The Digital Era, often referred to as the Information Age, marks a significant shift from traditional industries established during the Industrial Revolution to an economy based on information technology. The onset of this era has transformed the way we live, work, and communicate, bringing forth a plethora of technological advancements and reshaping societal structures. This article delves deep into the evolution, characteristics, and implications of the Digital Era.
Evolution of the Digital Era
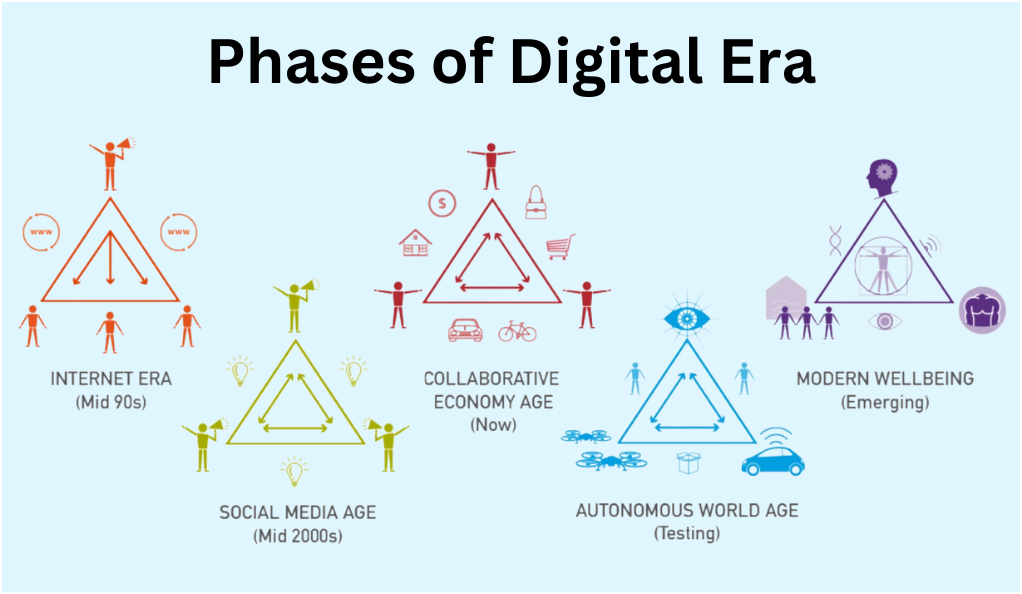
- Pre-Digital Age: Before the digital revolution, information was primarily stored and processed manually or through analog systems. Communication was limited to face-to-face interactions, letters, and landline telephones.
- Birth of Digital Technology: The 20th century witnessed the invention of digital computers, which laid the foundation for the digital revolution. The 1960s and 1970s saw the emergence of mainframe computers, followed by personal computers in the 1980s.
- Internet and Global Connectivity: The 1990s marked the rise of the internet and email, connecting people globally. This period also saw the birth of the World Wide Web, making information universally accessible.
Characteristics of the Digital Era
- Instantaneous Communication: With tools like email, instant messaging, and social media, communication is now real-time and boundary-less.
- Information Overload: The internet offers an abundance of information, leading to the challenge of filtering relevant from irrelevant data.
- Digital Storage: Gone are the days of physical storage; now, we have cloud storage, digital databases, and more.
- Interconnectivity: Devices are now interconnected through the Internet of Things (IoT), leading to smarter homes, cities, and industries.
Digital Era: A Comparative Analysis
| Aspect | Pre-Digital Era | Digital Era |
|---|---|---|
| Communication | Letters, Face-to-face, Landlines | Emails, Social Media, Instant Messaging |
| Data Storage | Physical files, Paper | Cloud, Digital Databases |
| Information Access | Libraries, Newspapers | Search Engines, Digital News |
| Business | Traditional Brick and Mortar | E-commerce, Online Services |
Implications of the Digital Era
- Economic Shifts: The rise of tech giants like Google, Apple, and Amazon, and the decline of traditional industries.
- Social Transformations: Social media has redefined communication, leading to global communities and also challenges like cyberbullying.
- Educational Advancements: E-learning platforms, digital classrooms, and online certifications have transformed the educational landscape.
- Political Impacts: The role of digital platforms in elections, public opinion, and global politics.
