In the ever-evolving landscape of digital technology, ensuring the security of your online presence is paramount. Cyber threats loom large, and without adequate protection, your sensitive data and personal information can fall into the wrong hands. This is where firewalls step in as your first line of defense.
Understanding Firewalls

Firewalls are essential components of network security that act as barriers between your internal network and the vast, potentially hostile environment of the internet. They serve as digital gatekeepers, monitoring and controlling the flow of data in and out of your network. By doing so, firewalls play a crucial role in safeguarding your digital assets.
Significance in Cybersecurity
The importance of firewalls in the realm of cybersecurity cannot be overstated. They are like the sentinels guarding the gates of your castle, determining who is allowed entry and who is denied. Here’s why firewalls are so significant:
- Unauthorized Access Prevention: Firewalls prevent unauthorized access to your network and devices. They filter out malicious traffic, such as hackers attempting to infiltrate your system.
- Traffic Control: They allow you to define rules and policies for network traffic, deciding which data packets can pass through and which should be blocked. This control ensures that only legitimate traffic flows in and out.
- Protection Against Malware: Firewalls can identify and block traffic that contains malware or malicious code, reducing the risk of infections within your network.
- Privacy and Confidentiality: They protect your privacy by ensuring that sensitive data, such as personal information and financial details, remains within your network and doesn’t leak out.
- Network Monitoring: Firewalls provide real-time monitoring and logging capabilities, allowing you to detect suspicious activities and potential security breaches.
- Compliance: Many industry regulations and standards require the implementation of firewalls to protect sensitive data. Compliance with these regulations is essential for businesses.
Types of Firewalls
Firewalls come in various forms, each tailored to specific security needs and network configurations. Understanding the different types of firewalls is essential in choosing the right one for your environment. Here are the primary types:
Hardware Firewalls
Hardware firewalls are standalone devices that serve as a barrier between your internal network and the internet. They are typically placed at the network perimeter, making them the first line of defense. Hardware firewalls are known for their robust security features and are often used in business environments.
Software Firewalls
Software firewalls are programs or applications installed on individual devices, such as computers or smartphones. They are designed to protect specific devices from network threats. Software firewalls are ideal for personal use and can be customized to allow or block specific applications or services.
Next-Generation Firewalls (NGFW)
Next-Generation Firewalls (NGFW) are a more advanced evolution of traditional firewalls. They combine traditional firewall capabilities with additional security features such as intrusion prevention systems (IPS), application awareness, and content filtering. NGFWs offer a holistic approach to security and are suitable for organizations looking for comprehensive protection.
Unified Threat Management (UTM)
Unified Threat Management (UTM) devices are all-in-one security solutions that combine various security features into a single appliance. These features may include firewall, antivirus, intrusion detection, content filtering, and virtual private network (VPN) capabilities. UTMs are designed for simplicity and are often used by small to medium-sized businesses.
How Firewalls Work
Understanding how firewalls operate is crucial to grasp their role as your first line of defense in cybersecurity. Firewalls employ various methods to filter and control network traffic. Here are the fundamental principles governing their operation:
Packet Filtering
Packet filtering is one of the basic techniques used by firewalls. It involves inspecting individual data packets as they enter or exit a network. Packet filters examine packet headers and compare them to predefined rules, such as source and destination IP addresses, ports, and protocols.
Stateful Inspection
Stateful inspection, also known as dynamic packet filtering, takes packet filtering to the next level. This method keeps track of the state of active connections and makes filtering decisions based on the state of the connection. It’s more intelligent than packet filtering alone and is better at detecting and preventing unauthorized access.
Proxy Firewalls
Proxy firewalls act as intermediaries between internal users and external resources, such as websites or servers. When a user requests access to a resource, the proxy firewall forwards the request on behalf of the user. It then filters and inspects the response before passing it back to the user. This process adds an additional layer of security by isolating internal systems from external threats.
Deep Packet Inspection (DPI)
Deep Packet Inspection (DPI) is an advanced technique that involves a detailed analysis of packet contents, not just headers. DPI examines the actual data within packets to identify specific applications, services, or threats. This method provides granular control over network traffic and is particularly effective in identifying and blocking malicious content.
These are the key methods through which firewalls work to protect your network. Depending on your security needs and the sophistication of threats you face, you may opt for a firewall solution that employs one or more of these techniques.
