The digital age has ushered in an era where information is the new currency. As cyber threats continue to evolve, the importance of sharing information to bolster cyber defense has never been more critical. The concept of “information sharing” in the realm of cybersecurity isn’t just about disseminating data; it’s about fostering a collaborative environment where organizations, governments, and individuals can collectively combat cyber threats.
The Evolution of Cyber Threats
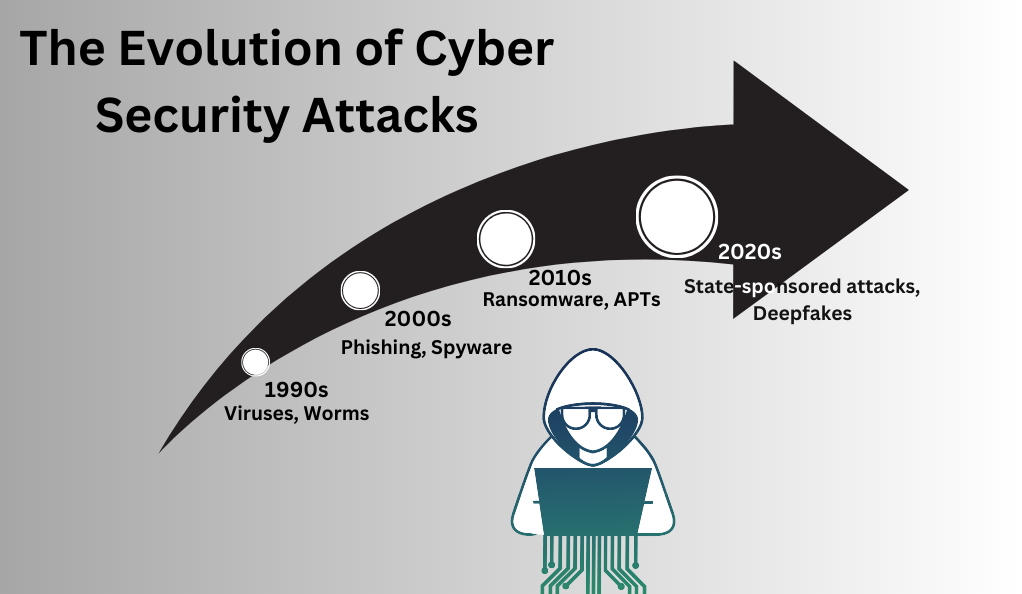
In the early days of the internet, cyber threats were relatively straightforward. They mostly consisted of viruses and worms, primarily aimed at causing disruptions rather than stealing data. Fast forward to today, and the landscape has drastically changed. Modern cyber threats range from sophisticated state-sponsored attacks to organized cybercrime rings targeting financial gains.
| Era | Primary Cyber Threats |
|---|---|
| 1990s | Viruses, Worms |
| 2000s | Phishing, Spyware |
| 2010s | Ransomware, APTs |
| 2020s | State-sponsored attacks, Deepfakes |
The Need for Collaborative Defense
No organization or government can single-handedly defend against the myriad of cyber threats. The sheer volume and sophistication of these threats necessitate a collaborative approach. By sharing threat intelligence, organizations can gain insights into emerging threats, allowing them to take proactive measures.
Comparison Table: Individual vs. Collaborative Defense
| Criteria | Individual Defense | Collaborative Defense |
|---|---|---|
| Scope of Threat Intel | Limited | Comprehensive |
| Response Time | Slower | Faster |
| Resource Requirement | High | Optimized |
| Success Rate | Variable | Higher |
Challenges in Information Sharing
While the benefits of information sharing are evident, several challenges hinder its full potential. These include concerns over privacy, potential legal liabilities, and the fear of revealing vulnerabilities. Addressing these challenges requires a balanced approach, ensuring that the shared information doesn’t compromise an organization’s integrity while still providing value to the broader community.
The Landscape of Cybersecurity Information Sharing
In the vast realm of cybersecurity, the landscape of information sharing has evolved to become a cornerstone of effective defense strategies. As cyber threats grow in complexity, the collective intelligence gathered from diverse sources provides a more holistic view of the threat environment. This section delves deep into the current state, mechanisms, and key players in cybersecurity information sharing.