Challenges in the Digital Era
- Cybersecurity: With the digital shift, threats like hacking, phishing, and cyber espionage have emerged.
- Privacy Concerns: Data breaches and unauthorized data collection pose significant privacy risks.
- Digital Divide: The gap between those with access to digital technologies and those without, leading to inequalities.
The Future of the Digital Era
The future holds even more advancements, with technologies like Artificial Intelligence (AI), Quantum Computing, and Augmented Reality (AR) on the horizon. These will further redefine the boundaries of what’s possible in the Digital Era.
Understanding Incident Response Plans (IRP)
In the realm of cybersecurity, Incident Response Plans (IRP) stand as a beacon of preparedness and resilience. As cyber threats evolve in complexity and frequency, the need for a structured and comprehensive approach to address potential security breaches becomes paramount. This article delves into the intricacies of IRPs, shedding light on their significance, structure, and implementation.
What is an Incident Response Plan (IRP)?
An Incident Response Plan is a well-documented strategy outlining the processes to follow when a cybersecurity incident occurs. These incidents can range from a minor configuration error to a full-blown cyberattack. The primary goal of an IRP is to handle the situation in a way that limits damage and reduces recovery time and costs.
The Need for an IRP
- Rising Cyber Threats: The digital landscape is riddled with threats, from ransomware to phishing attacks, making IRPs essential.
- Regulatory Compliance: Many industries mandate the need for a robust IRP to meet data protection standards.
- Reputation Management: A swift and effective response to incidents can protect an organization’s reputation and customer trust.
Key Components of an IRP
- Preparation: This involves setting up an incident response team, defining roles, and ensuring all necessary tools and resources are in place.
- Detection and Analysis: Continuous monitoring to detect and analyze potential security threats.
- Containment: Short-term and long-term measures to contain the incident and prevent further damage.
- Eradication: Finding the root cause of the incident and completely removing the threat from the environment.
- Recovery: Restoring and validating system functionality for business operations to resume.
- Lessons Learned: After handling the incident, the team should meet to discuss what went well, what could be improved, and how to prevent future incidents.
Implementing an IRP
- Risk Assessment: Understand the potential risks and vulnerabilities in the organization.
- Training and Awareness: Regularly train staff on the IRP and conduct mock drills.
- Communication Strategy: Define how and when to communicate during an incident, both internally and externally.
- Review and Update: Technology and threats evolve; the IRP should too. Regularly review and update the plan.
Challenges in Incident Response
- Rapidly Evolving Threats: Cyber threats are constantly evolving, making it challenging to stay ahead.
- Coordination: Ensuring all stakeholders are aligned during an incident can be challenging, especially in large organizations.
- Resource Limitations: Not all organizations have the necessary resources or expertise to manage sophisticated threats.
The Future of Incident Response
With advancements in AI and machine learning, future IRPs will likely incorporate more automation, allowing for quicker detection and response. Additionally, as regulations around data protection become stricter, IRPs will play an even more crucial role in compliance.
Why Incident Response is Non-Negotiable
In the vast expanse of the digital universe, cyber threats loom large, casting shadows on organizations and individuals alike. With the increasing sophistication of these threats, the importance of a proactive stance in cybersecurity has never been more evident. At the heart of this proactive approach lies Incident Response (IR) – a structured methodology to address and manage the aftermath of a security breach or cyberattack. This article delves into the undeniable significance of Incident Response and why it’s an absolute imperative in today’s digital age.
The Evolving Cyber Threat Landscape
- Proliferation of Threats: From ransomware to Distributed Denial of Service (DDoS) attacks, the variety and volume of threats have surged.
- Sophistication and Stealth: Modern cyberattacks are not just frequent but also more sophisticated, often bypassing traditional security measures.
The High Stakes of Cyber Incidents
- Financial Implications: Beyond the immediate financial loss, cyber incidents can lead to regulatory fines and lost business opportunities.
- Reputational Damage: A security breach can erode trust, which might take years to rebuild.
- Operational Disruptions: Cyber incidents can halt business operations, leading to service disruptions and loss of productivity.
Incident Response: Beyond Just Recovery
- Proactive Detection: IR isn’t just about reacting; it’s about proactively identifying potential threats before they escalate.