Firewall Rules and Policies
Creating effective firewall rules and policies is essential to tailor your network security to your specific needs. Firewall rules define how traffic is allowed or denied based on various criteria. Here, we’ll explore the practical aspects of setting up these rules:
Creating Firewall Rules
Firewall rules are the heart of any firewall configuration. They specify the conditions under which network traffic is either allowed or blocked. The rules are typically defined based on:
- Source and Destination: Rules can be set to allow or block traffic between specific IP addresses, networks, or devices.
- Port and Protocol: You can specify the ports (e.g., 80 for HTTP, 443 for HTTPS) and protocols (e.g., TCP, UDP) that the rule applies to.
- Action: Decide whether to allow or deny traffic that matches the rule criteria.
- Logging: Enabling logging for a rule helps in monitoring and analyzing network traffic.
Rule Prioritization
Firewalls process rules in a specific order, often from top to bottom. It’s crucial to prioritize rules correctly to ensure that the most specific rules take precedence. Rule prioritization helps prevent conflicts and ensures that traffic is handled as intended.
- First Match Wins: In many firewall configurations, the first rule that matches the traffic criteria is applied. Subsequent rules may not be evaluated.
- Explicit Deny Rules: It’s a best practice to have explicit deny rules at the end of the rule set to catch any traffic that doesn’t match allowed rules.
- Logging and Monitoring: Enable logging for rules to keep track of traffic that matches each rule. This information is valuable for troubleshooting and security analysis.
Example Rule Scenarios
Let’s consider a few common rule scenarios to illustrate how firewall rules work:
| Scenario | Rule | Purpose |
|---|---|---|
| Allow Outbound Web Browsing | Allow traffic from all internal devices to destination ports 80 (HTTP) and 443 (HTTPS) on external IP addresses. | Permits users to access websites while blocking other unnecessary traffic. |
| Block Suspicious IP Addresses | Deny traffic from specific known malicious IP addresses. | Provides an extra layer of security by blocking connections from sources with a history of malicious activity. |
| Permit Remote Desktop Access | Allow traffic from a specific external IP address to connect to an internal device’s port 3389 (Remote Desktop Protocol). | Grants remote access to a specific device while maintaining a secure network. |
Creating well-defined firewall rules and policies tailored to your organization’s requirements is essential for effective network security. It’s a proactive measure to prevent unauthorized access, minimize security risks, and ensure the confidentiality of your data.
Firewall Deployment
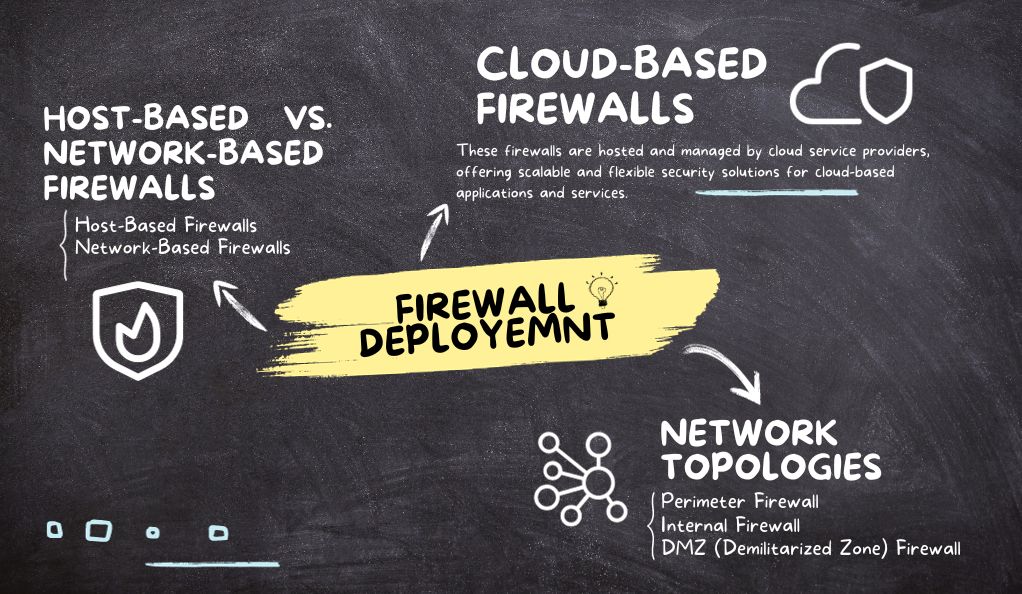
Firewall deployment plays a critical role in determining how effectively your network is protected. Different network topologies require different approaches to firewall implementation. Here, we will explore the various deployment options:
Network Topologies
Perimeter Firewall
A perimeter firewall, also known as an edge firewall, is positioned at the network boundary between your internal network and the external internet. It acts as the primary defense, filtering incoming traffic before it reaches your internal network. This type of deployment is common in traditional network setups.