The Genesis of Information Sharing
Historically, organizations operated in silos, guarding their cyber threat intelligence closely. The realization that cyber adversaries often target multiple entities using similar tactics led to the birth of collaborative defense. By pooling together threat intelligence, organizations found they could better predict, detect, and respond to cyber threats.
Key Mechanisms in Information Sharing
There are several mechanisms through which cybersecurity information is shared:
- Information Sharing and Analysis Centers (ISACs): These are sector-specific centers where companies share information about threats and vulnerabilities. For instance, the Financial Services ISAC focuses on threats specific to the banking and finance industry.
- Information Sharing and Analysis Organizations (ISAOs): Unlike ISACs, ISAOs aren’t sector-specific. They allow for broader sharing of information across different industries.
- Automated Indicator Sharing (AIS): This is a real-time sharing mechanism where threat indicators are shared automatically among participants.
- Public and Private Partnerships: Governments often collaborate with private entities to share threat intelligence, enhancing national cybersecurity.
| Mechanism | Scope | Speed | Participants |
|---|---|---|---|
| ISACs | Sector-specific | Variable | Industry members |
| ISAOs | Cross-sector | Variable | Various entities |
| AIS | Broad | Real-time | Tech companies, Governments |
| Public-Private | Broad | Variable | Governments, Private entities |
Key Players in the Landscape
Several entities play pivotal roles in the information-sharing ecosystem:
- Governments: National and regional governments often have dedicated cybersecurity agencies that gather, analyze, and disseminate threat intelligence.
- Private Corporations: Tech giants and cybersecurity firms often have vast resources dedicated to threat intelligence, which they sometimes share with the broader community.
- Non-Profit Organizations: Entities like the Cyber Threat Alliance work to improve the sharing of threat intelligence across the industry.
- Individual Researchers: Ethical hackers and independent researchers often uncover vulnerabilities or threats, sharing their findings with the affected parties or the public.
Benefits and Challenges
While the benefits of information sharing, such as enhanced threat detection and collaborative defense, are clear, challenges persist. Concerns over trust, data privacy, and potential misuse of shared information can hinder collaboration. Balancing the need for openness with these concerns is a continuous endeavor in the landscape of cybersecurity information sharing.
Benefits of Information Sharing
In the intricate web of cybersecurity, the act of sharing information isn’t merely a transaction; it’s a transformative process that amplifies the collective defense capabilities of all involved parties. The benefits of information sharing in cybersecurity are manifold, and they extend beyond just the immediate recipients of the information. This section delves into the multifaceted advantages that arise from proactive and collaborative information dissemination.
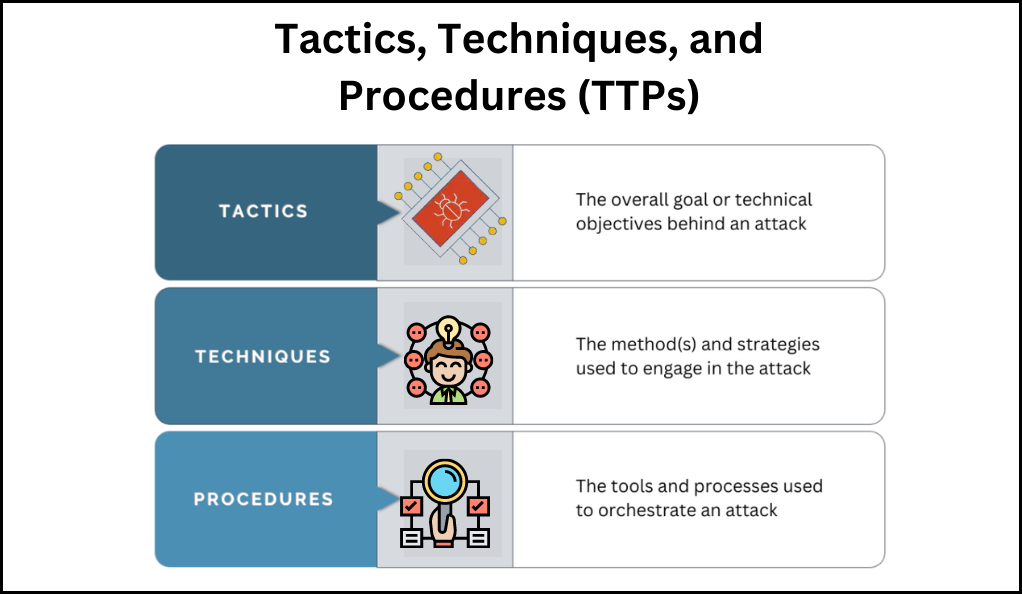
Proactive Defense Through Collective Intelligence
