In today’s interconnected world, where communication is instantaneous and borders are virtually non-existent, the importance of securing voice communications cannot be overstated. Voice over Internet Protocol (VoIP) has revolutionized the way we communicate, offering unparalleled convenience and cost savings. However, with these advancements come new challenges, particularly in the realm of security.
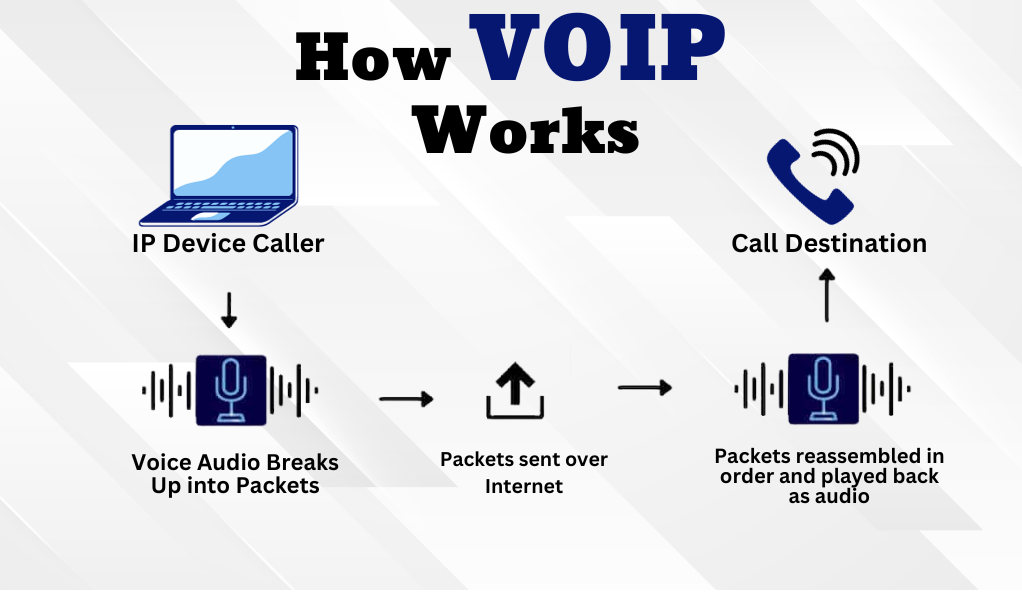
Why VoIP Security Matters
VoIP, at its core, transforms voice into data packets that traverse the vast expanse of the internet. Just as you wouldn’t send a confidential letter without sealing it, voice data, too, requires protection. Without adequate security measures, these voice packets can be intercepted, manipulated, or even rerouted by malicious actors.
The Digital Voice Ecosystem
To understand the significance of VoIP security, it’s essential to grasp the digital voice ecosystem’s intricacies. Consider the following table that breaks down the VoIP communication process:
| Component | Description |
|---|---|
| User Device | This could be a computer, IP phone, or mobile device from which the call originates. |
| VoIP Software | Applications or platforms like Skype, Zoom, or proprietary business solutions. |
| Call Processor | The server that manages call setup, routing, and termination. |
| Codec | Software that converts voice into data packets and vice versa. |
| Internet | The medium through which the voice data packets travel. |
| Receiver Device | The endpoint device, like an IP phone or computer, where the call is received and voice is rendered. |
Each component in this ecosystem presents a potential vulnerability point. If any of these components are compromised, it could lead to eavesdropping, fraud, or even service denial.
Real-world Consequences
The implications of neglecting VoIP security are vast. From financial losses due to toll fraud to reputational damage from leaked confidential conversations, the stakes are high. For instance, a business might find itself billed for thousands of dollars in unauthorized calls if their VoIP system is breached. On a more personal level, imagine the ramifications of personal conversations or business strategies falling into the wrong hands.
Understanding the Threat Landscape
The digital realm, while offering a plethora of advantages, is not without its dark alleys. As VoIP technology becomes more prevalent, it has inevitably attracted the attention of cybercriminals. To effectively safeguard our voice communications, we must first understand the threats we’re up against.

Eavesdropping on Calls: The Hidden Treasure for Cybercriminals
Eavesdropping, in the context of VoIP, refers to the unauthorized interception of voice packets during their transit. Cybercriminals employ sophisticated tools to “listen in” on these conversations, extracting valuable information. This could range from corporate secrets and financial data to personal details and confidential discussions.