- Structured Response: A well-defined IR process ensures that incidents are handled methodically, reducing the scope for errors.
- Learning and Adaptation: Post-incident analysis provides insights, helping organizations bolster their defenses against future threats.
The Regulatory and Compliance Angle
- Mandatory Reporting: Many regulations now require organizations to report breaches within a specified timeframe.
- Data Protection Standards: Regulations like GDPR emphasize the importance of safeguarding user data, making IR crucial.
- Avoiding Penalties: A robust IR strategy can help organizations avoid hefty fines associated with non-compliance.
The Human Element
- Employee Training: Well-trained employees can act as the first line of defense, identifying and reporting anomalies.
- Stakeholder Communication: Transparent communication during and after an incident can help manage stakeholder expectations and maintain trust.
Incident Response as a Business Enabler
- Customer Trust: Demonstrating a proactive approach to cybersecurity can enhance customer trust and loyalty.
- Competitive Advantage: In a market where data breaches are frequent, robust cybersecurity can be a differentiator.
- Operational Resilience: A swift and effective IR ensures that business operations are disrupted minimally.
Key Components of an Effective Incident Response Plan
In the intricate maze of cybersecurity, an Incident Response Plan (IRP) serves as a guiding light, illuminating the path to navigate and counteract potential cyber threats. An effective IRP is not just a document; it’s a dynamic strategy that evolves with the threat landscape. This article delves deep into the essential components that constitute an effective IRP, ensuring that organizations are well-prepared to confront and mitigate cyber incidents.
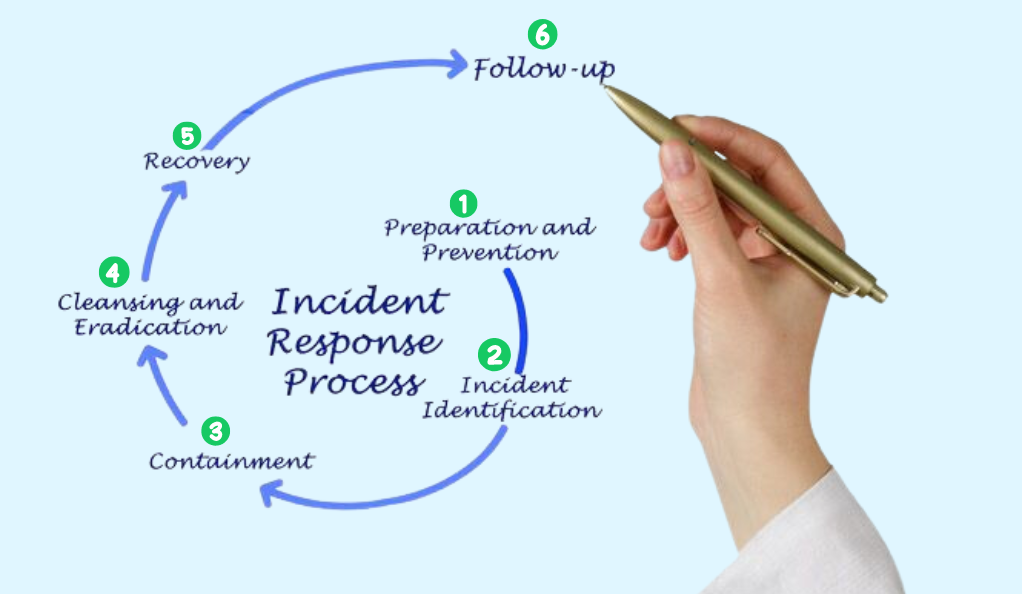
Preparation: Laying the Groundwork
- Incident Response Team (IRT): Identify and assemble a team of experts, each with defined roles and responsibilities, to handle potential incidents.
- Tools and Infrastructure: Equip the IRT with the necessary tools, technologies, and infrastructure to detect, analyze, and counteract threats.
- Training and Drills: Regularly train the IRT and conduct simulated cyberattack drills to test and refine the response strategy.
Detection: The First Line of Defense
- Monitoring Systems: Implement continuous monitoring systems to detect anomalies and potential threats in real-time.
- Alert Mechanisms: Establish mechanisms to alert the IRT of potential incidents, ensuring swift initiation of the response process.
