Ransomware is a type of malicious software designed with the intent to extort money from its victims. It operates by encrypting the victim’s files, making them inaccessible. The attacker then demands a ransom from the victim, promising to provide the decryption key in return for payment. Unfortunately, paying the ransom doesn’t always guarantee the restoration of the encrypted files.
The rise of digital currencies, like Bitcoin, has further fueled the ransomware business model. These currencies allow attackers to maintain anonymity, making it challenging for law enforcement agencies to trace and apprehend them. As a result, ransomware attacks have seen a significant surge in recent years, targeting both individuals and large corporations.
The Evolution of Ransomware
In the early days of the internet, ransomware was relatively rudimentary. The primary form of ransomware, known as “screen lockers,” would lock users out of their computers, displaying a message that demanded payment. These were easier to combat, as they didn’t encrypt files but merely restricted access.
However, as technology advanced, so did ransomware. Modern ransomware variants are more sophisticated and dangerous. They encrypt valuable files, sometimes even entire network drives, making them inaccessible. The encryption methods used are often robust, making decryption without the appropriate key nearly impossible. This evolution has made ransomware a formidable threat in the cybersecurity landscape.
How Ransomware Infects Systems
Ransomware primarily spreads through deceptive tactics. Phishing emails are the most common method. These emails appear legitimate, often mimicking trusted entities, but contain malicious attachments or links. Once the user interacts with these elements, the ransomware is downloaded and executed on the system.
Another prevalent method is through exploit kits. These are software tools designed to take advantage of security vulnerabilities in systems or applications. When a user visits a compromised website, the exploit kit scans the user’s system for vulnerabilities. If found, the ransomware is silently installed without the user’s knowledge. This method emphasizes the importance of keeping software and systems updated to patch known vulnerabilities.

The Ransomware Business Model
Ransomware is not just a random act of cyber vandalism; it’s a business. Cybercriminals are motivated by the potential for significant financial gain. Once a system is infected, the victim is often willing to pay to regain access to their critical files, especially if they lack backups.
The business model is straightforward: infect, encrypt, demand payment, and decrypt (sometimes). However, it’s worth noting that paying the ransom doesn’t guarantee decryption. Some attackers take the money and vanish, while others might demand more money after the initial payment. This unpredictability makes dealing with ransomware attackers risky and reinforces the importance of preventive measures.
Impact of Ransomware on Businesses
Ransomware attacks can be devastating for businesses. Beyond the immediate financial implications of the ransom demand, there are other costs to consider. Downtime, loss of data, and the effort required for recovery can be significant. Moreover, there’s the reputational damage. Customers and partners may lose trust in a company that falls victim to such attacks, leading to lost business opportunities.
Furthermore, in some jurisdictions, businesses are legally obligated to report ransomware attacks, especially if customer data is compromised. This can lead to legal repercussions and potential fines. The cumulative effect of these factors can be crippling, especially for small and medium-sized businesses that may not have the resources to recover fully.
Defending Against Ransomware
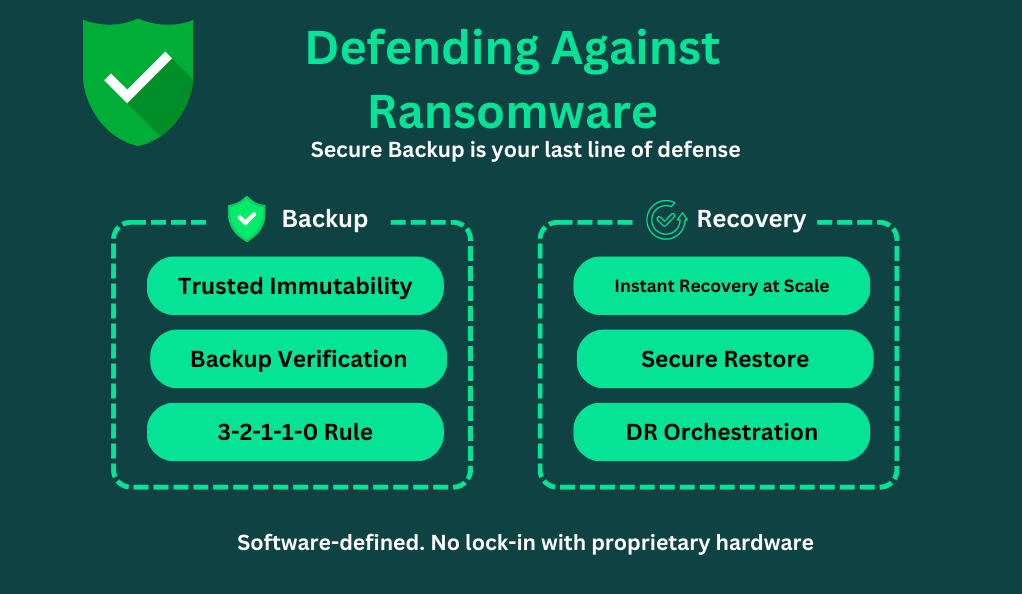
The best defense against ransomware is a multi-pronged approach. Regular backups are the first line of defense. By having up-to-date copies of critical data, businesses can restore their systems without paying the ransom. These backups should be stored offline to ensure they aren’t compromised during an attack.