Imagine a high-stakes business negotiation being intercepted, giving competitors an unfair advantage. Or consider the breach of attorney-client privilege, where sensitive legal strategies are exposed. The implications are vast and varied.
The Lucrative Nature of Hacking Voicemails
Voicemails, often overlooked, are a goldmine for hackers. These stored voice messages can contain a wealth of information, from business directives to personal messages. By gaining unauthorized access to voicemail systems, cybercriminals can retrieve these recordings, leading to data breaches.
A notable instance involved a global media scandal where celebrities’ voicemails were hacked, leading to widespread outrage and legal consequences. Such incidents underscore the importance of securing not just live voice data but also stored voice recordings.
Toll Fraud and Its Global Implications
Toll fraud is a multi-billion dollar concern in the VoIP industry. Here, attackers gain unauthorized access to a user’s VoIP system, making long-distance or international calls at the user’s expense. Businesses, especially those with inadequate security measures, can find themselves facing exorbitant bills for calls they never made.
For instance, a small business in the U.S. might suddenly find itself billed for hours of calls to a remote location in Eastern Europe, all made within a short span. Such incidents not only lead to financial losses but also disrupt regular business operations.
The Cost of Complacency
In the rapidly evolving world of digital communication, complacency can be a costly mistake. The belief that “it won’t happen to me” or “we’re too small to be targeted” is a dangerous misconception. The reality is that cybercriminals often target entities they perceive as having weaker security measures, regardless of their size or stature.
- Financial Implications
The immediate financial repercussions of a VoIP security breach can be staggering. Beyond the unauthorized calls leading to inflated bills, businesses may also face regulatory fines for failing to protect customer data. Additionally, the cost of remediation—identifying the breach, securing the system, and possibly compensating affected parties—can further strain a company’s finances. - Productivity Setbacks
A compromised VoIP system can lead to significant downtime. Businesses may find themselves unable to make or receive calls, disrupting regular operations. For sectors like customer support or sales, where voice communication is pivotal, the impact can be particularly severe. - Reputational Damage
Trust is a hard-earned commodity in the business world. A security breach, especially one that compromises customer data, can irreparably damage a company’s reputation. Clients and partners may question the company’s competence and commitment to security, leading to lost business opportunities and severed partnerships.
VoIP Vulnerabilities and Entry Points
As we journey deeper into the intricacies of VoIP security, it’s crucial to understand the potential weak spots or vulnerabilities inherent in the technology. By identifying these entry points, we can better strategize on how to fortify them against potential threats.
IP Phones: More Than Just Communication Devices
At the heart of any VoIP system are the IP phones—devices that convert our voice into digital packets for transmission over the internet. However, these are not mere communication tools. They are sophisticated devices with operating systems, software, and network connectivity, making them potential targets for cyberattacks.
Potential Vulnerabilities in IP Phones:
- Firmware Flaws: Outdated or poorly designed firmware can have vulnerabilities that hackers can exploit.
- Default Credentials: Many IP phones come with default usernames and passwords. If these aren’t changed, they provide an easy entry point for unauthorized users.
- Unencrypted Traffic: If voice data isn’t encrypted, it can be intercepted and decoded by eavesdroppers.
The Data Nature of VoIP Calls and Voicemails
Unlike traditional telephony, where voice travels as analog signals over copper lines, VoIP calls are essentially data packets traveling over the internet. This transformation brings along the vulnerabilities associated with data transmission:
- Packet Sniffing: Tools can capture these packets, allowing hackers to reconstruct and listen to conversations.
- Man-in-the-Middle Attacks: Attackers can intercept and potentially alter voice packets as they travel between the sender and receiver.
- Denial of Service (DoS): By overwhelming a VoIP system with traffic, attackers can render it unusable.
The Risks Beyond Voice Data
VoIP systems, especially when integrated with other business systems, can be a gateway to a wealth of information beyond just voice data:
- Access to Network Resources: Once inside a VoIP system, attackers might gain access to other network resources, from databases to email systems.
- Call Logs and History: These can reveal business relationships, patterns, and other sensitive information.
- Voicemail Hacking: As discussed earlier, voicemails can be a treasure trove of information if not adequately secured.
The Blurred Lines of Responsibility
One of the challenges with VoIP security is the shared responsibility. While service providers ensure the security of their infrastructure, clients are often responsible for securing their devices and internal networks. This division can lead to gaps in security if either party assumes the other has taken care of a particular aspect.
Strategies for Securing VoIP Systems
Recognizing the vulnerabilities in VoIP systems is only half the battle. The next step—and arguably the most crucial—is implementing robust strategies to counteract these vulnerabilities. Let’s delve into actionable measures that businesses and individuals can adopt to fortify their VoIP communications.