- Threat Intelligence: Stay updated with the latest threat intelligence to recognize new and evolving cyber threats.
Analysis: Understanding the Threat
- Incident Classification: Categorize the incident based on its severity, type, and potential impact.
- Root Cause Analysis: Determine the origin and cause of the incident to understand its nature and scope.
- Impact Assessment: Evaluate the potential damage the incident can cause to the organization’s assets, reputation, and operations.
Containment: Limiting the Damage
In the realm of cybersecurity, the containment phase plays a pivotal role in limiting the damage of a cyber incident. Initially, short-term measures are crucial, requiring the implementation of immediate actions to contain the incident and prevent any further damage or data loss. However, containment doesn’t end there. It’s equally vital to develop long-term strategies to ensure that the threat is not only addressed but also completely neutralized, preventing any possibility of its recurrence in the future. This two-pronged approach ensures a comprehensive response, safeguarding assets and data from persistent threats.
Eradication: Eliminating the Threat
Following the containment of a cyber incident, the next critical steps involve threat removal and system fortification. It’s imperative to not only contain the threat but to ensure its complete removal from the environment, eliminating any remnants that might pose future risks. However, merely removing the threat isn’t sufficient. The vulnerabilities that were exploited by the threat need to be addressed. This is where system patching comes into play. By updating and patching systems, organizations can seal off these vulnerabilities, fortifying their defenses against similar threats in the future. Together, these measures form a comprehensive strategy to not only counteract cyber threats but also to bolster the system’s resilience against future attacks.
Recovery: Restoring Normalcy
- System Restoration: Restore affected systems and data from backups, ensuring they are clean and uncompromised.
- Validation: Test the restored systems to ensure they are operational and free from vulnerabilities.
- Communication: Inform stakeholders about the incident’s resolution and the measures taken to prevent future occurrences.
Post-Incident Review: Learning from the Incident
- Incident Debrief: Conduct a thorough review with the IRT to discuss the incident, the response, and areas of improvement.
- Documentation: Document the incident, the response actions, and the lessons learned for future reference.
- Plan Refinement: Based on the insights from the review, refine and update the IRP to better handle future incidents.
The Broader Security Strategy
In the vast realm of cybersecurity, while tools and tactics like Incident Response Plans (IRP) are crucial, they are but one piece of a much larger puzzle. A holistic approach to security requires a broader strategy, encompassing a range of measures, practices, and philosophies. This article delves into the expansive landscape of the broader security strategy, highlighting its multifaceted nature and the importance of a comprehensive approach to digital protection.
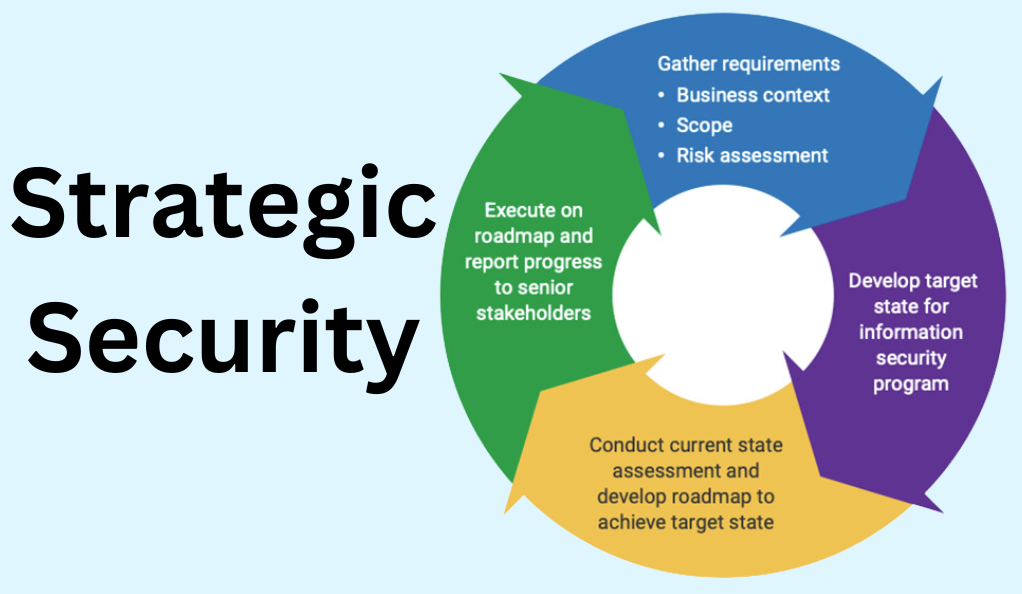
Understanding the Security Ecosystem
- Layers of Security: Recognize that security is multi-layered, from physical security to network, application, and data security.
