The digital world is constantly evolving, and with it, the threats that lurk in the cyber realm grow more sophisticated every day. Cyber security is no longer just about protecting against viruses or hackers; it’s about safeguarding our digital identities, assets, and the integrity of our online infrastructure. As technology advances, so do the methods employed by cybercriminals, making the need for robust security measures more critical than ever.
Tailgating: A Subtle Yet Serious Threat
In the midst of various cyber threats, tailgating stands out for its simplicity and effectiveness. Tailgating in cyber security refers to the practice where unauthorized individuals gain access to restricted areas or information by following someone who is authorized. This technique doesn’t rely on sophisticated hacking skills but rather on exploiting human trust and oversight. Its impact can be significant, as it often leads to data breaches, loss of sensitive information, or unauthorized access to critical systems.
Understanding the Basics of Tailgating
Tailgating in the cyber world can take various forms. From someone peeking over your shoulder to view your computer screen to following closely behind you in a secure login process, these actions may seem harmless but can lead to significant security breaches. It’s a method that blends the physical and digital worlds, leveraging the slightest lapse in security protocols.
Why Tailgating Demands Attention
While it might seem less dramatic than other cybercrimes, the consequences of tailgating can be just as severe. It represents a unique challenge in cyber security – one that combines physical security breaches with digital consequences. Recognizing and addressing tailgating is crucial in developing a comprehensive security strategy that protects against both digital and physical vulnerabilities.
What Exactly is Tailgating in Cyber Security?
Tailgating in cyber security is often misunderstood due to its simplicity. It’s a method where unauthorized persons gain access to restricted or sensitive information by exploiting human nature or physical security lapses. Unlike complex cyberattacks that require technical know-how, tailgating is more about seizing opportunities presented by everyday behaviors and oversights. This can include scenarios like accessing a secured network by using someone else’s login credentials without their knowledge, or entering a restricted physical area by following closely behind an authorized person.
Physical vs. Cyber Tailgating: Understanding the Difference
While the concept of tailgating is straightforward, it’s essential to distinguish between its physical and digital manifestations.
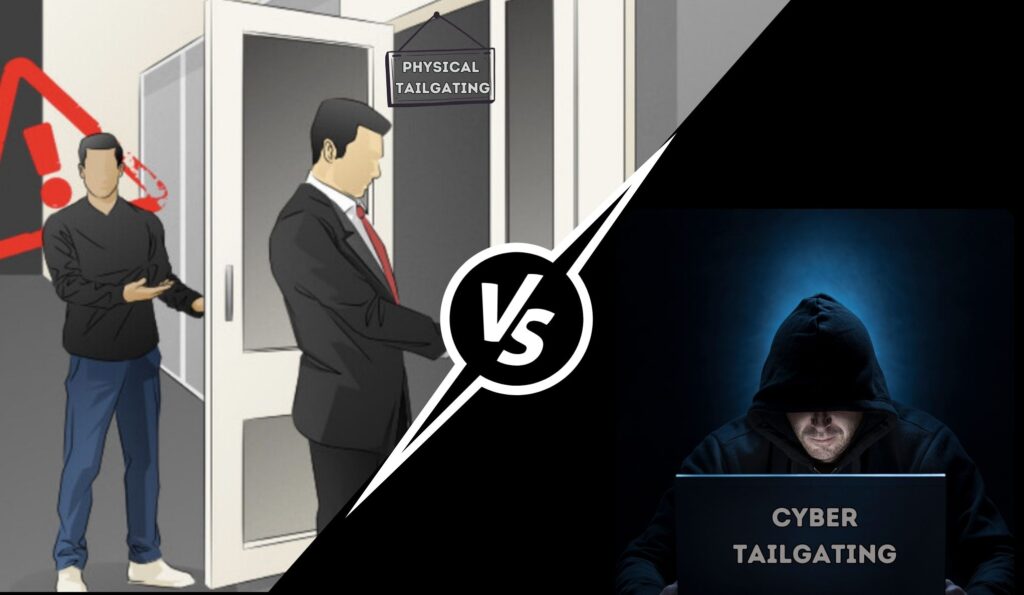
Physical Tailgating
Physical tailgating occurs when someone gains unauthorized access to a physical space, like an office or a data center, by following an authorized person. This type of tailgating relies on the social reluctance to confront or question, allowing the intruder to slip in unnoticed.
Cyber Tailgating
In contrast, cyber tailgating involves accessing restricted digital resources or information. It can happen when an individual observes another entering sensitive login information and then uses it to gain unauthorized access. This method preys on the digital equivalent of leaving the door open – using someone else’s credentials or a session that hasn’t been properly logged out.