Proactive defense in cybersecurity is significantly bolstered through collective intelligence. When organizations come together to share threat intelligence, they amalgamate their knowledge, offering a more expansive view of the prevailing threat landscape. This pooled insight equips entities with the ability to better anticipate threats. By comprehending the tactics, techniques, and procedures (TTPs) employed by adversaries against similar targets, organizations can foresee and brace for potential attacks. Furthermore, the integration of shared indicators of compromise (IoCs) into detection tools amplifies their capability to identify threats, enhancing overall detection efficacy.
Cost Efficiency
Responding to cyber threats after a breach has occurred often incurs higher costs compared to preventing them in the first place. Shared information plays a pivotal role in mitigating these costs. Notably, it contributes to the reduction of incident response expenses. By preventing breaches or detecting them at an early stage, organizations can substantially diminish the financial impact associated with incident response efforts. Furthermore, the sharing of threat intelligence enables organizations to optimize their investments in security. With a clear understanding of prevalent threats, resources can be allocated more effectively to bolster defenses, ensuring a more robust and cost-efficient cybersecurity strategy.
Strengthened Community Resilience
The act of one entity sharing information about a threat or vulnerability extends its positive impact to the resilience of the entire community. This collective defense mechanism yields notable advantages. Firstly, it leads to a reduction in the number of successful attacks. As organizations fortify their defenses using the shared intelligence, potential adversaries encounter fewer vulnerable targets, resulting in a diminished success rate for attacks. Additionally, this collaborative approach serves as a powerful deterrent against cybercriminals. The presence of a united defense community makes adversaries rethink the cost-benefit ratio of their attacks. The increased risk of encountering a well-prepared and interconnected defense front can discourage cybercriminals from engaging in malicious activities, ultimately fostering a safer digital ecosystem.
Improved Regulatory Compliance
Amid various industries and regions, regulations that mandate or encourage information sharing have gained prominence. These regulations hold dual significance. Firstly, information sharing aids compliance efforts by helping organizations meet industry-specific mandates. By engaging in these initiatives, organizations ensure alignment with regulations, avoiding potential fines. Secondly, proactive information sharing strengthens stakeholder trust. Organizations openly exchanging threat intelligence demonstrate cybersecurity commitment, fostering confidence among customers, partners, and regulators.
In various sectors and geographic areas, regulations promoting information sharing have become prominent. These regulations hold a dual role. Initially, they aid compliance by assisting organizations in meeting industry-specific mandates. Participation ensures adherence, avoiding penalties. Additionally, proactive information sharing enhances stakeholder trust. Organizations openly sharing threat intelligence display cybersecurity dedication, building confidence among customers, partners, and regulators.
Fostering Innovation
Shared threat intelligence can also lead to innovation in defense strategies and tools:
- Collaborative Tool Development: Organizations can collaboratively develop or refine cybersecurity tools based on shared insights.
- Advanced Analytical Models: Shared data can be used to develop advanced analytical models for threat prediction and response.