- Interconnected Threats: Understand that vulnerabilities in one area can compromise the entire system.
- Evolving Landscape: Accept that the cyber landscape is dynamic, with threats and solutions constantly evolving.
Preventive Measures: Stopping Threats Before They Start
- Regular Audits: Conduct periodic security assessments to identify and rectify vulnerabilities.
- Patch Management: Ensure that all software, including operating systems and applications, are regularly updated.
- Employee Training: Educate employees about security best practices, from password hygiene to recognizing phishing attempts.
Detective Measures: Identifying Threats in Action
- Intrusion Detection Systems (IDS): Implement systems that monitor network traffic for suspicious activities.
- Security Information and Event Management (SIEM): Use advanced solutions that provide real-time analysis of security alerts.
- Behavioral Analytics: Employ tools that recognize abnormal user behaviors, indicating potential breaches.
Responsive Measures: Acting on Identified Threats
- Incident Response: As previously discussed, have a robust IRP in place to address and manage security incidents.
- Backup and Recovery: Ensure data is regularly backed up and can be quickly restored in case of breaches or failures.
Continuous Improvement: Adapting and Evolving
- Feedback Loops: Create mechanisms to learn from past incidents and integrate those lessons into the security strategy.
- Stay Informed: Keep abreast of the latest threats, trends, and technologies in cybersecurity.
- Regularly Update Strategy: As the organization grows and the digital landscape changes, revisit and revise the security strategy.
Collaboration and Integration
- Internal Collaboration: Foster communication between IT, operations, and business units for a unified security approach.
- External Collaboration: Engage with industry groups, governmental agencies, and other organizations to share knowledge and best practices.
- Integrated Security Solutions: Use solutions that integrate various security tools for a more cohesive defense strategy.
Beyond Technology: The Human and Organizational Aspect
- Security Culture: Cultivate a culture where every employee understands the importance of security and their role in it.
- Organizational Policies: Establish clear security policies, guidelines, and procedures that are regularly reviewed and updated.
- Leadership Commitment: Ensure that organizational leaders are committed to security, providing the necessary resources and emphasis.
The Business Implications of Incident Response
In today’s interconnected digital landscape, cybersecurity is not just an IT concern; it’s a business imperative. As organizations increasingly rely on digital platforms and data-driven strategies, the potential fallout from cyber incidents becomes not only technically challenging but also profoundly impactful on the business front. This article delves into the multifaceted business implications of incident response, highlighting the profound effects a cyber incident can have on an organization’s operations, reputation, and bottom line.
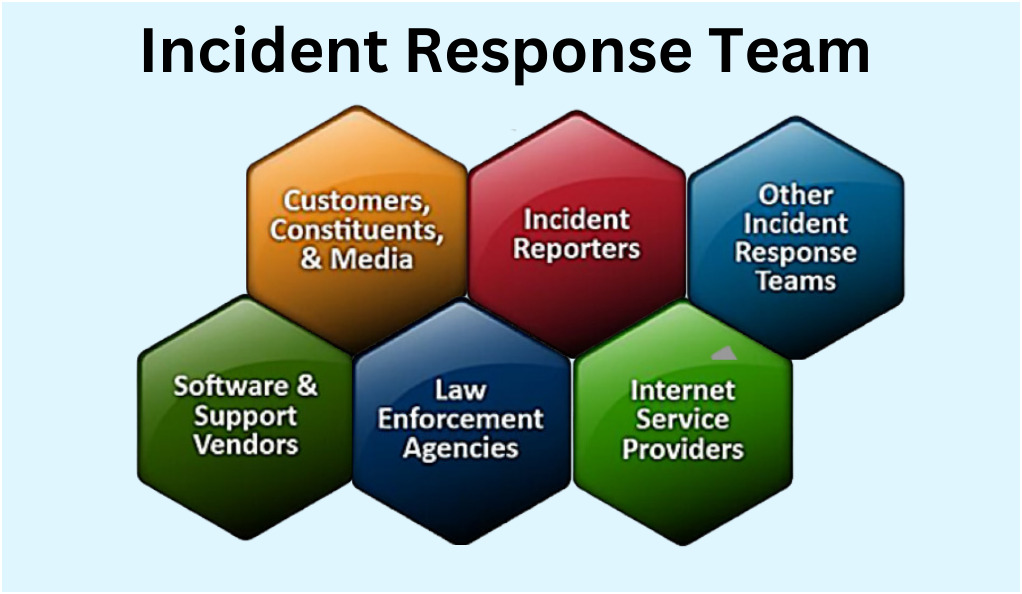
Financial Impact: The Immediate and Long-Term Costs
- Direct Costs: These include expenses related to incident detection, containment, eradication, and recovery. This might involve hiring external experts, purchasing new tools, or restoring lost data.
