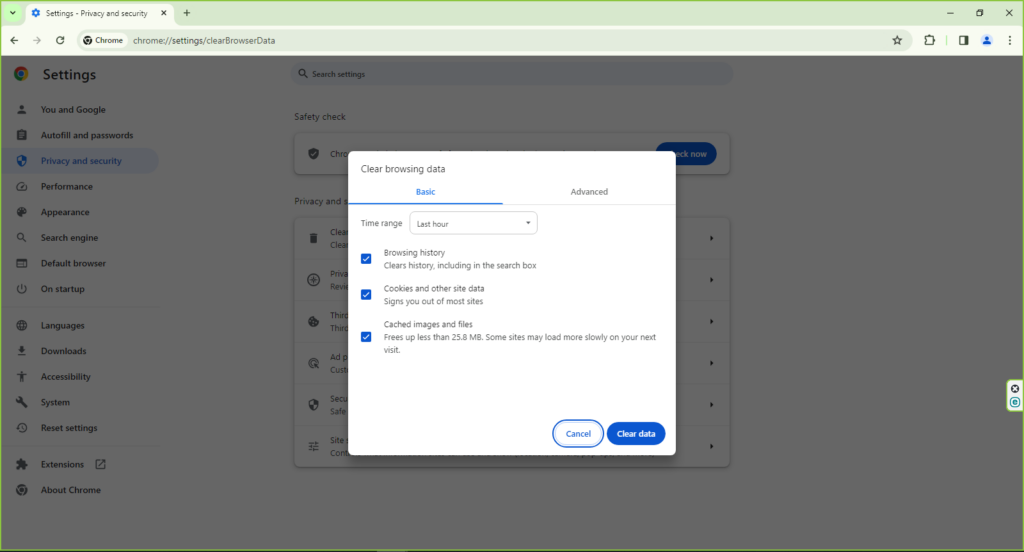
- Clear Browser Cache and Cookies: Regularly clear your browser cache and cookies. This can prevent tracking and remove residual data that might be malicious.
- Enable HTTPS-Only Mode: Use Chrome’s settings to ensure you are always using the HTTPS protocol, which is more secure than HTTP.
Setting Up Enhanced Protection Features in Chrome
Chrome offers several built-in features to enhance your online security. Activating these features can provide an additional layer of protection:
- Safe Browsing: Turn on the enhanced Safe Browsing feature in Chrome’s settings. This feature offers better protection against dangerous websites and downloads.
- Two-Factor Authentication (2FA): Enable 2FA for your Google account. This adds an extra layer of security beyond just your password.
- Security Check Feature: Regularly use Chrome’s Security Check feature in settings. It helps identify unsafe settings and alerts you about compromised passwords.
- Incognito Mode: Use Incognito Mode for sensitive browsing sessions. This mode does not save your browsing history or cookies.
By following these steps and regularly monitoring your Chrome browser for unusual activity, you can significantly reduce the risk of future malware infections and ensure a safer browsing experience.
Regular Maintenance and Best Practices
Maintaining your Chrome browser’s health is not a one-time task but a continuous process. Regular maintenance and adherence to best practices are vital in keeping Chrome free from malware and ensuring a secure browsing experience. It’s about forming habits that bolster your browser’s defenses against potential threats.
Emphasize the Importance of Regular Maintenance to Keep Chrome Malware-Free
Regular maintenance of your Chrome browser is crucial for its optimal performance and security. This includes:
- Updating Chrome: Always keep your browser updated to the latest version. Chrome updates include security patches that protect against new threats.
- Clearing Cache and Cookies: Periodically clear your browser’s cache and cookies. This helps in removing stored data that might be used for tracking or could become corrupted.
- Scanning for Malware: Use a trusted antivirus program to regularly scan your computer for malware. This is especially important if you’ve recently visited a suspicious website or downloaded an unknown file.
- Reviewing Extensions: Regularly review and manage your Chrome extensions. Remove any that are no longer needed or that you don’t remember installing.
Best Practices for a Safer Browsing Experience
To further ensure your safety while browsing, consider these best practices:
- Be Cautious with Downloads: Be wary of what you download. Avoid downloading files from untrusted sources or clicking on suspicious email attachments.
- Use Secure Connections: Whenever possible, use secure, encrypted connections. Look for ‘HTTPS’ in the website URL, especially when entering sensitive information.
- Enable Privacy Settings: Utilize Chrome’s privacy settings to control what data you share. Adjust settings like cookies, site data, and location access according to your preferences.
- Educate Yourself: Stay informed about common online threats and the latest security trends. Being knowledgeable helps you make better decisions about your online security.
By incorporating these maintenance tasks and best practices into your routine, you can significantly reduce the risk of malware infections and enjoy a safer, more secure browsing experience with Chrome.
Conclusion
Navigating the digital world safely requires constant vigilance, especially when it comes to protecting our browsers from malware. This guide has equipped you with the necessary knowledge to identify, remove, and prevent malware infections in Google Chrome. By understanding the types of malware, recognizing their symptoms, and following the step-by-step guide for removal, you can ensure your browser remains clean and secure. Moreover, implementing regular maintenance and best practices will fortify your defenses against future threats. Remember, the key to a secure browsing experience lies in staying informed, being cautious, and proactively managing your browser’s health. By adhering to these principles, you can enjoy the vast resources of the internet with peace of mind, knowing your digital space is well-guarded.