Comparison Table: Solo vs. Collaborative Benefits
| Aspect | Solo Defense | Collaborative Defense |
|---|---|---|
| Threat Anticipation | Limited | Enhanced |
| Cost Efficiency | Variable | High |
| Community Resilience | Individual | Collective |
| Regulatory Compliance | Individual Effort | Collective Effort |
| Innovation | Limited | Amplified |
Barriers to Effective Information Sharing
While the benefits of information sharing in cybersecurity are undeniable, the journey towards achieving seamless and effective collaboration is riddled with challenges. These barriers, ranging from technical to socio-political, can hinder the flow of crucial threat intelligence between entities. This section delves into the myriad obstacles that organizations face in their quest for collaborative cyber defense.
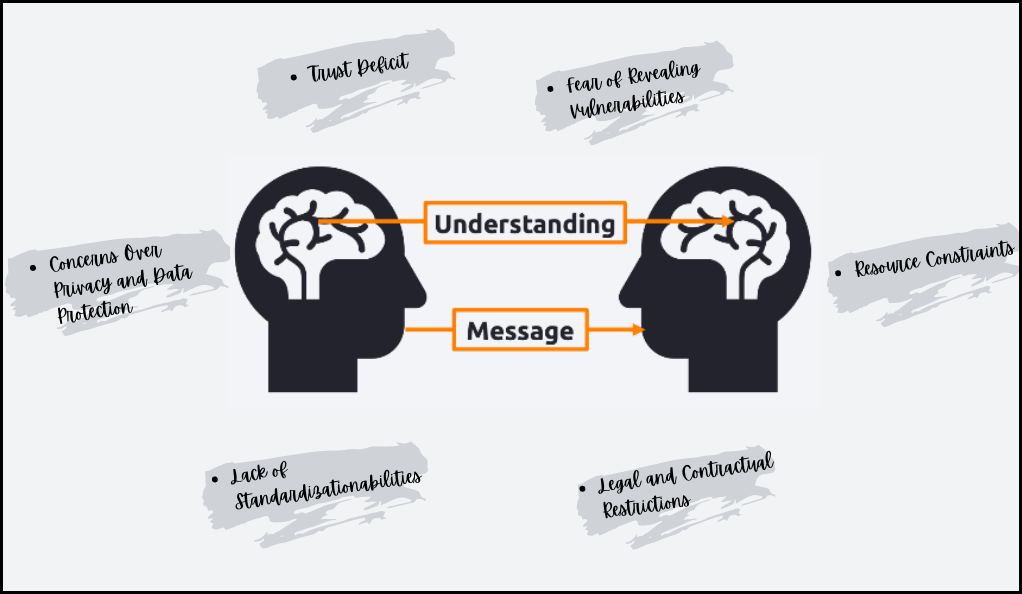
Concerns Over Privacy and Data Protection
One of the primary concerns when sharing information is the potential compromise of sensitive data:
- Personal Data Leaks: Sharing threat intelligence might inadvertently expose personal data, leading to privacy breaches.
- Regulatory Implications: Data protection regulations, such as GDPR, impose stringent requirements on data sharing, making organizations wary of potential non-compliance.
Fear of Revealing Vulnerabilities
Organizations often hesitate to share information about breaches or vulnerabilities due to:
- Reputation Damage: Admitting to a breach or vulnerability can harm an organization’s reputation, leading to a loss of customer trust.
- Competitive Disadvantages: Revealing vulnerabilities might give competitors an edge, especially if they exploit the disclosed weaknesses.
Lack of Standardization
The absence of standardized formats and protocols for sharing information can lead to:
- Inconsistent Data: Different organizations might represent threat intelligence in varied formats, leading to inconsistencies.
- Integration Challenges: Without standardization, integrating shared data into existing systems can be cumbersome.
Legal and Contractual Restrictions
Legal frameworks and contractual obligations can impede information sharing:
- Fear of Legal Repercussions: Organizations might face legal consequences if shared information leads to damages for other parties.
- Contractual Limitations: Contracts with third parties might prohibit the sharing of certain types of information.
Trust Deficit
Trust is a foundational element in information sharing, and its absence can be a significant barrier:
- Questionable Data Authenticity: Organizations might doubt the authenticity of shared data, fearing misinformation or decoys.
- Reluctance with New Partners: Building trust with new information-sharing partners takes time, slowing down the sharing process.
