In the vast expanse of the digital universe, the threats of malware, phishing, and ransomware loom large, casting shadows over the safety and security of online users and organizations. As we increasingly rely on digital platforms for everything from communication to commerce, understanding these threats becomes paramount. This introduction aims to provide a foundational understanding of these cyber threats, setting the stage for a deeper exploration of each.
The Digital Landscape: A Double-Edged Sword
The digital age has ushered in unparalleled convenience and connectivity. However, with these advancements come vulnerabilities. As we integrate technology into every facet of our lives, we inadvertently open doors for cybercriminals to exploit.
| Advantages of Digital Age | Associated Risks |
|---|---|
| Instant Communication | Phishing Attacks |
| Online Banking | Financial Malware |
| Cloud Storage | Ransomware Attacks |
| Smart Devices | IoT Malware |
Defining the Threats
- Malware (Malicious Software): Software specifically designed to disrupt, damage, or gain unauthorized access to computer systems. It encompasses a range of threats from viruses to worms.
- Phishing: A cybercrime where targets are contacted by email, telephone, or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data.
- Ransomware: A type of malicious software designed to block access to a computer system until a sum of money is paid.
The Human Element
While technology plays a significant role, the human element cannot be ignored. Often, it’s human error—like clicking on a suspicious link or downloading an unverified attachment—that allows these threats to infiltrate systems.
The Global Impact
Cyber threats have a global impact, affecting individuals, businesses, and governments. The financial implications alone run into billions, not to mention the loss of trust, reputation, and data integrity.
Setting the Stage
As we delve deeper into the world of malware, phishing, and ransomware in subsequent sections, it’s essential to remember that knowledge is power. By understanding these threats, we can better equip ourselves to prevent, detect, and mitigate them.
The Evolution of Ransomware
Ransomware, a term that sends shivers down the spine of many IT professionals and business owners, has seen a meteoric rise in its prevalence and sophistication over the past few decades. From its humble beginnings as simple scareware to the advanced, state-sponsored attacks of today, ransomware has continually adapted to the changing digital landscape. This section will trace the evolution of ransomware, highlighting its major milestones and the lessons we’ve learned along the way.

- The Genesis: Early Days of Ransomware
In the late 1980s, the first known ransomware, the “AIDS Trojan,” was distributed via floppy disks. Victims found their files encrypted and were asked to pay a ransom to regain access. While primitive, this marked the beginning of a new era in cyber threats.
- The Rise of Encryption-based Attacks
The 2000s saw the emergence of encryption as a primary tool for ransomware. Cryptolocker, which surfaced in 2013, is a prime example. By encrypting users’ files with a nearly unbreakable code, attackers could demand higher ransoms with a greater assurance of payment.
- The Age of Ransomware-as-a-Service (RaaS)
With the increasing commoditization of cybercrime, ransomware became available “as a service.” Cybercriminals could now purchase ransomware kits on the dark web, enabling even those with limited technical skills to launch attacks.
- High-Profile Attacks and Their Global Impact
The mid-2010s were marked by a series of high-profile ransomware attacks. NotPetya, WannaCry, and Locky, among others, caused widespread disruption, targeting everything from individual computers to entire city infrastructures.
Notable Ransomware Attacks:
| Year | Ransomware | Impact |
|---|---|---|
| 2017 | WannaCry | Affected over 200,000 computers across 150 countries |
| 2017 | NotPetya | Estimated damages of over $10 billion |
| 2016 | Locky | Infected approximately 7% of global organizations |
- The Shift to Targeted Attacks
Recent years have seen a shift from widespread, scattergun attacks to more targeted ransomware campaigns. These attacks often focus on specific industries or organizations, such as healthcare or municipal governments, where the urgency to regain access to data is high.
- The Double Extortion Trend
A more recent trend in ransomware attacks involves not just encrypting data but also threatening to release it publicly. This “double extortion” method puts additional pressure on victims to pay the ransom, as they must now also contend with potential data breaches and the associated reputational damage.
Understanding Malware and Its Variants
Malware, an abbreviation for “malicious software,” is a broad term that encompasses a variety of software designed with malicious intent. From disrupting computer operations to collecting sensitive information or gaining unauthorized access, malware has been a persistent threat in the digital world. This section will delve into the different types of malware, their characteristics, and the evolution of these threats over time.