- Indirect Costs: Downtime, lost productivity, and potential legal fees can add up, impacting the organization’s financial health.
- Long-Term Financial Implications: A breach can lead to lost business opportunities, decreased stock value, and increased insurance premiums.
Reputational Damage: Erosion of Trust and Brand Value
- Customer Trust: A security incident can erode the trust customers place in an organization, leading to decreased loyalty and potential churn.
- Brand Perception: News of a breach can tarnish an organization’s image, making it harder to attract new customers or partners.
- Media and Public Relations: Handling media scrutiny and managing public relations post-incident can be challenging and resource-intensive.
Operational Disruptions: Halting the Business Engine
- Service Interruptions: Cyber incidents can disrupt services, leading to customer dissatisfaction and potential contract breaches.
- Supply Chain Disruptions: If suppliers or partners are affected, it can have cascading effects on an organization’s operations.
- Resource Diversion: Responding to an incident often requires diverting resources from other projects, impacting overall business productivity.
Legal and Regulatory Consequences: Navigating the Compliance Maze
- Regulatory Fines: Many industries have regulations that mandate specific cybersecurity measures and breach notifications. Non-compliance can lead to hefty fines.
- Lawsuits: Affected parties, be it customers or shareholders, might initiate legal actions against the organization.
- Contractual Obligations: Breaches might lead to violations of contractual agreements with partners or customers, leading to penalties or terminations.
Strategic Implications: Rethinking Business Directions
- Re-evaluation of Digital Initiatives: Post-incident, organizations might need to reassess their digital strategies, potentially delaying or altering digital transformation initiatives.
- Investment Priorities: Increased emphasis on cybersecurity might divert funds from other strategic investments.
- Market Positioning: Organizations might need to reposition themselves in the market, emphasizing security and trust.
Long-Term Business Resilience: Building a Stronger Future
- Learning from Incidents: Organizations can use incidents as learning opportunities, refining their strategies and bolstering defenses.
- Stakeholder Communication: Transparent and timely communication with stakeholders post-incident can aid in rebuilding trust.
- Future-Proofing: Investing in advanced cybersecurity measures post-incident can position the organization as a leader in security, turning a challenge into an opportunity.
Future of Incident Detection and Response
The digital frontier is in a constant state of flux. As technology evolves, so too do the threats that seek to exploit it. This ever-changing landscape necessitates a forward-looking approach to cybersecurity, especially in the realms of incident detection and response. This article delves into the anticipated advancements and trends that will shape the future of incident detection and response, offering a glimpse into the next generation of cybersecurity strategies and tools.