Resource Constraints
Effective information sharing requires resources, and not all organizations can allocate them:
- Lack of Dedicated Personnel: Some entities might not have dedicated staff for threat intelligence sharing.
- Technological Limitations: Without advanced tools and platforms, sharing information in real-time can be challenging.
Quantitative vs. Qualitative Approaches
In the realm of cybersecurity information sharing, the methodologies employed to analyze, interpret, and act upon data can vary significantly. Two primary approaches dominate this landscape: quantitative and qualitative. While both have their merits, understanding their distinctions and applications is crucial for effective threat intelligence. This section delves into the nuances of these approaches, highlighting their strengths, limitations, and optimal use cases.
Understanding Quantitative Approaches
Quantitative methods focus on data that can be measured and quantified. In cybersecurity, this often translates to:
- Metrics and Statistics: This includes data like the number of attempted breaches, frequency of specific types of attacks, or the average time to detect a threat.
- Structured Data Analysis: Quantitative approaches rely on structured data, such as logs, network traffic statistics, and other measurable indicators.
Strengths:
- Provides objective and measurable insights.
- Enables trend analysis and pattern recognition.
- Facilitates data-driven decision-making.
Limitations:
- Might overlook nuanced or contextual information.
- Requires substantial data for meaningful analysis.
Delving into Qualitative Approaches
Qualitative methods, on the other hand, focus on non-numerical data, offering a more descriptive and interpretative perspective:
- Human Intelligence (HUMINT): Insights derived from human sources, such as insider threat testimonials or hacker interviews.
- Contextual Analysis: Understanding the motivations, tactics, and objectives of cyber adversaries based on narratives and descriptions.
Strengths:
- Offers depth and context, providing a holistic view.
- Captures nuances, motivations, and subjective experiences.
- Enables understanding of complex and multifaceted threats.
Limitations:
- Can be subjective and open to interpretation.
- Might lack the precision and scalability of quantitative data.
Blending the Two: A Holistic Approach
For a comprehensive understanding of the cyber threat landscape, a blend of both approaches is often optimal:
- Quantitative Data for Baseline: Establishing a foundation with measurable metrics provides a clear picture of the threat environment.
- Qualitative Insights for Depth: Layering qualitative insights on top adds depth, context, and understanding to the quantitative baseline.
Comparison Table: Quantitative vs. Qualitative
| Aspect | Quantitative | Qualitative |
|---|---|---|
| Data Type | Numerical, Structured | Descriptive, Unstructured |
| Analysis Focus | Metrics, Patterns | Context, Motivations |
| Strengths | Objectivity, Scalability | Depth, Nuance |
| Limitations | Lack of context | Subjectivity |
| Use Cases | Trend analysis, Risk assessment | Threat actor profiling, Insider threat analysis |
Game-Theoretical Models in Cybersecurity
The intricate world of cybersecurity, with its ever-evolving threats and defenses, can often resemble a strategic game where players constantly adapt to outmaneuver their opponents. Game theory, a mathematical study of strategic interaction among rational players, has found increasing relevance in this domain. By modeling cybersecurity scenarios as games, experts can predict potential outcomes and devise optimal strategies. This section delves into the application of game-theoretical models in cybersecurity, exploring their significance, methodologies, and implications.
The Essence of Game Theory in Cybersecurity
At its core, game theory examines how players make decisions based on the anticipated actions of other players. In cybersecurity:
- Players: Typically, the defenders (e.g., organizations or governments) and attackers (e.g., hackers or cybercriminals).
- Strategies: The actions or sequences of actions chosen by players, such as deploying a specific defense mechanism or launching a particular type of attack.
- Payoffs: The outcomes or results of the strategies chosen by the players, often represented in terms of costs or benefits.
Common Game-Theoretical Models in Cybersecurity
- Zero-Sum Games: In these games, the gain (or loss) of one player is exactly balanced by the losses (or gains) of other players. For instance, if a hacker successfully breaches a system, they gain, while the organization loses.
