In the vast expanse of the digital universe, the term “malware” has emerged as a significant buzzword, often evoking images of shadowy hackers and compromised systems. But what exactly is malware, and why has it become such a pivotal concern in today’s interconnected world?
Defining Malware
At its core, malware, a portmanteau of “malicious software,” refers to any software intentionally designed to harm, disrupt, or exploit any device, network, service, or computer program. Unlike software flaws that inadvertently cause issues, malware is purposefully crafted by individuals or groups to achieve specific malicious objectives.
| Type | Description |
|---|---|
| Virus | A malicious code that attaches itself to legitimate files and spreads to other files and programs. |
| Worm | A standalone software that replicates itself to spread to other devices, often exploiting network vulnerabilities. |
| Trojan Horse | Disguises itself as legitimate software but delivers a malicious payload once inside the host system. |
| Ransomware | Encrypts the victim’s data, demanding a ransom for its decryption. |
| Rootkit | Conceals its presence, giving remote control of a device to an attacker. |
| Backdoor | Provides unauthorized access to a system, bypassing standard authentication. |
The Evolution of Threats
Historically, the term “computer virus” was synonymous with malicious software. Early viruses were relatively simple, often spread via floppy disks and primarily aimed at causing mischief. Fast forward to the present day, and the landscape has dramatically changed. The rise of the internet, coupled with the proliferation of smart devices, has given birth to a myriad of malware types, each more sophisticated and damaging than its predecessor.
Modern malware is no longer just about causing random disruptions. It’s about data theft, espionage, financial gains, and even political motives. With the stakes higher than ever, understanding the nuances of these threats is paramount.
The Significance in Today’s Digital Age
As we further entrench ourselves in the digital age, our reliance on technology grows. From online banking to smart homes, our data and daily operations are intertwined with digital systems. This interconnectivity, while offering unparalleled convenience, also presents lucrative opportunities for cybercriminals. A single malware infection can lead to data breaches, financial losses, and a tarnished reputation.
The Proliferation of Malware
The digital age, while ushering in an era of unprecedented connectivity and innovation, has also seen an alarming surge in the number and complexity of malware threats. This growth isn’t merely incidental; it’s a reflection of the evolving motivations and capabilities of cyber adversaries.
The Exponential Growth of Malware Variants
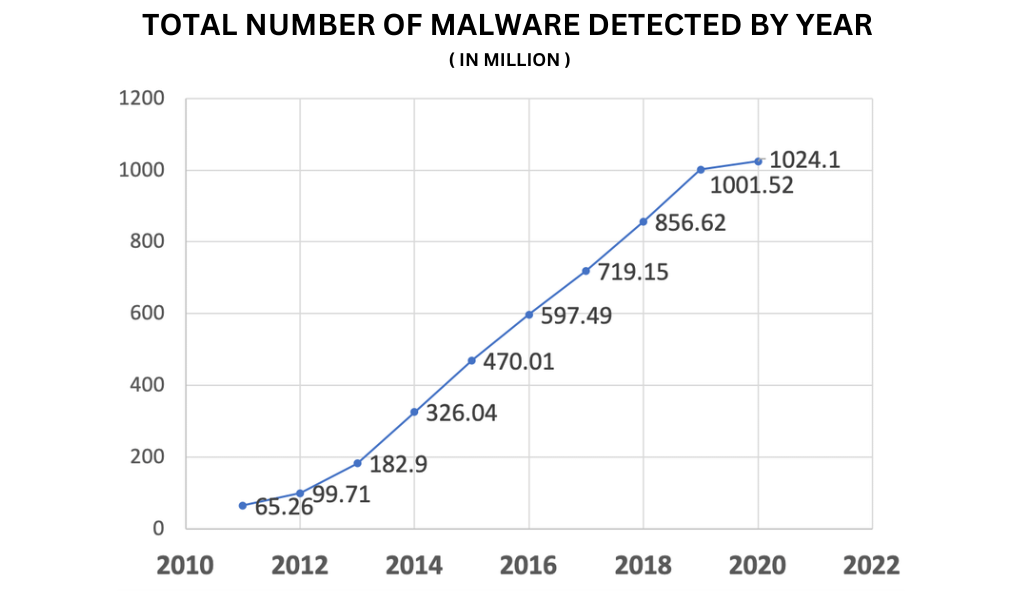
In the early days of the internet, malware was relatively sparse, with a few hundred known variants. Today, millions of new malware samples are discovered annually. This exponential growth can be attributed to several factors:
- Ease of Creation: With the advent of malware-as-a-service platforms, even individuals with limited technical know-how can create and deploy malware.