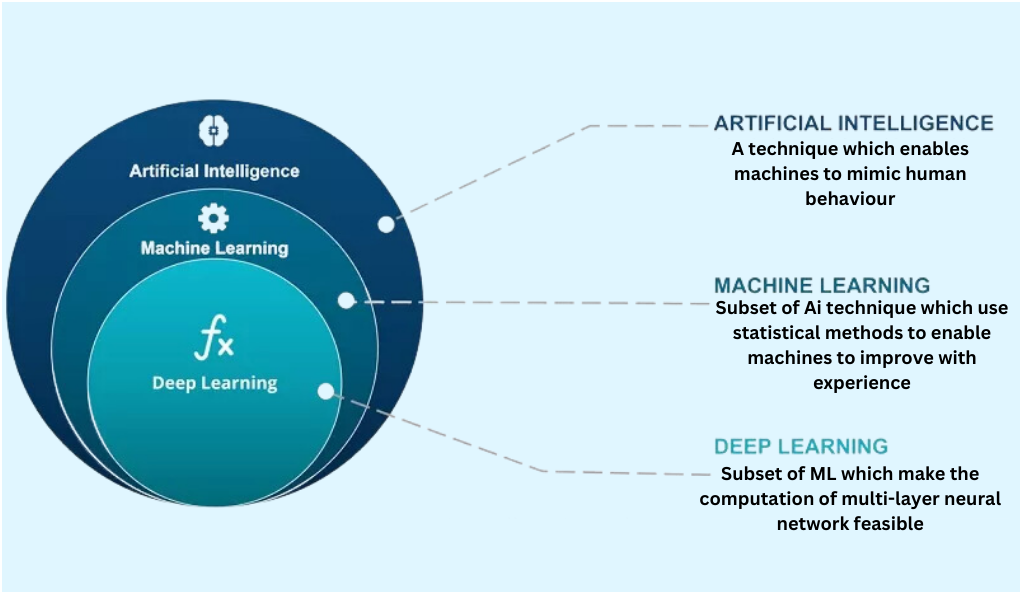
The Rise of Artificial Intelligence and Machine Learning
- Predictive Analysis: AI and ML can analyze vast amounts of data to predict potential threats before they manifest, shifting from a reactive to a proactive stance.
- Automated Response: Advanced algorithms can automatically respond to detected threats, reducing the time between detection and containment.
- Behavioral Analytics: By understanding ‘normal’ user behavior, AI can more accurately detect anomalies, reducing false positives.
Integration of Quantum Computing
- Enhanced Cryptography: Quantum computers have the potential to break traditional encryption methods but can also usher in a new era of quantum-safe cryptography.
- Speedier Threat Analysis: Quantum computing can analyze threats at unprecedented speeds, offering real-time insights.
Evolution of Threat Intelligence Platforms
- Real-time Threat Feeds: Future platforms will offer real-time global threat intelligence, allowing organizations to stay updated with emerging threats.
- Collaborative Defense: Organizations will increasingly share threat intelligence, fostering a collaborative defense approach against cyber adversaries.
Augmented Reality (AR) and Virtual Reality (VR) in Incident Response
- Virtual Cybersecurity War Rooms: AR and VR can create virtual spaces where incident response teams collaborate, irrespective of their physical location.
- Immersive Threat Visualization: Visualize threats and system vulnerabilities in a 3D virtual environment, enhancing understanding and response strategies.
Enhanced Digital Forensics
- Automated Evidence Collection: Advanced tools will automate the collection of digital evidence post-incident, ensuring accuracy and integrity.
- Deep Dive Analysis: New forensic tools will delve deeper into incidents, uncovering hidden threats and vulnerabilities.
The Growing Importance of Zero Trust Architectures
- Continuous Authentication: Instead of one-time logins, systems will continuously authenticate users based on behavior and other parameters.
- Micro-segmentation: Breaking networks into smaller segments, ensuring that breaches in one segment don’t compromise the entire system.
Emphasis on Human-Centric Security
- Regular Training: Recognizing that humans can be both the weakest link and the first line of defense, there will be an increased emphasis on regular cybersecurity training.
- Psychological Approaches: Understanding the psychology of attackers to predict and counteract their moves.
Regulatory Evolution and Global Collaboration
- Unified Global Standards: As cyber threats become a global concern, there may be a move towards unified international cybersecurity standards.
- Collaborative International Response: Countries and organizations will collaborate more closely to counteract major global cyber threats.
Conclusion
In our rapidly evolving digital age, cybersecurity stands as a cornerstone of trust and business continuity. As we’ve explored the multifaceted world of incident detection and response, the necessity for a proactive approach becomes evident. The dynamic nature of cyber threats requires organizations to be both technologically advanced and culturally aware. The fusion of human vigilance with cutting-edge technology is vital. As we move forward, continuous adaptation and collaboration will be key, ensuring that organizations not only counter threats but also thrive in the digital landscape.