- Non-Zero-Sum Games: Here, the total benefit to all players in the game can be more than or less than zero. Collaborative defense strategies, where multiple organizations share threat intelligence, can result in a net positive outcome for all involved.
- Sequential Games: These are games where players have a set order of play. For example, an organization might first deploy a defense, and then a hacker decides whether to attack.
- Simultaneous Games: Players make decisions at the same time. In cybersecurity, this could represent simultaneous moves by multiple threat actors and defenders.
Applications and Insights
- Optimal Defense Allocation: Organizations can use game theory to determine the best way to allocate their cybersecurity resources, considering potential attacker strategies.
- Understanding Attacker Motivations: By modeling attacker payoffs, defenders can gain insights into potential targets or methods of attack.
- Collaborative Defense Strategies: Game theory can help understand the benefits and potential pitfalls of collaborative defense, guiding organizations in forming alliances or sharing information.
Challenges and Limitations
While game-theoretical models offer valuable insights, they come with challenges:
- Assumption of Rationality: Game theory often assumes players are perfectly rational, which might not always be the case in real-world scenarios.
- Complexity: As the number of players or strategies increases, the models can become exceedingly complex.
- Incomplete Information: In many cybersecurity scenarios, players might not have complete information about the strategies or payoffs of others, leading to uncertainty.
Future Directions and Research Gaps
The dynamic realm of cybersecurity is in a perpetual state of evolution, driven by the relentless advancement of technology and the ingenuity of cyber adversaries. As the digital landscape expands and intertwines with every facet of modern life, the challenges and opportunities in cybersecurity research grow in tandem. This section explores the promising future directions in cybersecurity and highlights the existing research gaps that beckon exploration.
Emerging Trends in Cybersecurity

Several trends are poised to shape the future of cybersecurity:
- Quantum Computing: As quantum computers inch closer to reality, they bring the potential to revolutionize encryption, making many current cryptographic methods obsolete.
- Artificial Intelligence and Machine Learning: AI-driven cybersecurity solutions can detect and respond to threats in real-time, adapting to new challenges autonomously.
- Decentralized Systems: Technologies like blockchain offer decentralized security solutions, reducing single points of failure.
- Extended Reality (XR): As augmented and virtual realities become mainstream, new cybersecurity challenges and solutions specific to these platforms will emerge.
Research Gaps in Cybersecurity
While progress has been substantial, several research gaps remain:
- Human-Centric Security: While technology advances, the human element remains a weak link. Research into behavioral aspects of cybersecurity, from social engineering to insider threats, is crucial.
- Ethical Implications of AI in Security: As AI becomes integral to cybersecurity, understanding its ethical ramifications, from privacy concerns to decision accountability, is vital.
- Post-Quantum Cryptography: With quantum computers threatening current encryption methods, research into quantum-resistant cryptographic algorithms is of paramount importance.
- Security in IoT and Edge Computing: The proliferation of IoT devices and the shift towards edge computing bring unique security challenges that are yet to be fully explored.
Collaboration: Bridging Academia and Industry
One of the future directions in cybersecurity research is fostering closer ties between academic research and industry:
- Real-World Application: Collaborative efforts can ensure that academic research finds practical applications, addressing real-world challenges.
- Shared Resources: Industry can provide academia with resources, from datasets to infrastructure, facilitating more impactful research.
The Role of Policy and Regulation
Future research will also need to address the interplay between cybersecurity and policy:
- Global Cybersecurity Standards: As cyber threats know no borders, there’s a need for global standards and regulations.
- Balancing Security and Privacy: Research into frameworks that balance cybersecurity measures with individual privacy rights is increasingly relevant.
Conclusion
In the ever-evolving digital landscape, cybersecurity stands as a beacon of collective defense. Through our exploration of information sharing, game-theoretical models, and future directions, it’s evident that collaboration is key. While technological advancements promise enhanced security solutions, they also introduce new challenges. Overcoming barriers to information sharing, leveraging strategic game-theory insights, and addressing research gaps are crucial. As we navigate the digital age, our collective efforts in cybersecurity will determine the safety and integrity of our digital future.