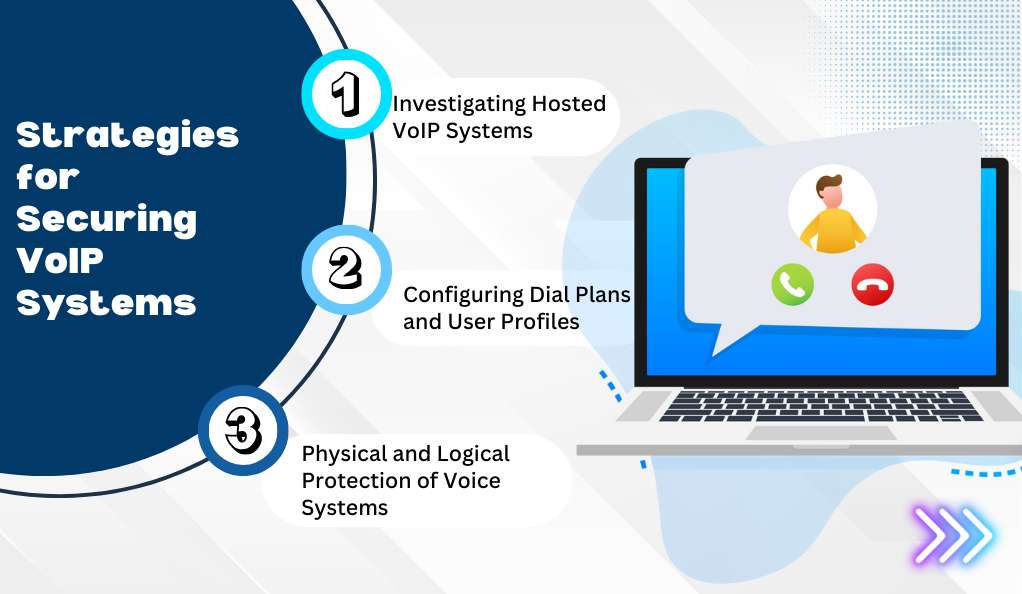
1. Investigating Hosted VoIP Systems
For those utilizing hosted VoIP solutions, it’s paramount to ensure that the chosen service provider prioritizes security. This involves scrutinizing the provider’s track record for reliability and any history of breaches or downtime. Additionally, it’s essential to confirm that the provider has implemented security provisions such as VLAN configuration, user authentication, and encryption. For businesses operating in regulated industries, verifying the provider’s adherence to compliance standards like HIPAA, SOX, or PCI becomes even more crucial.
2. Configuring Dial Plans and User Profiles
Beyond the service provider, optimizing the configuration of your own VoIP system can significantly bolster its security. This includes implementing access controls to limit voice network access using device certificates or user credentials, ensuring only authorized users can access the system. Furthermore, businesses can set call restrictions based on criteria like user profiles, devices, or time of day.
3. Physical and Logical Protection of Voice Systems
On the infrastructure front, setting up a firewall and an intrusion prevention system (IPS) to monitor and filter VoIP traffic can be invaluable. These systems can identify and block any malicious activities, providing an added layer of security. Additionally, ensuring the physical and logical security of VoIP servers is of utmost importance. This involves both physically securing servers in locked locations and logically protecting them with strong passwords and access controls.
Advanced Security Techniques
In the realm of VoIP security, as threats evolve, so must our defenses. Advanced security techniques not only address current vulnerabilities but also anticipate future challenges, ensuring that voice communications remain secure in an ever-changing digital landscape.
Deep Packet Inspection (DPI)
Deep Packet Inspection, commonly referred to as DPI, goes beyond the capabilities of traditional firewalls. Instead of merely examining the headers of data packets, DPI delves deeper, analyzing the content of packets in real-time. This allows for more precise threat identification, as DPI can identify and block malicious payloads or unauthorized voice traffic. Additionally, by analyzing voice traffic, DPI can prioritize VoIP packets, ensuring optimal call quality and preventing potential breaches.
Behavioral Analytics
Behavioral analytics offers a proactive approach to VoIP security. By monitoring and analyzing the behavior of users and network traffic, the system can detect anomalies that might indicate potential threats. Over time, the system learns the “normal” behavior of users and network traffic, establishing a baseline. Any deviation from this baseline, such as unusual call patterns or high call volumes at odd hours, triggers alerts for further investigation. This continuous monitoring ensures that threats can be identified and addressed in their early stages.