Internal Firewall
An internal firewall is placed within your internal network to segment it into different security zones. It can be used to create isolated areas within your network, providing an additional layer of security for sensitive resources.
DMZ (Demilitarized Zone) Firewall
In a DMZ firewall setup, a separate network zone called the DMZ is established to host services that need to be accessible from the internet but should be isolated from the internal network. DMZ firewalls control traffic between the DMZ and both the internal network and the external internet.
Host-Based vs. Network-Based Firewalls
Host-Based Firewalls
Host-based firewalls are installed on individual devices, such as computers or servers. They provide security at the device level and are particularly useful for protecting laptops and mobile devices that may connect to various networks.
Network-Based Firewalls
Network-based firewalls are deployed as standalone devices within the network infrastructure. They provide centralized security control and are effective at filtering traffic at the network level.
Cloud-Based Firewalls
With the increasing adoption of cloud computing, cloud-based firewalls have gained prominence. These firewalls are hosted and managed by cloud service providers, offering scalable and flexible security solutions for cloud-based applications and services.
Firewall Best Practices
To ensure the effectiveness of your firewall as the first line of defense, it’s essential to follow best practices for its configuration, maintenance, and monitoring. Here are some key practices to consider:
Regular Updates and Patching
Firewall manufacturers release updates and patches to address security vulnerabilities and improve performance. It’s crucial to keep your firewall firmware, software, and rule sets up to date. Regularly check for updates and apply them promptly to ensure your firewall remains resilient against emerging threats.
Intrusion Detection and Prevention
Implementing intrusion detection and prevention systems (IDS/IPS) alongside your firewall enhances security. IDS monitors network traffic for suspicious behavior, while IPS actively blocks or mitigates threats. These systems provide an additional layer of defense against advanced threats and attacks.
Logging and Monitoring
Enable logging on your firewall to record network traffic and security events. Regularly review these logs to detect unusual or suspicious activity. Establish alerts and notifications to promptly respond to security incidents. Monitoring your firewall’s performance is essential for proactive threat detection.
Security Awareness Training
Educate your employees or users about security best practices. A well-informed workforce is less likely to inadvertently compromise network security. Train users to recognize phishing attempts, use strong passwords, and avoid risky online behavior that could bypass firewall protection.
Implement a Defense-in-Depth Strategy
A firewall is just one component of a comprehensive security strategy. Consider adopting a defense-in-depth approach, which combines multiple layers of security measures. This may include antivirus software, secure authentication, and network segmentation to enhance overall protection.
Regular Security Audits
Conduct regular security audits and penetration testing to identify vulnerabilities and weaknesses in your network. Address any identified issues promptly to improve the effectiveness of your firewall and overall security posture.
Documentation and Change Control
Maintain detailed documentation of your firewall configurations and rule sets. Implement change control procedures to ensure that firewall changes are thoroughly reviewed and tested before implementation. This helps prevent misconfigurations that can introduce security risks.
Business Continuity and Disaster Recovery
Plan for business continuity and disaster recovery scenarios. Ensure that your firewall configurations and security policies align with these plans. Having backup configurations and failover mechanisms in place can minimize downtime in the event of a security incident.