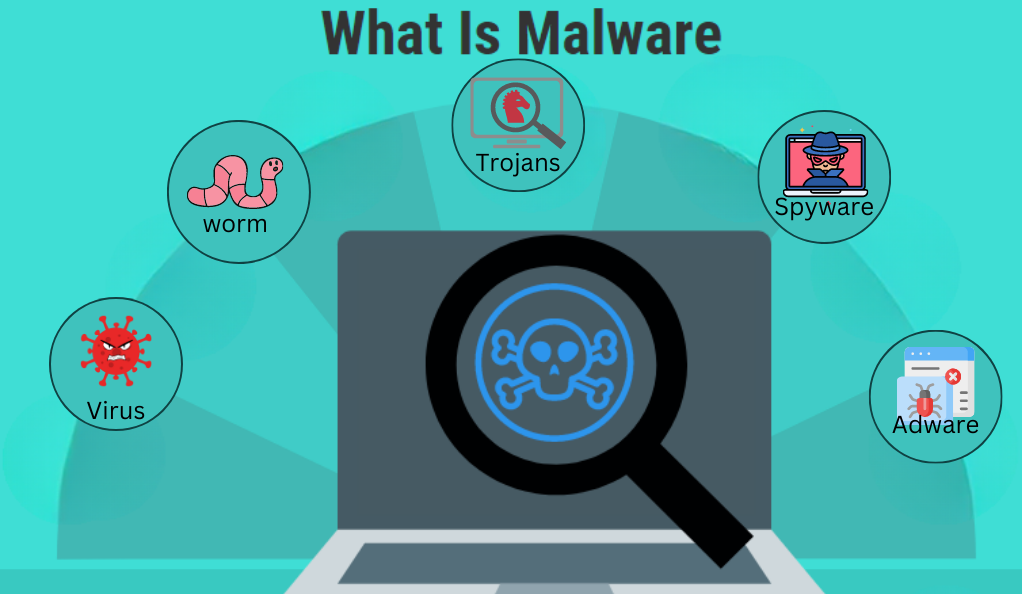
What is Malware?
At its core, malware is software written specifically to harm or exploit any device, network, service, or computer program. It can be introduced to a system in various ways, including email attachments, software downloads, or even malicious advertisements.
The Many Faces of Malware
Malware comes in many forms, each with its unique characteristics and methods of operation. Some of the most common types include:
- Viruses: Attach themselves to clean files and spread throughout a computer system.
- Worms: Standalone software that replicates and spreads to other computers.
- Trojans: Disguise themselves as legitimate software but act maliciously once inside the host system.
- Spyware: Secretly monitors and collects user information.
- Adware: Unwanted software that displays advertisements.
Evolution Over the Decades
From the early days of simple computer viruses to today’s sophisticated state-sponsored malware campaigns, the evolution of malware mirrors the broader developments in the world of technology.
Timeline of Notable Malware:
| Year | Malware | Significance |
|---|---|---|
| 1986 | Brain | Considered the first computer virus for MS-DOS. |
| 2000 | ILOVEYOU | A worm that affected millions of Windows PCs globally. |
| 2003 | Slammer | A worm that caused widespread internet outages. |
| 2010 | Stuxnet | Targeted Iranian nuclear facilities. |
Advanced Persistent Threats (APTs)
APTs are complex, long-term targeted attacks. Often state-sponsored, these threats aim to steal data rather than cause immediate damage. They’re characterized by their persistence, stealth, and sophistication.
Malware Distribution Methods
How does malware find its way onto devices? Common distribution methods include:
- Phishing Emails: Disguised as legitimate communications to trick users into downloading attachments.
- Drive-by Downloads: Malware is automatically downloaded when a user visits a compromised website.
- Malvertising: Malicious advertisements that redirect users to malware-laden sites.
- USB Drives: Infected hardware devices introduced to a system.
The Impact of Malware
Beyond the immediate disruptions, malware can have long-term consequences, including financial losses, data breaches, and reputational damage. For businesses, a single malware attack can result in significant downtime and loss of customer trust.
Phishing: The Human Element of Cyber Attacks
Phishing, a deceptive tactic that preys on human psychology, stands as one of the most prevalent forms of cyberattacks. By manipulating individuals into revealing sensitive information, cybercriminals can gain unauthorized access, commit fraud, or even launch more sophisticated attacks. This section delves into the world of phishing, emphasizing the human element that makes these attacks so effective and dangerous.
What is Phishing?
Phishing is a cyberattack method where attackers impersonate trusted entities to deceive individuals into providing sensitive information, such as passwords, credit card numbers, or personal identification details.
The Psychology Behind Phishing
At the heart of every phishing attack is the exploitation of human psychology. Attackers rely on:
- Urgency: Creating a sense of immediate action to prevent users from thinking critically.
- Trust: Impersonating familiar entities or individuals.
- Curiosity: Leveraging intriguing or enticing content to prompt action.
- Fear: Threatening potential consequences if action isn’t taken.