- Financial Motives: Cybercrime has become a lucrative business. Ransomware attacks, in particular, can yield significant financial gains for attackers.
- Political and Espionage Objectives: State-sponsored attacks and cyber espionage campaigns often deploy sophisticated malware to achieve their objectives.
The Economic Impact of Cybercrimes and Malware Attacks
The financial repercussions of malware attacks extend beyond the immediate victims. Entire economies can feel the ripple effects. According to a recent study, the global cost of cybercrime is projected to reach $10.5 trillion annually by 2025, up from $3 trillion in 2015. This staggering figure encompasses direct damages, post-attack disruptions, and preventive measures.
Businesses, both large and small, are frequent targets. A successful attack can lead to:
- Operational Downtime: Disruptions in services or production lines can result in significant revenue losses.
- Reputation Damage: Trust is hard to earn but easy to lose. Customers may migrate to competitors after a security breach.
- Regulatory Fines: Non-compliance with data protection regulations can lead to hefty penalties.
The Changing Face of Malware Attacks
While traditional malware attacks were often broad and indiscriminate, modern campaigns are increasingly targeted. Attackers often conduct thorough reconnaissance to identify vulnerabilities and tailor their malware to exploit them. This shift underscores the importance of robust cybersecurity measures and continuous vigilance.
Diverse Types of Malware
As we delve deeper into the realm of cyber threats, it becomes evident that malware is not a monolithic entity. Instead, it’s a vast umbrella term encompassing a range of malicious software, each with its unique characteristics, objectives, and modes of operation. Understanding these distinctions is crucial for effective defense and mitigation.
Differentiating Between Viruses, Worms, and Trojan Horses
- Viruses: Much like their biological counterparts, computer viruses attach themselves to clean files and infect other clean files. They can spread uncontrollably, damaging a system’s core functionality and deleting or corrupting files. They usually appear as an executable file and require human intervention to propagate.
- Worms: Worms are distinct from viruses in their ability to replicate and spread autonomously. They exploit vulnerabilities in software and can quickly propagate across networks. A notable example is the WannaCry ransomware worm that affected systems worldwide in 2017.
- Trojan Horses: Named after the ancient Greek story of the wooden horse that was used to infiltrate Troy, Trojan horses disguise themselves as legitimate software. However, once installed, they can deploy their malicious payload, which can range from data theft to creating backdoors in the infected system.
The Rise of Ransomware and Its Devastating Effects
Ransomware has emerged as one of the most formidable malware types in recent years. By encrypting the victim’s data and demanding a ransom for its release, cybercriminals can exert direct financial pressure on their targets. The consequences of a ransomware attack can be crippling:
- Operational Paralysis: Organizations can be rendered inoperative, leading to significant financial losses.
- Reputational Damage: Beyond the immediate financial implications, the public relations fallout can be long-lasting.
- Data Loss: If backups are not available or are also compromised, critical data can be lost permanently.
Rootkits: Concealing Malicious Activities
Rootkits are a stealthy form of malware that aim to hide their existence and activities on an infected system. By gaining administrator-level access, they can modify system settings, disable antivirus software, and remain undetected for extended periods. Their primary objective is not damage but surveillance and data theft.
Backdoors: Unauthorized Access and Its Implications
Backdoors provide attackers with unauthorized access to a system, bypassing standard authentication methods. They can be introduced by other malware types or can exploit vulnerabilities in software. Once established, backdoors can be used for a range of malicious activities, from data theft to launching further attacks on other systems.
The Deception of Trojan Horses
Trojan horses, often simply referred to as “Trojans,” are among the most insidious forms of malware. Their primary characteristic is deception; they masquerade as benign or useful software, only to deliver a malicious payload once inside the host system. This section will unravel the intricacies of these deceptive threats.
Understanding the Masquerade
The essence of a Trojan horse lies in its ability to deceive. Users are often tricked into downloading and installing Trojans, believing them to be legitimate software. This could be in the form of a seemingly useful application, an email attachment, or even a software update. Once executed, the Trojan goes to work, often without the user’s knowledge.