Common Firewall Challenges
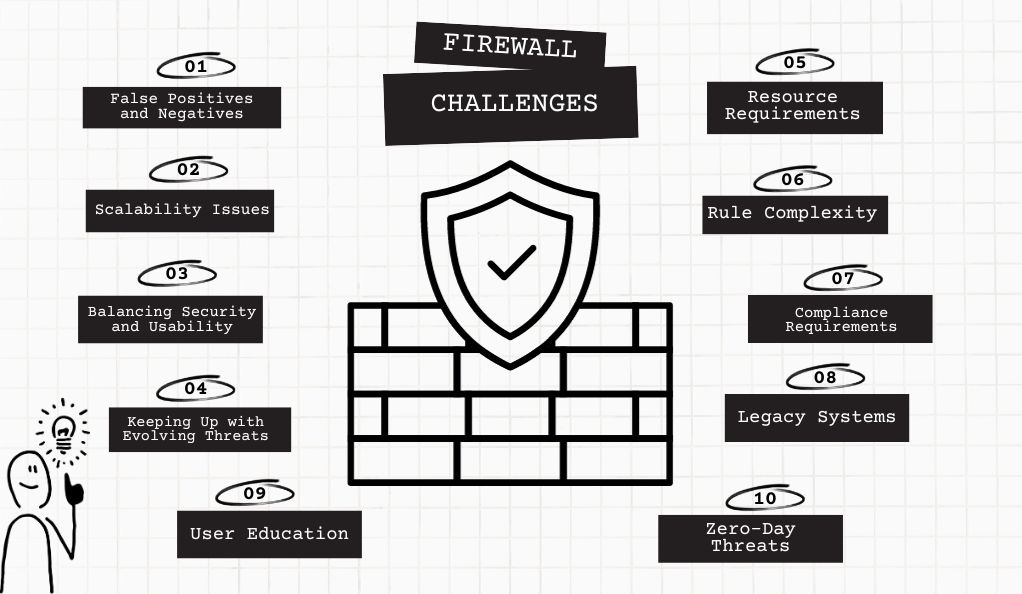
While firewalls are essential for network security, they come with their set of challenges and considerations. Understanding these challenges is crucial for effective firewall management. Here are some common issues you may encounter:
False Positives and Negatives
Firewalls aim to strike a balance between security and usability. False positives occur when legitimate traffic is incorrectly blocked, causing inconvenience to users. On the other hand, false negatives happen when malicious traffic goes undetected, posing a security risk. Achieving the right balance is an ongoing challenge.
Scalability Issues
As your network grows, the demands on your firewall increase. Ensuring that your firewall can handle increased traffic and the addition of new devices is essential. Scaling your firewall solution to match your network’s growth is a continuous consideration.
Balancing Security and Usability
Striking the right balance between robust security and user convenience can be challenging. Overly restrictive firewall rules can hinder legitimate business operations, while overly permissive rules can expose your network to risks. Continuous evaluation and adjustment of rules are necessary.
Keeping Up with Evolving Threats
Cyber threats are constantly evolving, and firewall rules and configurations must adapt accordingly. Staying informed about the latest threats and vulnerabilities is essential to ensure that your firewall remains effective.
Resource Requirements
Some advanced firewall features, such as deep packet inspection (DPI), can be resource-intensive. Ensuring that your firewall hardware or virtual appliance has sufficient processing power and memory to handle these features is critical for optimal performance.
Rule Complexity
Managing a large number of firewall rules can become complex and prone to errors. Documenting and organizing rules, as well as employing rule groups, can help mitigate this challenge.
Compliance Requirements
Many industries and organizations must adhere to specific regulatory compliance requirements (e.g., GDPR, HIPAA). Ensuring that your firewall configurations align with these regulations and standards is essential to avoid legal and financial repercussions.
Legacy Systems
Integrating firewalls with legacy systems or older network technologies can be challenging. It may require custom configurations and additional security measures to ensure compatibility and protection.
Zero-Day Threats
Zero-day threats are vulnerabilities and exploits that are discovered and exploited by hackers before security patches are available. Firewalls may not always detect these threats immediately, highlighting the importance of intrusion detection and prevention systems (IDS/IPS).
User Education
Even with the best firewall in place, users can still inadvertently compromise security through actions like clicking on phishing links. Ongoing user education and awareness training are crucial for minimizing these risks.
Conclusion
In the digital age, firewalls are the guardians of your online fortress, defending against cyber threats. They stand resolute, allowing safe passage while thwarting unauthorized access and malicious intruders. From exploring their types and workings to the intricacies of rule creation, deployment, and best practices, this journey has unveiled the vital role of firewalls in securing your digital domain.
As you navigate the digital landscape, remember that firewalls are just one layer of defense in a broader cybersecurity strategy. Embrace proactive measures, stay vigilant, and adapt to evolving threats. With the right firewall strategy, you fortify your digital stronghold and venture forth into the digital world with confidence, knowing your first line of security stands strong.








