Today’s digital world faces many threats, one of which is the Csrss.exe Trojan virus. This guide focuses on helping you understand and remove this virus from your computer. The Csrss.exe Trojan disguises itself as a legitimate Windows process, making it hard to detect and dangerous for your system. It can steal personal information, slow down your computer, and give hackers access to your system.

The genuine Csrss.exe file is a critical part of Windows, responsible for many important tasks. However, the Trojan version is harmful and found in places other than the System32 folder where the real file is located. Knowing the difference between these two is key to keeping your computer safe.
In this guide, we will explain how the Csrss.exe Trojan gets into your system, how to spot it, and step-by-step instructions to get rid of it. Our goal is to give you the knowledge and tools you need to protect your computer against this type of threat. Let’s start by learning more about the Csrss.exe Trojan virus and how it can affect your computer.
Understanding Csrss.exe Trojan Virus
What is the Csrss.exe File?
The Client Server Runtime Process, commonly known as CSRSS.exe, plays a pivotal role in the functioning of Windows operating systems. It handles essential tasks, particularly those related to the graphical interface such as managing the console windows and the shutdown process. The significance of CSRSS.exe in the Windows environment cannot be overstated, as it is integral to the stability and smooth operation of the system.
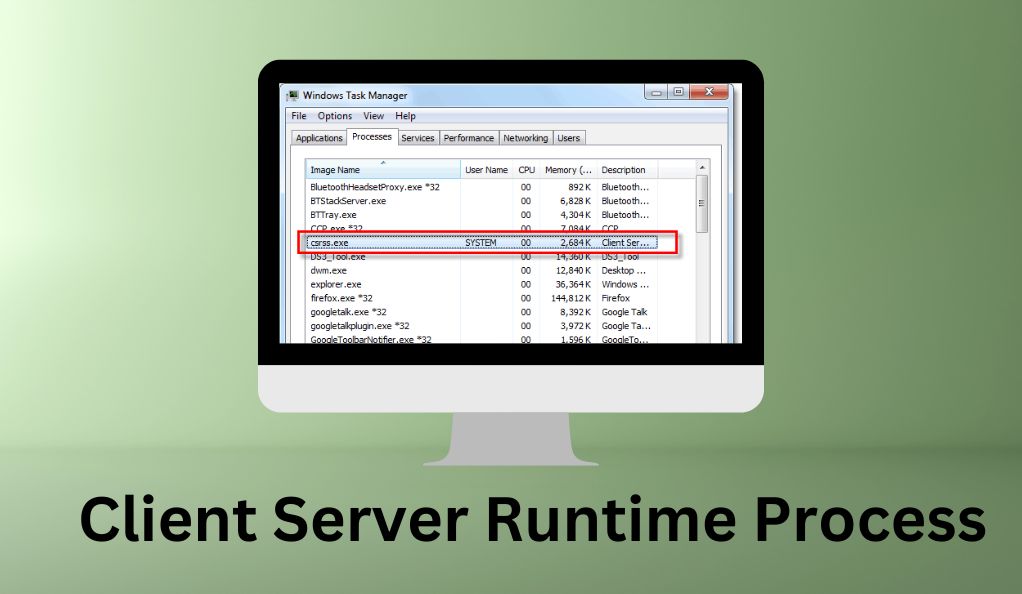
Legitimate vs. Trojan Variant
The challenge arises in distinguishing the legitimate CSRSS.exe file from its malicious twin, the Trojan virus. The genuine CSRSS.exe file is located in the System32 folder within the Windows directory and is a critical system file. Any attempts to delete or modify this file can lead to system instability or failure.
In contrast, the Trojan variant of CSRSS.exe is a piece of malware that often installs itself in various locations outside the System32 folder. This malicious version poses as the legitimate CSRSS.exe to avoid detection by users and antivirus programs. It is notorious for its harmful activities, which include stealing sensitive information, severely affecting system performance, and potentially allowing unauthorized access to the user’s system.
Understanding the difference between these two variants is essential for maintaining system security. The genuine CSRSS.exe file is an integral part of the Windows operating system, required for its normal functioning, while the Trojan variant is a harmful impostor that must be identified and removed promptly.
How Csrss.exe Trojan Enters Your System
The Csrss.exe Trojan is a cunning piece of malware that finds numerous ways to infiltrate computers. Understanding these methods is crucial for effectively guarding your system against this stealthy invader.
Common Methods of Infection
- Bundled Software: One of the most common ways the Csrss.exe Trojan enters your system is through bundled software. Often, free software or applications downloaded from the internet come with hidden extras. This Trojan hides within these bundles and installs itself alongside the primary software, usually without the user’s knowledge or consent.
- Infected Emails: Email remains a popular method for spreading malware. Cybercriminals craft emails with malicious attachments or embedded links. When these attachments are opened or links clicked, the Trojan is silently installed onto your computer. These emails can be very deceptive, often appearing legitimate or coming from familiar sources.
- Malicious Ads and Pop-Ups: While browsing the internet, you might encounter pop-up ads or banners that, when clicked, can initiate the download of the Csrss.exe Trojan. These ads are often found on less secure or compromised websites and can be very convincing or enticing.
- Peer-to-Peer Networks: Downloading files from peer-to-peer sharing platforms like torrent sites is another common way this Trojan spreads. These networks are notorious for harboring infected files, as there is little to no regulation of the content shared.
- Other Infected Devices: Connecting devices like USB drives, external hard drives, or even smartphones that are already infected with the Trojan can introduce it to your system. The malware uses these devices as a bridge to jump from one system to another.
- Exploiting System Vulnerabilities: Sometimes, the Trojan takes advantage of unpatched vulnerabilities in your operating system or software. Keeping your system and applications up-to-date is crucial to prevent this type of attack.
Identifying the Csrss.exe Trojan Virus
Detecting the presence of the Csrss.exe Trojan on your computer is a critical step in the removal process. This section outlines how to spot this deceptive malware.