Types of Trojan Horses
- Downloader Trojans: These Trojans focus on downloading and installing new versions of malicious programs, including other Trojans, onto the infected system.
- Infostealer Trojans: As the name suggests, these are designed to steal information from the infected device. This could range from login credentials to personal and financial data.
- Remote Access Trojans (RATs): These provide cybercriminals with complete control over the infected system, allowing them to steal data, monitor user behavior, and even activate the system’s webcam.
- Banking Trojans: Specifically designed to steal banking and financial information, these Trojans can intercept and redirect transactions, leading to financial losses for the user.
The Dangers of Social Engineering and Drive-by Downloads
Trojans often rely on social engineering tactics to infiltrate systems. Cybercriminals exploit human psychology, manipulating users into performing specific actions. This could be in the form of a convincing phishing email urging the user to download an attachment or a fake advertisement on a website.
Drive-by downloads are another common method. In this scenario, simply visiting a compromised website can result in the automatic download of a Trojan, without the user’s knowledge or consent.
Mitigating the Threat of Trojan Horses
Protection against Trojans requires a multi-pronged approach:
- Regular Software Updates: Keeping all software, especially the operating system and browsers, updated ensures that known vulnerabilities are patched.
- Antivirus and Anti-malware Tools: These tools can detect and remove Trojans based on their signatures. Regular scans and real-time protection are essential.
- User Awareness: Educating users about the dangers of downloading software from untrusted sources and the importance of scrutinizing email attachments can significantly reduce the risk of Trojan infections.
Ransomware: The Digital Hostage Situation
In the ever-evolving landscape of cyber threats, ransomware stands out as one of the most audacious and financially damaging forms of malware. Its modus operandi is simple yet devastating: encrypt the victim’s data and demand a ransom for its release. This section delves into the intricacies of ransomware, its impact, and the measures to counteract it.
Encryption-based Ransomware and Its Modus Operandi
At the heart of ransomware lies encryption. Once a system is infected, the ransomware encrypts critical files, rendering them inaccessible. Victims are then presented with a ransom note, typically demanding payment in cryptocurrencies like Bitcoin, to receive the decryption key.
The strength of the encryption used means that, in most cases, attempting to decrypt the files without the key is virtually impossible. This places victims in a precarious position: pay the ransom and hope the attackers provide the decryption key, or refuse and potentially lose their data forever.
The Economic Implications and the Rise of Crypto-ransom Attacks
The financial impact of ransomware attacks is staggering. Beyond the immediate ransom demands, which can range from a few hundred to millions of dollars, the collateral damage is extensive:
- Operational Downtime: Businesses can face prolonged periods of inactivity, leading to revenue losses.
- Recovery Costs: Even if the ransom is paid, significant resources may be required to restore systems and data.
- Reputational Damage: The public relations fallout from a ransomware attack can lead to a loss of customer trust and future business.
The anonymity provided by cryptocurrencies has further emboldened attackers, making tracing and prosecuting them challenging.
High-Profile Ransomware Attacks
Several ransomware attacks have made headlines in recent years, targeting critical infrastructure, healthcare institutions, and major corporations. Some notable examples include:
- WannaCry: In 2017, this ransomware worm exploited a Windows vulnerability, affecting over 200,000 computers across 150 countries and causing damages estimated in the billions.
- NotPetya: Masquerading as ransomware, this 2017 attack primarily targeted Ukraine, causing widespread disruption and financial losses.
- Colonial Pipeline: In 2021, a ransomware attack on the Colonial Pipeline, a major U.S. fuel pipeline, led to widespread fuel shortages and a ransom payment of $4.4 million.
Defending Against Ransomware
To guard against ransomware, it’s vital to regularly back up essential data and store it separately. Effective email filtering can block threats from malicious attachments. Keeping software updated patches known vulnerabilities, and educating users about suspicious downloads and emails further reduces the risk of infections.
Grayware: The Ambiguous Threat
In the vast spectrum of malicious software, there exists a category that doesn’t fit neatly into the traditional definitions of malware. This category, known as “grayware,” encompasses software that, while not overtly malicious, can be annoying, intrusive, and potentially harmful. Let’s delve into the nebulous world of grayware, understanding its nuances and the challenges it presents.
Defining Grayware
Grayware is a catch-all term for software that resides in the gray area between benign software and traditional malware. While it doesn’t cause direct harm like viruses or worms, grayware can compromise user experience, privacy, and system performance. Common types of grayware include:
- Adware: Software that displays unwanted advertisements, often in the form of pop-ups or banners. While adware itself isn’t harmful, it can be intrusive and degrade user experience.