End-to-End Encryption (E2EE)
End-to-End Encryption, or E2EE, ensures that voice data remains encrypted from the moment it leaves the sender’s device until it reaches the recipient. This means that even if voice data is intercepted during transit, it remains encrypted and unintelligible to unauthorized parties. E2EE requires robust key management practices, ensuring that only the intended recipient can decrypt the voice data. By implementing E2EE, businesses can ensure the confidentiality and integrity of their voice communications.
Multi-factor Authentication (MFA)
Multi-factor Authentication adds an additional layer of security to VoIP systems. Beyond just usernames and passwords, MFA requires users to provide a second (or even third) form of verification before granting access. This could be a code sent to their mobile device, a biometric verification like a fingerprint, or a physical token. MFA ensures that even if a malicious actor obtains a user’s password, they would still need the second verification step to access the system, thereby providing an added layer of protection.
Geo-blocking and Whitelisting
Geo-blocking and whitelisting are techniques that restrict VoIP access based on specific criteria. With geo-blocking, businesses can prevent access from regions known for high cybercrime rates or unfamiliar IP addresses. This reduces the system’s exposure to potential threats from these regions. On the other hand, whitelisting ensures that only pre-approved IP addresses or devices can access the VoIP system. By combining both techniques, businesses can create a secure environment where only trusted entities have access, significantly reducing the risk of unauthorized intrusions.
User-Centric Security Policies
While technology plays a pivotal role in securing VoIP systems, the human element remains equally crucial. After all, the most advanced security systems can be rendered ineffective if users are careless or uninformed. Thus, fostering a culture of security awareness and implementing user-centric policies is paramount.
- Educating Users on VoIP Threats:
Awareness forms the cornerstone of any effective security strategy. To foster a culture of vigilance, it’s essential to educate users about the various threats targeting VoIP systems. Regular workshops can be conducted to delve into topics ranging from eavesdropping to toll fraud. By sharing real-world examples and stories of actual VoIP breaches, businesses can drive home the importance of security, ensuring that users understand the potential consequences of lax security practices.
- Implementing Best Practices:
Guiding users on the secure use of VoIP systems is pivotal in preventing potential breaches. Best practices can range from the technical, such as the importance of strong, unique passwords, to the behavioral, like avoiding the use of public Wi-Fi networks for VoIP calls. By ingraining these practices into the daily routines of users, businesses can significantly reduce the risk of inadvertent security lapses.
- Monitoring and Feedback:
Continuous monitoring of user behavior and VoIP traffic can provide invaluable insights into potential vulnerabilities. By analyzing how users interact with the VoIP system, businesses can identify risky behaviors or patterns that might indicate security lapses. Furthermore, establishing regular feedback sessions allows users to share their experiences, challenges, and suggestions related to VoIP usage. This two-way communication ensures that security policies remain relevant and effective.
- Emergency Protocols:
Despite the best preventive measures, security breaches can still occur. In such scenarios, having a clear and well-defined emergency protocol is crucial. Establishing a dedicated channel through which users can report any suspicious activities or perceived breaches ensures swift action. A rapid response team, equipped to handle such incidents, can then step in to mitigate potential damages, ensuring minimal disruption and data loss.
- Continuous Learning and Adaptation:
The digital threat landscape is ever-evolving, and security policies must adapt accordingly. Regular updates to user guidelines and best practices ensure that they address the latest threats and vulnerabilities. Encouraging users to share their insights and concerns creates a feedback loop, ensuring that policies remain relevant, effective, and user-centric. This continuous learning and adaptation ensure that businesses stay one step ahead of potential threats, safeguarding their VoIP communications in an ever-changing digital environment.
Conclusion: Navigating VoIP Security in the Digital Era
In the ever-evolving landscape of digital communication, VoIP security stands as a testament to the challenges and innovations that come with progress. Technology offers both advanced defense tools and new vulnerabilities, emphasizing the dual role it plays. Meanwhile, the human element remains pivotal, acting as both a shield and a potential weak link. As VoIP systems become more integrated and essential, fostering a culture of security awareness and leveraging expert solutions will be paramount.
Looking ahead, the future of voice communication is undeniably digital. With collective efforts from the tech community, businesses, and informed users, we can anticipate a future where digital conversations are not only efficient but also secure. This journey underscores the broader narrative of our digital age, where challenges are met with resilience and innovation, ensuring our digital voice remains authentic and protected.