Verifying the Presence of a Fake CSRSS.exe File
1. Check the File Location:
- The legitimate CSRSS.exe file is always located in the C:\Windows\System32 directory.
- If you find a CSRSS.exe file in any other location, it’s likely a Trojan.
2. Using Task Manager:
- Open Task Manager by pressing Ctrl + Shift + Esc.
- Navigate to the “Processes” tab and look for CSRSS.exe or Client Server Runtime Subsystem.
- Right-click on it and select “Open File Location.” If it takes you anywhere other than the System32 folder, it’s a red flag.
- Additionally, if you try to end the process and Windows shows a warning box, it’s likely the legitimate process. If there’s no warning, it could be the Trojan.
3. System Performance Issues:
- Unusual system behavior like slow performance, frequent crashes, or unexpected ads can be signs of the Trojan.
4. Use Antivirus Software:
- Run a full system scan with your antivirus software. Most antivirus programs are equipped to identify and flag suspicious files like the CSRSS.exe Trojan.
Step-by-Step Guide to Removing the Csrss.exe Trojan
Removing the Csrss.exe Trojan virus from your computer involves a careful approach to ensure complete eradication of the threat. This guide will walk you through the necessary steps, focusing on methodical actions rather than a simple list of tasks.
Preliminary Check: Confirm if CSRSS.exe is Malicious
Before proceeding with removal steps, it’s crucial to confirm whether the CSRSS.exe file is indeed malicious. Begin by using the Task Manager to locate the CSRSS.exe process. Right-click on it and choose ‘Open File Location’. If the file is located anywhere other than the System32 folder, it’s a sign of the Trojan. Additionally, running a full system scan with reliable antivirus software can help identify whether the CSRSS.exe file is a threat.
Step 1: Identify and Isolate the Threat
The first step in the removal process is to restart your computer in Safe Mode. This action prevents the Trojan from running and makes it easier to remove. Disconnecting your computer from the internet is also advised. This step is crucial as it prevents the Trojan from communicating with any external servers. If possible, backing up your important files to an external drive or cloud storage is a good idea, but be careful not to include any potentially infected files.
Step 2: Remove the CSRSS.exe Trojan
The primary method for removing the Trojan is to use a comprehensive antivirus program to run a full system scan. This software will typically detect and remove the threat. However, if the antivirus fails to eliminate the Trojan, you may need to manually intervene. This involves locating the malicious CSRSS.exe file outside the System32 directory and deleting it. Additionally, cleaning the registry to remove any related entries is recommended, but caution is advised as incorrect changes to the registry can be detrimental to your system.
Step 3: Reset Browser Settings and Remove Temporary Files
After dealing with the Trojan, resetting your web browsers to their default settings is important as it helps remove any changes or extensions the malware might have installed. Alongside this, deleting temporary files from your system can help eliminate any remnants of the infection. You can use tools like the Disk Cleanup utility to assist with this task.
Step 4: Final Steps and Prevention
Once these steps are completed, reboot your computer in normal mode and conduct another full system scan to ensure all traces of the Trojan are removed. It’s also essential to keep your operating system and software updated with the latest security patches. Regular scans with your antivirus software can help maintain your system’s security and prevent future infections.
Preventive Measures
After removing the Csrss.exe Trojan, it’s crucial to implement strategies to prevent future infections. By adopting these preventive measures, you can significantly reduce the risk of encountering similar threats.

1. Keeping Software and Operating System Updated
Regular updates are essential for the security of your system. Software developers frequently release updates to patch vulnerabilities that could be exploited by malware like the Csrss.exe Trojan. Ensure your operating system and all installed software are up-to-date with the latest security patches. This can often be automated within the settings of your operating system and individual applications.
2. Safe Downloading Practices
The origin of your downloads plays a crucial role in system safety. Always download software from official and trustworthy websites. Avoid third-party downloaders, unofficial sites, or peer-to-peer networks, as these are common sources of malware. Be particularly cautious with free software, as it may bundle unwanted applications or Trojans.
3. Email Vigilance
Emails are a common method for distributing malware. Be cautious with emails from unknown senders, especially those with attachments or links. Verify the authenticity of the sender and the relevance of the email before opening any attachments or clicking on links. Implementing spam filters and using email services with good security features can also help reduce the risk of malicious emails.
4. Regular Antivirus Scans
Having a reputable antivirus or anti-malware software installed and keeping it updated is vital. Regular scans can detect and remove malicious software before it causes harm. Most antivirus programs offer real-time protection, scanning new files as they are downloaded or created, and monitoring system behavior for signs of malware.
5. Backup Important Data
Regularly backing up important data can save you from losing critical information in the event of a malware attack. Use external drives or cloud storage solutions to keep copies of your important files. However, ensure that you’re not backing up any infected files.
6. Be Wary of External Devices
Infected external devices like USB drives can introduce malware into your system. Always scan such devices with antivirus software before accessing their contents. Avoid using unknown or untrusted external devices.
Conclusion
Navigating through the process of identifying and removing the Csrss.exe Trojan virus is a critical step in ensuring your computer’s safety. This experience underscores the importance of cybersecurity in our increasingly digital world. By understanding the risks, recognizing the signs of infection, and knowing the steps to effectively remove threats, you become more equipped to protect your digital life. Moreover, this journey highlights the need for continual vigilance and education in cybersecurity. As cyber threats evolve, staying informed and proactive is essential for maintaining the security of your computer systems. Remember, effective cybersecurity is an ongoing commitment to safeguarding your digital footprint.