- Spyware: This type of grayware secretly monitors user activities, collecting data without the user’s knowledge or consent. The gathered information can range from browsing habits to personal details.
- Potentially Unwanted Programs (PUPs): These are software applications that a user may unknowingly download and install, often bundled with other software. While not directly malicious, PUPs can affect system performance and may come with unwanted features.
The Thin Line Between Unwanted Applications and Malware
What makes grayware particularly challenging is its ambiguous nature. For instance, a software tool that monitors user behavior for targeted advertising might be considered useful by some and invasive by others. This subjectivity makes it difficult to classify and address grayware threats universally.
Implications of Grayware
While grayware might initially appear benign, especially when contrasted with more pronounced threats like ransomware or Trojans, its subtle implications are manifold. Spyware and specific adware variants can amass significant user data, posing genuine privacy risks. Additionally, certain grayware applications can be notably resource-intensive, hampering system performance and diminishing the overall user experience. Furthermore, grayware can inadvertently act as a gateway to more malicious software; for example, adware could showcase advertisements that redirect users to sites riddled with malware.
Combatting Grayware
Addressing grayware demands a blend of technical solutions and user awareness. Modern security tools can detect and remove grayware, while regular software audits help eliminate unwanted applications. Users should exercise caution when downloading from unverified sources and be educated about grayware risks to make informed software choices.
Defending Against Malware
In our journey through the intricate world of malware, from the overt threats of ransomware to the subtle nuances of grayware, one thing becomes abundantly clear: proactive defense is paramount. As cyber threats continue to evolve in complexity and scale, so must our strategies to counteract them. This section delves into the essential measures to defend against malware and safeguard our digital realms.
The Importance of Proactive Defense Strategies
Reactive approaches, where actions are taken post-infection, often result in significant damage, both in terms of data loss and financial repercussions. Proactive defense, on the other hand, emphasizes prevention, aiming to stop threats before they infiltrate systems.
Utilizing Antivirus Software and Firewalls
- Antivirus Software: This is the first line of defense against most malware threats. Modern antivirus solutions not only rely on signature-based detection but also employ heuristic analysis to detect previously unknown threats. Regular updates and scans are crucial for optimal protection.
- Firewalls: These act as barriers between trusted internal networks and potentially malicious external networks, such as the internet. Firewalls monitor and control incoming and outgoing network traffic based on predetermined security policies, blocking unauthorized access and malicious content.
Regular Patches and Software Updates
Cybercriminals often exploit known vulnerabilities in software to introduce malware. Regularly updating operating systems and applications ensures that these vulnerabilities are patched, reducing potential entry points for malware.
Safe Browsing and Download Habits

In the realm of digital security, two key practices stand out. First, it’s essential to be wary of suspicious links, as phishing campaigns frequently employ deceptive links to distribute malware. This is especially true for links found in unsolicited emails, where verifying authenticity is paramount. Second, when downloading software and applications, it’s crucial to source them from official or trusted third-party platforms. Both these measures significantly reduce the risk of malware infiltration and ensure a safer online experience.
The Role of User Awareness and Education in Malware Prevention
Arguably, the most potent defense against malware is an informed and vigilant user base. Regular training sessions and awareness campaigns can equip users with the knowledge to:
- Recognize phishing attempts and deceptive links.
- Understand the importance of strong, unique passwords.
- Be cautious about sharing personal or financial information online.
Backup: The Ultimate Safety Net
Regular backups ensure that, even in the event of a successful malware attack, data can be restored without significant loss. It’s essential to store backups in a separate location, isolated from the main network, and to periodically test them for integrity.
Conclusion: Navigating the Cyber Threat Landscape
In the ever-evolving digital realm, the continuous adaptation of malware stands as a testament to the challenges and threats we face. From rudimentary viruses to sophisticated state-sponsored attacks, staying informed and vigilant is our strongest defense. As technology advances, introducing both new opportunities and vulnerabilities, it’s evident that cybersecurity is a collective responsibility. Every individual, from casual users to IT professionals, plays a crucial role in shaping a secure digital future. Embracing knowledge, fostering international cooperation, and emphasizing user education will be pivotal as we navigate the complexities of our interconnected world.