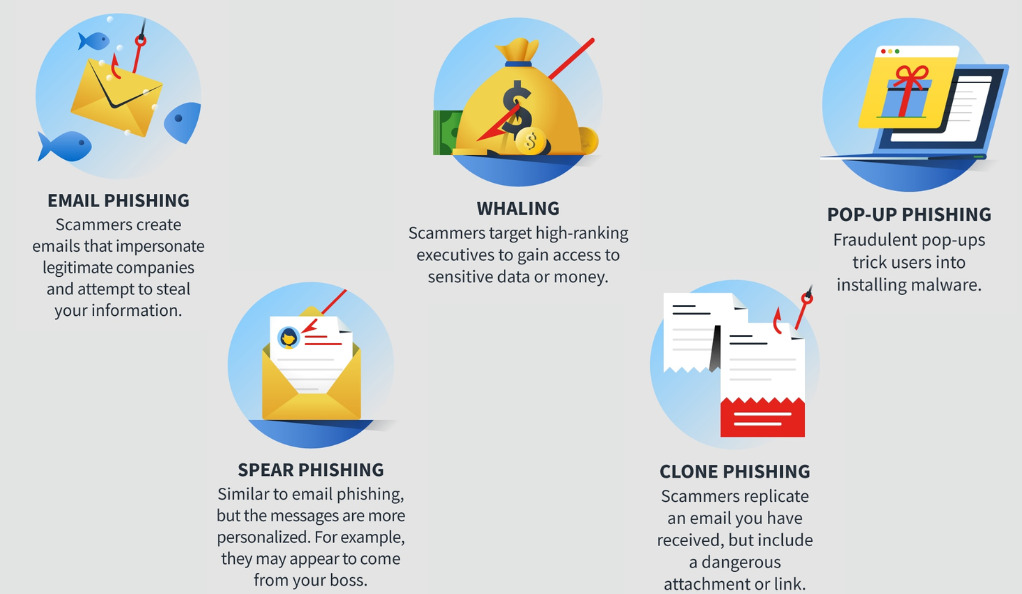
Common Phishing Techniques
Phishing attacks have evolved over time, but some common techniques include:
- Email Phishing: Deceptive emails mimicking legitimate organizations.
- Spear Phishing: Targeted attacks on specific individuals or companies.
- Vishing: Voice-based phishing, often over the phone.
- Smishing: Phishing attacks conducted via SMS.
Real-World Phishing Examples
To understand the depth and impact of phishing, consider these real-world incidents:
| Year | Phishing Incident | Impact |
|---|---|---|
| 2011 | RSA Security Breach | Attackers stole sensitive data related to SecurID. |
| 2016 | DNC Email Leak | Spear-phishing led to the leak of DNC emails. |
| 2018 | Netflix Account Scam | Users deceived into updating payment details. |
The Consequences of Falling for Phishing
The repercussions of a successful phishing attack can be severe:
- Financial Loss: Direct theft or fraudulent transactions.
- Data Breach: Unauthorized access to sensitive data.
- Reputational Damage: Loss of trust among clients or customers.
- Operational Disruption: Downtime or loss of access to critical systems.
The Role of Education in Prevention
One of the most effective defenses against phishing is education:
- Training Programs: Regularly updating staff on the latest phishing tactics.
- Simulated Phishing Attacks: Testing an organization’s vulnerability.
- Awareness Campaigns: Keeping the threat of phishing in the forefront of employees’ minds.
Best Practices to Combat Phishing
Protection against phishing requires both technological and human interventions:
- Email Filtering: Using software to detect and block phishing emails.
- Two-Factor Authentication: An additional layer of security.
- Regular Backups: Ensuring data can be restored in case of a breach.
- Critical Thinking: Encouraging users to think before they click.
Proactive Defense Strategies
In the ever-evolving landscape of cyber threats, reactive measures are often insufficient. Waiting for an attack to occur before taking action can result in significant damages, both financially and reputationally. Instead, a proactive approach to cybersecurity is essential. This section delves into the various proactive defense strategies that individuals and organizations can employ to stay one step ahead of potential cyber threats.
The Need for Proactivity in Cybersecurity
In today’s interconnected world, the digital realm offers unparalleled convenience and opportunities. However, with these advantages come significant challenges. The cyber landscape is fraught with threats that are not only increasing in number but also in sophistication.
- Rapid Evolution of Threats: The digital age is characterized by the swift evolution of technology. Similarly, cyber threats are not static. Hackers and cybercriminals are continually refining their methods, finding new vulnerabilities, and devising more effective ways to breach systems. This constant evolution means that yesterday’s security solutions might be inadequate today, necessitating continuous vigilance and adaptation.
- Increasingly Sophisticated Attacks: Gone are the days when simple antivirus software could ward off most threats. Modern cyberattacks, equipped with advanced techniques and tools, can often bypass traditional defenses. These attacks can be multi-pronged, targeting both hardware and software vulnerabilities, making them harder to detect and counter.