Real-World Examples of Tailgating Attacks
To better understand the impact of tailgating in cyber security, let’s look at some real-world examples. These instances highlight how seemingly minor oversights can lead to significant security breaches.
- Example 1: The Overlooked Login
Consider a scenario where an employee in a company logs into a secure system and steps away without logging out. An unauthorized individual takes this opportunity to access sensitive information from the unattended workstation. This incident showcases how tailgating can occur due to simple human error, leading to potential data breaches. - Example 2: The Following Game
Another common example is in physical security settings, like secured office areas. An intruder might tailgate an authorized employee through a secure door, bypassing security measures like keycard access. This type of tailgating can lead to unauthorized physical access to sensitive areas, potentially compromising both physical and digital assets.
The Mechanics of a Tailgating Attack
Understanding the mechanics of tailgating attacks is crucial in recognizing and preventing them. These attacks often rely on the element of surprise and the exploitation of trust. For example, in a digital context, an attacker might observe when an employee types in their password and then use this information later to gain unauthorized access. In a physical setting, attackers might dress as service personnel and carry equipment to appear legitimate, making it easier for them to follow an employee through a secure door without question.
The Role of Social Engineering in Tailgating
A key component of tailgating attacks is social engineering, which involves manipulating individuals into breaking normal security procedures. Attackers often rely on the natural human tendency to avoid confrontation or to be helpful. For instance, an attacker might tailgate into a secure area while carrying heavy boxes, banking on the fact that someone will hold the door open for them. In the digital realm, social engineering can be as simple as creating a sense of urgency or exploiting the natural curiosity of individuals to prompt them to click on a malicious link or share their credentials.
Tailgating: A Blend of Physical and Digital Techniques
Tailgating attacks are unique in that they can bridge the gap between physical and digital security breaches. This dual nature requires a comprehensive understanding and approach to security, addressing both the physical security measures and the cyber security protocols in place.
Types of Tailgating Attacks in Cyber Security
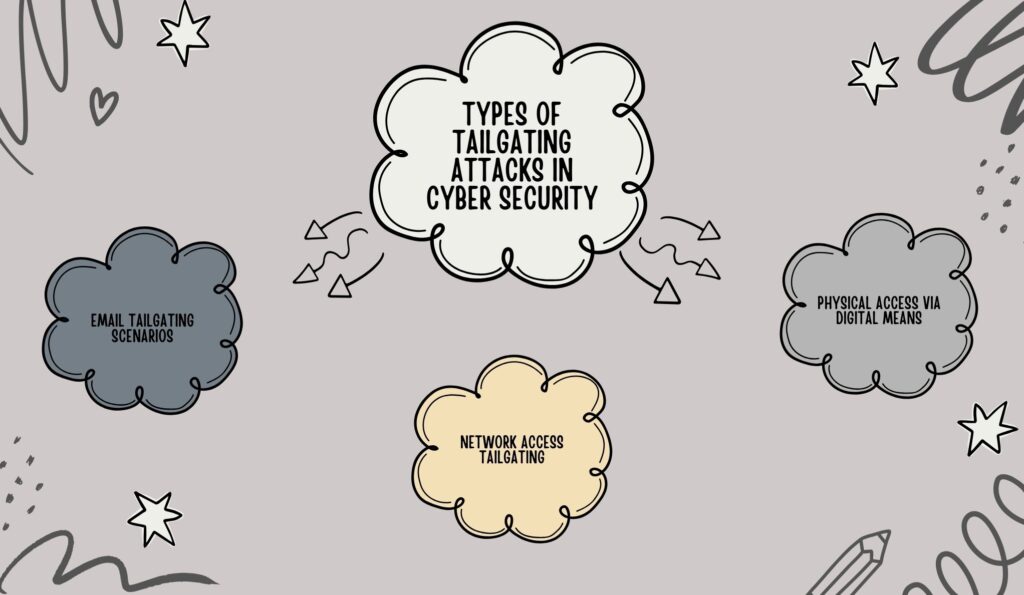
Tailgating attacks in cyber security can vary in their approach and execution. Understanding these variations is key to identifying and mitigating potential threats. Below are some common types of tailgating attacks:
- Email Tailgating Scenarios
Email tailgating involves attackers sending emails that appear to be from a trusted source. Recipients, believing the email is legitimate, might provide sensitive information or click on a link that grants attackers access to secure systems. This form of tailgating exploits trust in known contacts or authoritative entities. - Network Access Tailgating
This type involves gaining unauthorized access to a network by exploiting existing connections. For instance, an attacker might use the credentials of an authorized user who has left their computer unsecured. This type of attack is especially concerning because it allows the attacker to bypass many network security measures. - Physical Access via Digital Means
Here, attackers may use digital methods to gain physical access. This can include hacking into a security system to disable alarms or open electronic locks, or using social engineering to trick someone into granting physical access.