In addition to backups, businesses should invest in cybersecurity training for their employees. Since phishing emails are a primary infection method, employees should be trained to recognize and report suspicious emails. Regular software updates, robust firewalls, and advanced antivirus solutions further bolster defenses, making it challenging for ransomware to penetrate the network.
Best Antivirus Software to Combat Ransomware
In the ever-evolving landscape of cyber threats, antivirus software plays a crucial role in defense. Modern antivirus solutions do more than just scan for known viruses. They employ advanced heuristics, behavior-based detection, and cloud-based threat intelligence to detect and neutralize threats, including ransomware.
When choosing an antivirus solution, it’s essential to opt for one that offers real-time protection, frequent updates, and ransomware-specific defenses. Some solutions even provide “rollback” features, allowing users to revert files to their pre-attack state. This can be invaluable in the event of a ransomware attack, providing an additional layer of protection alongside regular backups.
Importance of Firewalls
Firewalls serve as gatekeepers, monitoring and controlling incoming and outgoing network traffic based on predetermined security policies. A robust firewall can prevent malicious traffic from entering a network, thereby stopping ransomware at the gates.
While traditional firewalls focus on filtering traffic based on ports and protocols, modern “next-generation” firewalls go a step further. They inspect the content of traffic, looking for malicious patterns or signatures. By integrating with threat intelligence services, these firewalls can block known ransomware command and control servers, further enhancing protection.
Beyond Technology: The Human Element
No matter how advanced the technological defenses, the human element remains a potential vulnerability. Cybercriminals often exploit human psychology, using tactics like social engineering and phishing to deceive individuals into compromising security.
To address this, continuous training and awareness programs are essential. Employees should be educated about the latest threats and trained to recognize and report suspicious activities. Simulated phishing exercises can be beneficial, helping employees identify deceptive emails in a controlled environment. By fostering a culture of cybersecurity awareness, businesses can significantly reduce the risk of ransomware attacks.
Conclusion: Staying One Step Ahead
The world of cybersecurity is a constant game of cat and mouse. As defenses improve, attackers devise new methods to bypass them. However, by staying informed, proactive, and adopting a layered defense strategy, individuals and businesses can mitigate the risks posed by ransomware and stay one step ahead of cybercriminals.
FAQs
Malware is a general term used to describe any malicious software designed to harm or exploit devices, networks, or services. This includes viruses, worms, trojans, and spyware. Ransomware, on the other hand, is a specific type of malware that focuses on encrypting a victim’s files and demanding a ransom for their release. While all ransomware is malware, not all malware is ransomware.
The most evident sign of a ransomware infection is the inability to access your files, followed by a ransom note. This note typically provides instructions on how to pay the ransom and may include a countdown timer, adding pressure to the victim. Additionally, file extensions might change, or you might notice unusual network activity. If you suspect a ransomware infection, it’s crucial to act quickly, disconnect from the network, and seek professional help.
While it’s possible to remove the ransomware itself from a system, decrypting the affected files without the decryption key can be challenging. Some tools and resources can decrypt certain types of ransomware, especially if they use known encryption flaws. However, there’s no universal solution. The best approach is to restore from a backup, emphasizing the importance of regular and secure backups. Paying the ransom is risky and doesn’t guarantee file recovery.
Absolutely. While desktop computers and servers are primary targets, mobile devices, especially those running Android, have been targeted by ransomware. These attacks often come in the form of malicious apps downloaded from third-party app stores. It’s essential to only download apps from trusted sources and keep your device’s operating system updated to protect against known vulnerabilities.
Protecting a business from ransomware requires a combination of technological and human-centric strategies. Regularly back up critical data and store it offline. Ensure all software, including operating systems and applications, are updated to patch known vulnerabilities. Invest in advanced antivirus solutions and robust firewalls. Most importantly, conduct regular cybersecurity training for employees, emphasizing the importance of recognizing and reporting suspicious activities.