- Wider Attack Surface: The Internet of Things (IoT) has led to a surge in connected devices, from smart thermostats to connected cars. Each device represents a potential entry point for cybercriminals. As our reliance on these devices grows, so does the attack surface, making it imperative to secure every touchpoint.
Risk Assessment and Management
The foundation of any robust cybersecurity strategy lies in understanding and managing potential risks.
- Regular Audits: Periodic reviews of IT infrastructure can identify outdated systems, software vulnerabilities, and potential weak points. These audits, conducted by internal teams or third-party experts, provide a roadmap for necessary security upgrades.
- Threat Modeling: This proactive approach involves anticipating potential attack vectors based on current trends and historical data. By understanding how an attacker might target the system, organizations can prepare and defend more effectively.
- Prioritization: Not all vulnerabilities are created equal. Some pose a more significant threat than others. By prioritizing the most critical vulnerabilities, organizations can allocate resources more effectively, addressing the most pressing threats first.
Implementing Layered Security
A holistic approach to security involves multiple layers of defense, ensuring that if one layer is compromised, others remain intact.
- Perimeter Defense: This is the first line of defense and includes tools like firewalls and intrusion detection systems. They act as gatekeepers, monitoring incoming and outgoing traffic and blocking suspicious activities.
- Internal Defense: Even if the perimeter is breached, internal defenses like antivirus software, endpoint protection, and network segmentation can prevent or limit damage. They ensure that malware doesn’t spread and that compromised sections of the network are isolated.
- Data Defense: Data is often the primary target of cyberattacks. Protecting it involves encryption (making data unreadable without a decryption key) and regular backups (ensuring data can be restored in case of loss or corruption).
Continuous Monitoring and Threat Detection
In the realm of cybersecurity, what you don’t know can hurt you. Continuous monitoring ensures that threats are detected and addressed in real-time.
- Security Information and Event Management (SIEM): SIEM solutions aggregate and analyze log data from various sources, looking for patterns or activities that deviate from the norm. This allows for swift detection of suspicious activities.
- Behavioral Analytics: By understanding typical user behavior, systems can detect anomalies. For instance, if an employee who typically accesses the system during regular business hours suddenly logs in at midnight, it might indicate a breach.
Employee Training and Awareness
People are often the weakest link in the security chain. Ensuring they are educated and vigilant is crucial.
- Regular Training: Cyber threats evolve, and so should employee training. Regular sessions can keep staff updated on the latest threats and safe practices.
- Phishing Simulations: These mock exercises test employees’ ability to recognize and resist phishing attempts, providing valuable feedback and learning opportunities.
- Clear Reporting Protocols: If employees suspect a cyber incident, they should know exactly how to report it. Clear protocols ensure swift action and can mitigate potential damage.
Incident Response Planning
Despite best efforts, breaches can occur. Being prepared with a clear response plan is crucial.
- Incident Response Team: This dedicated team, trained specifically to handle cyber incidents, can take immediate action when a breach is detected.
- Drills and Simulations: Just as fire drills prepare employees for potential fires, cyber drills prepare them for potential breaches. Regular simulations can test and refine the organization’s response to hypothetical cyberattacks.
- Communication Protocols: In the event of a breach, stakeholders (including customers, partners, and regulators) may need to be informed. Having a clear communication plan ensures that the right information reaches the right people at the right time.
Staying Updated and Informed
The world of cybersecurity is dynamic and ever-changing. Staying informed is essential.
- Industry Forums and Groups: Organizations like ISACA or CompTIA offer resources, insights, and platforms for professionals to share knowledge and best practices.
- Regular Software Updates: Outdated software can have vulnerabilities. Regular updates ensure that all software, especially security solutions, has the latest defenses.
- Engaging with Experts: The field of cybersecurity is vast. Regular consultations with experts can provide guidance, insights, and recommendations tailored to an organization’s specific needs.
Conclusion
In the digital age, the intersection of vast opportunities and cyber threats underscores the paramount importance of cybersecurity. As we become more intertwined with digital platforms, threats like ransomware and phishing schemes not only risk financial losses but also compromise sensitive data and trust. Proactivity, encompassing anticipation, preparation, and prevention, stands as the cornerstone of effective cybersecurity. This involves understanding evolving threats, implementing layered defenses, educating staff, and having robust response plans in place.
The convergence of traditional organized crime with digital tactics highlights the intricate nature of today’s threat landscape. However, technological advancements, while introducing vulnerabilities, also offer potent defense tools. Collaborative efforts across industries and borders are fostering shared defenses against these threats. As we navigate this digital realm, a combination of cutting-edge technology and a culture of awareness will be our strongest shield against cyber adversaries.