Strategies for Mitigating Tailgating Risks
Addressing these various forms of tailgating requires a multifaceted approach. This includes implementing stringent security protocols, regular security awareness training for employees, and advanced technical measures such as two-factor authentication and continuous monitoring of network access.
Prevention: Stopping Tailgaters in Their Tracks
Preventing tailgating attacks requires a combination of technical measures, employee training, and robust security policies. Here are some key strategies that can help mitigate the risk of tailgating:
- Enhanced Security Protocols
Implementing strong security measures like two-factor authentication, secure login procedures, and automatic session timeouts can significantly reduce the risk of digital tailgating. For physical security, measures like electronic access control systems, surveillance cameras, and security personnel can deter unauthorized access. - Employee Training and Awareness
Regular training sessions for employees are crucial. These sessions should cover the importance of security protocols, how to identify potential tailgating attempts, and the correct way to respond to them. Building a culture of security awareness within an organization is one of the most effective defenses against tailgating.
The Role of Technological Solutions
Technology plays a pivotal role in preventing tailgating. Advanced security systems that include intrusion detection, AI-powered surveillance, and access control systems can provide an additional layer of security. Regularly updating these systems and monitoring for unusual activity can help in early detection of tailgating attempts, both physically and digitally.
Creating a Secure Organizational Culture
Finally, fostering a secure organizational culture where every employee understands their role in maintaining security is essential. This involves clear communication of security policies, encouraging vigilance, and creating an environment where security concerns can be openly discussed and addressed.
Tailgating versus Other Cyber Threats
Understanding how tailgating differs from other cyber security threats helps in developing targeted strategies for its prevention. Tailgating, while less technologically sophisticated, can be just as damaging as more commonly known cyber threats.
- The Unique Challenge of Tailgating
Unlike threats such as malware or phishing, which are purely digital, tailgating can involve a physical component. This duality means that it requires a broader approach to security, encompassing both cyber security protocols and physical security measures. Tailgating is also unique in its reliance on exploiting human behavior, rather than technological vulnerabilities. - Tailgating vs. Phishing and Hacking
Phishing and hacking often require specific technical skills and involve direct attacks on a system’s security infrastructure. Tailgating, in contrast, often simply requires observation and the exploitation of everyday situations, making it a threat that is harder to detect and prevent using conventional cyber security tools.
Strategic Responses to Different Threats
The response to tailgating needs to be as unique as the threat itself. While technological solutions like firewalls and anti-virus programs are crucial in defending against hacking and malware, tailgating demands a more human-centered approach. This includes security awareness training, clear security policies, and a culture that prioritizes vigilance and responsibility.
FAQs
To further clarify the concept of tailgating in cyber security and its implications, this section addresses some frequently asked questions. Providing clear and concise answers helps in enhancing understanding and awareness of this security threat.
While hacking generally involves breaking into digital systems using technical methods, tailgating often relies on exploiting human behavior and physical security lapses. Tailgating can be as simple as following someone through a secured door or using someone else’s computer while they are away.
Detecting tailgating requires a combination of vigilance, technology, and process. Surveillance systems, entry logs, and anomaly detection tools can help identify unauthorized access. Additionally, fostering a security-conscious culture where employees are trained to spot and report suspicious behavior is crucial.
While it’s challenging to completely eliminate the risk of tailgating, combining robust security measures, technology, and employee training significantly reduces the likelihood of such attacks. Regular security audits and updates to security protocols also play a key role in prevention.
Conclusion
Tailgating in cyber security, a threat blending physical and digital vulnerabilities, emphasizes the need for a holistic security approach. This risk, leveraging human nature and operational lapses, can be mitigated with robust security protocols, technological solutions, and a culture of awareness. It’s not just about the latest technology but understanding human behavior, maintaining physical security, and fostering a vigilant workplace culture. The fight against tailgating is ongoing, requiring continuous education and empowerment of individuals to recognize and respond to security threats. A proactive security awareness environment helps create a resilient defense against the evolving landscape of cyber threats.